Setting Up Security for a Device
Operating Notes for Port Security
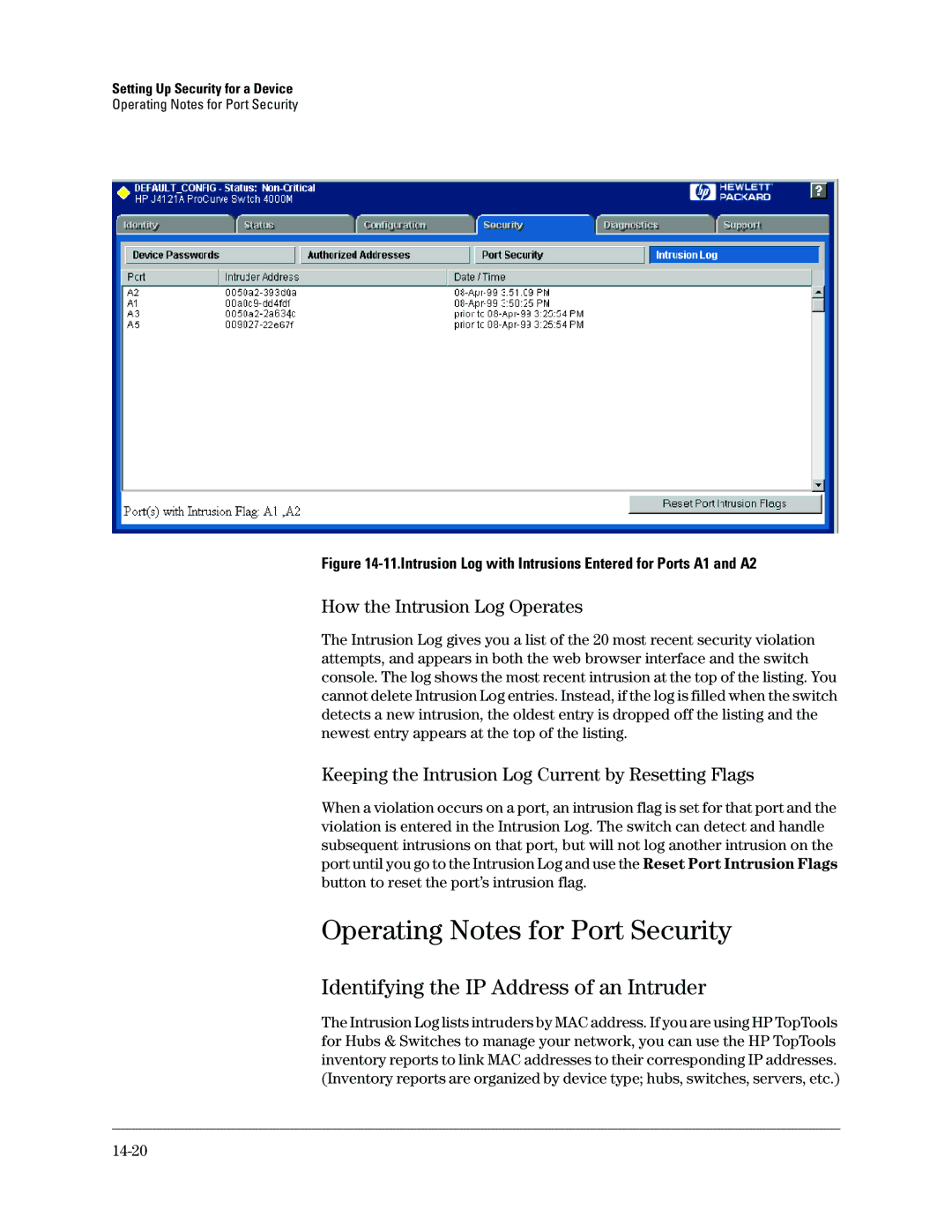
Figure 14-11.Intrusion Log with Intrusions Entered for Ports A1 and A2
How the Intrusion Log Operates
The Intrusion Log gives you a list of the 20 most recent security violation attempts, and appears in both the web browser interface and the switch console. The log shows the most recent intrusion at the top of the listing. You cannot delete Intrusion Log entries. Instead, if the log is filled when the switch detects a new intrusion, the oldest entry is dropped off the listing and the newest entry appears at the top of the listing.
Keeping the Intrusion Log Current by Resetting Flags
When a violation occurs on a port, an intrusion flag is set for that port and the violation is entered in the Intrusion Log. The switch can detect and handle subsequent intrusions on that port, but will not log another intrusion on the port until you go to the Intrusion Log and use the Reset Port Intrusion Flags button to reset the port’s intrusion flag.
Operating Notes for Port Security
Identifying the IP Address of an Intruder
The Intrusion Log lists intruders by MAC address. If you are using HP TopTools for Hubs & Switches to manage your network, you can use the HP TopTools inventory reports to link MAC addresses to their corresponding IP addresses. (Inventory reports are organized by device type; hubs, switches, servers, etc.)