McAfee® Host Intrusion Prevention 6.1 Product Guide | IPS Policies |
| Configuring the IPS Protection policy |
4
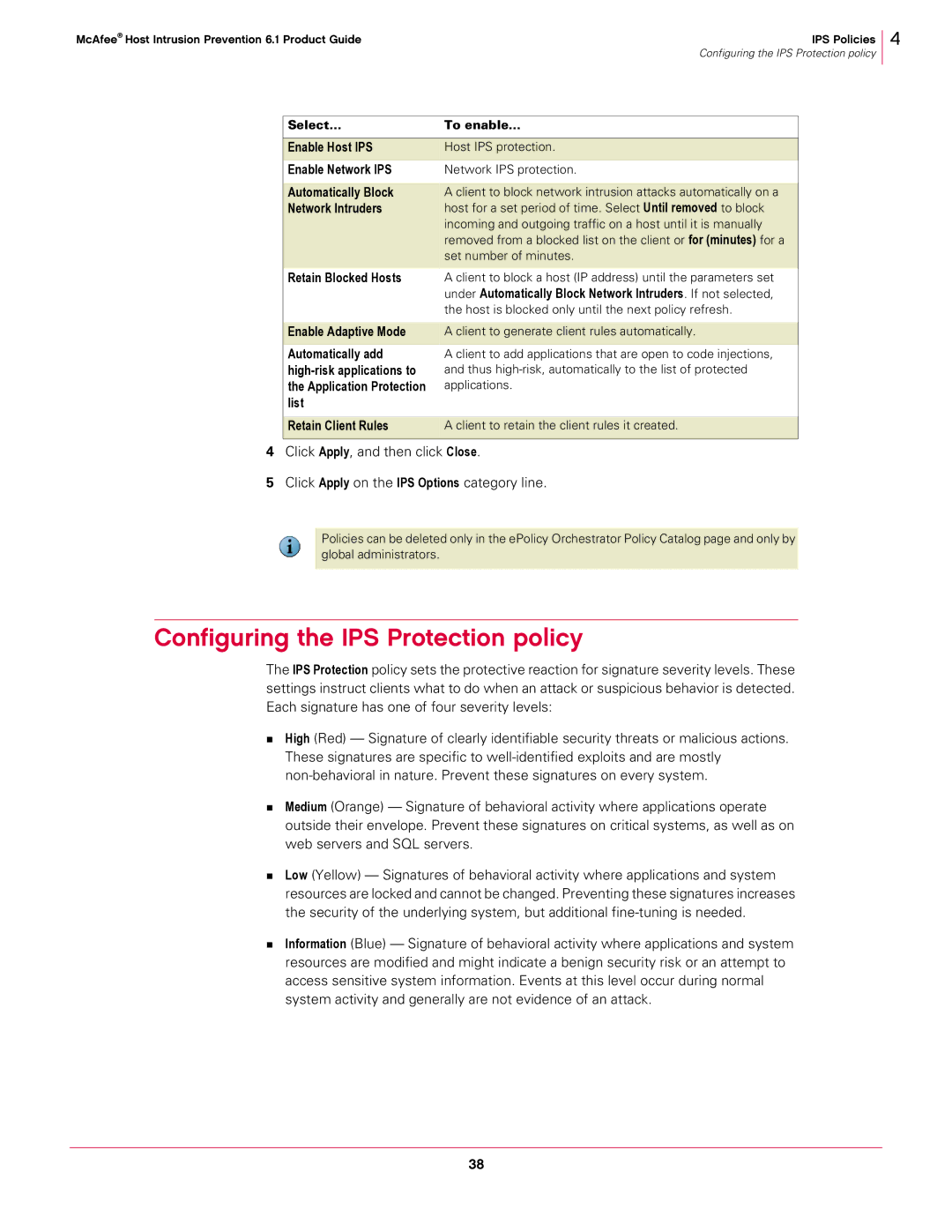
Select... | To enable... |
|
|
Enable Host IPS | Host IPS protection. |
Enable Network IPS | Network IPS protection. |
|
|
Automatically Block | A client to block network intrusion attacks automatically on a |
Network Intruders | host for a set period of time. Select Until removed to block |
| incoming and outgoing traffic on a host until it is manually |
| removed from a blocked list on the client or for (minutes) for a |
| set number of minutes. |
|
|
Retain Blocked Hosts | A client to block a host (IP address) until the parameters set |
| under Automatically Block Network Intruders. If not selected, |
| the host is blocked only until the next policy refresh. |
|
|
Enable Adaptive Mode | A client to generate client rules automatically. |
Automatically add | A client to add applications that are open to code injections, |
and thus | |
the Application Protection | applications. |
list |
|
|
|
Retain Client Rules | A client to retain the client rules it created. |
|
|
4Click Apply, and then click Close.
5Click Apply on the IPS Options category line.
Policies can be deleted only in the ePolicy Orchestrator Policy Catalog page and only by global administrators.
Configuring the IPS Protection policy
The IPS Protection policy sets the protective reaction for signature severity levels. These settings instruct clients what to do when an attack or suspicious behavior is detected. Each signature has one of four severity levels:
High (Red) — Signature of clearly identifiable security threats or malicious actions. These signatures are specific to
Medium (Orange) — Signature of behavioral activity where applications operate outside their envelope. Prevent these signatures on critical systems, as well as on web servers and SQL servers.
Low (Yellow) — Signatures of behavioral activity where applications and system resources are locked and cannot be changed. Preventing these signatures increases the security of the underlying system, but additional
Information (Blue) — Signature of behavioral activity where applications and system resources are modified and might indicate a benign security risk or an attempt to access sensitive system information. Events at this level occur during normal system activity and generally are not evidence of an attack.
38