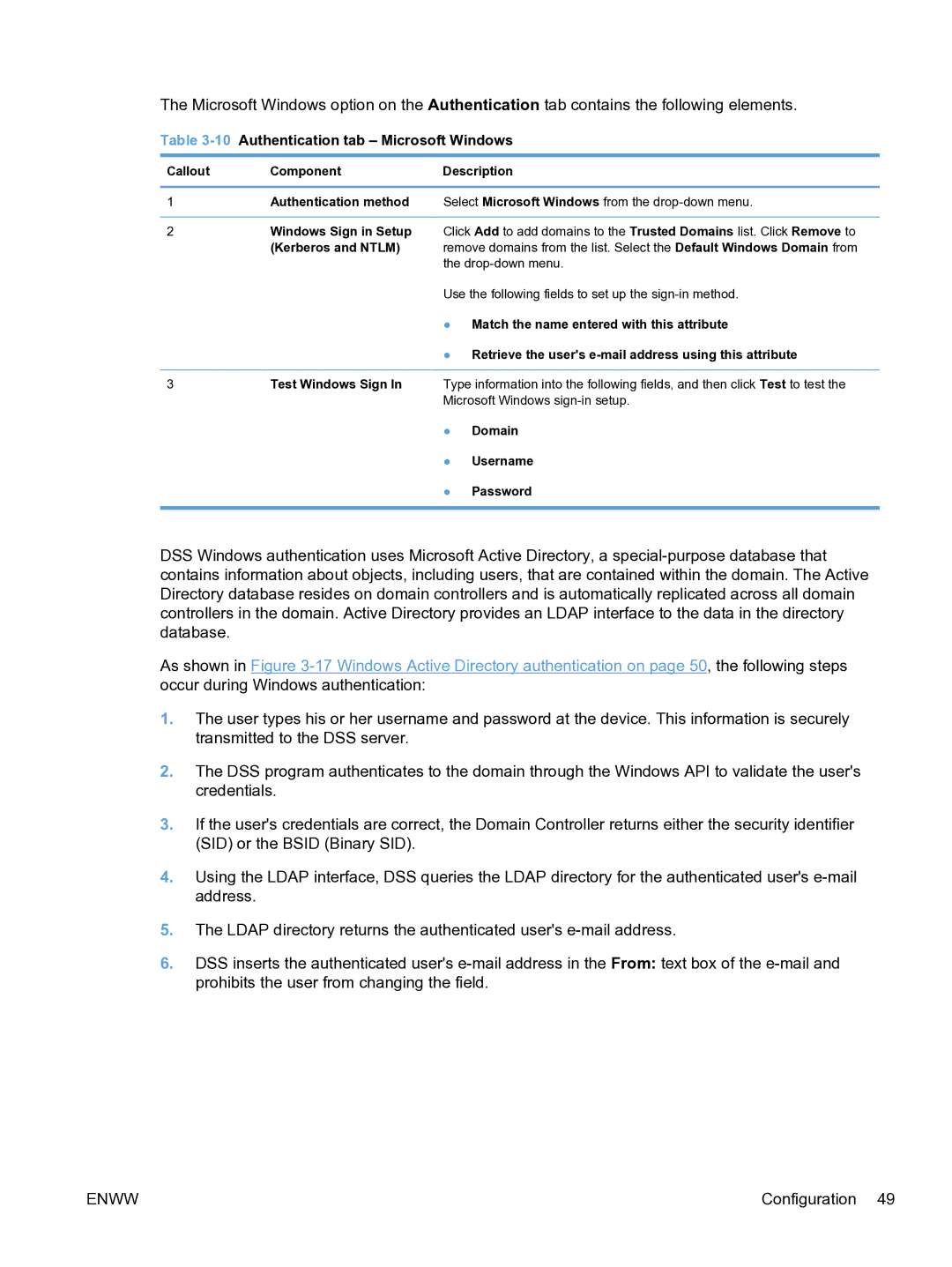
The Microsoft Windows option on the Authentication tab contains the following elements.
Table 3-10 Authentication tab – Microsoft Windows
Callout | Component | Description |
|
|
|
1 | Authentication method | Select Microsoft Windows from the |
2Windows Sign in Setup Click Add to add domains to the Trusted Domains list. Click Remove to
(Kerberos and NTLM) remove domains from the list. Select the Default Windows Domain from the
Use the following fields to set up the
●Match the name entered with this attribute
●Retrieve the user's
3Test Windows Sign In Type information into the following fields, and then click Test to test the Microsoft Windows
●Domain
●Username
●Password
DSS Windows authentication uses Microsoft Active Directory, a
As shown in Figure
1.The user types his or her username and password at the device. This information is securely transmitted to the DSS server.
2.The DSS program authenticates to the domain through the Windows API to validate the user's credentials.
3.If the user's credentials are correct, the Domain Controller returns either the security identifier (SID) or the BSID (Binary SID).
4.Using the LDAP interface, DSS queries the LDAP directory for the authenticated user's
5.The LDAP directory returns the authenticated user's
6.DSS inserts the authenticated user's
ENWW | Configuration 49 |