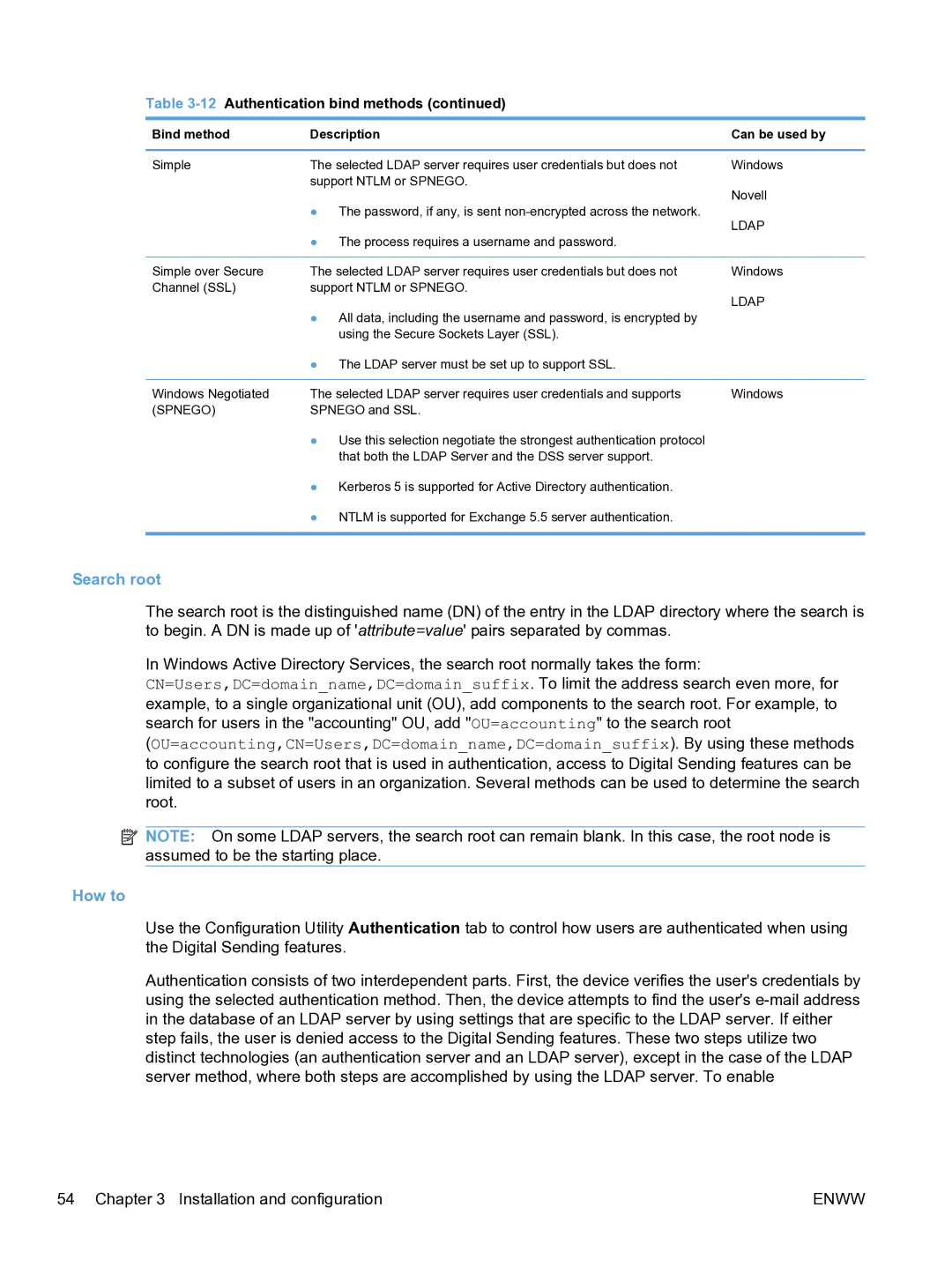
Table 3-12 Authentication bind methods (continued)
Bind method | Description | Can be used by |
|
|
|
Simple | The selected LDAP server requires user credentials but does not | Windows |
| support NTLM or SPNEGO. | Novell |
| ● The password, if any, is sent | |
| LDAP | |
| ● The process requires a username and password. | |
|
| |
|
|
|
Simple over Secure | The selected LDAP server requires user credentials but does not | Windows |
Channel (SSL) | support NTLM or SPNEGO. | LDAP |
| ● All data, including the username and password, is encrypted by | |
|
| |
| using the Secure Sockets Layer (SSL). |
|
| ● The LDAP server must be set up to support SSL. |
|
|
|
|
Windows Negotiated | The selected LDAP server requires user credentials and supports | Windows |
(SPNEGO) | SPNEGO and SSL. |
|
| ● Use this selection negotiate the strongest authentication protocol |
|
| that both the LDAP Server and the DSS server support. |
|
| ● Kerberos 5 is supported for Active Directory authentication. |
|
| ● NTLM is supported for Exchange 5.5 server authentication. |
|
|
|
|
Search root
The search root is the distinguished name (DN) of the entry in the LDAP directory where the search is to begin. A DN is made up of 'attribute=value' pairs separated by commas.
In Windows Active Directory Services, the search root normally takes the form: CN=Users,DC=domain_name,DC=domain_suffix. To limit the address search even more, for example, to a single organizational unit (OU), add components to the search root. For example, to search for users in the "accounting" OU, add "OU=accounting" to the search root (OU=accounting,CN=Users,DC=domain_name,DC=domain_suffix). By using these methods to configure the search root that is used in authentication, access to Digital Sending features can be limited to a subset of users in an organization. Several methods can be used to determine the search root.
![]() NOTE: On some LDAP servers, the search root can remain blank. In this case, the root node is assumed to be the starting place.
NOTE: On some LDAP servers, the search root can remain blank. In this case, the root node is assumed to be the starting place.
How to
Use the Configuration Utility Authentication tab to control how users are authenticated when using the Digital Sending features.
Authentication consists of two interdependent parts. First, the device verifies the user's credentials by using the selected authentication method. Then, the device attempts to find the user's
54 Chapter 3 Installation and configuration | ENWW |