McAfee® Host Intrusion Prevention 6.1 Product Guide | IPS Policies |
| IPS Events |
4
From the list of events generated, you can determine which events are allowable and which indicate suspicious behavior. To allow events, configure the system with the following:
Exceptions — which are rules that override a signature rule. To create an exception specific to the event, see Creating and applying Trusted Applications policies on page 112.
Trusted Applications — which allow internal applications whose operations may be blocked by a signature. To create a trusted application specific to the event, see Creating and applying Trusted Applications policies on page 112).
This
Viewing events
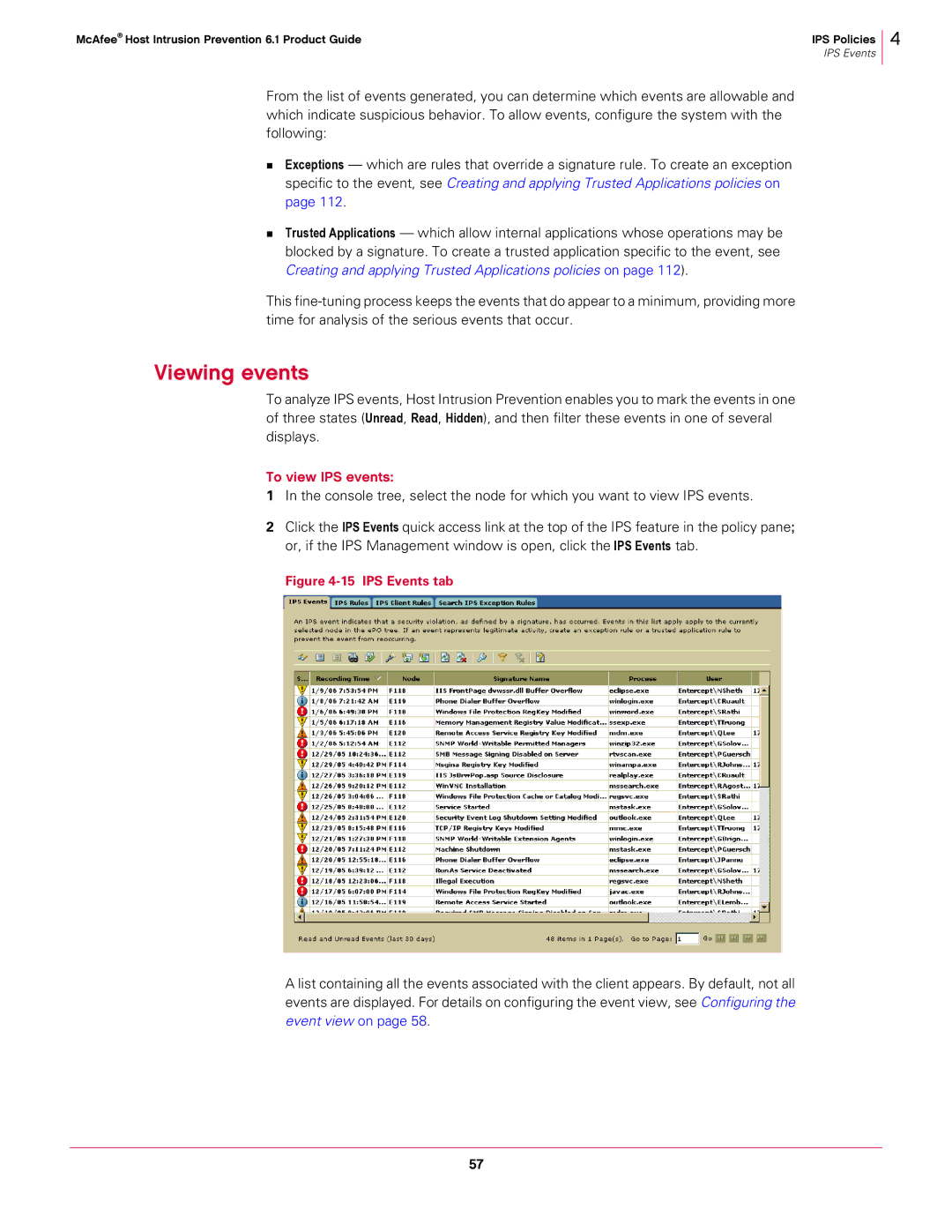
To analyze IPS events, Host Intrusion Prevention enables you to mark the events in one of three states (Unread, Read, Hidden), and then filter these events in one of several displays.
To view IPS events:
1In the console tree, select the node for which you want to view IPS events.
2Click the IPS Events quick access link at the top of the IPS feature in the policy pane; or, if the IPS Management window is open, click the IPS Events tab.
Figure 4-15 IPS Events tab
A list containing all the events associated with the client appears. By default, not all events are displayed. For details on configuring the event view, see Configuring the event view on page 58.
57