McAfee® Host Intrusion Prevention 6.1 Product Guide | IPS Policies |
| IPS Rules policy details |
4
Application Protection Rules
Application Protection Rules alleviate compatibility and stability issues involving process hooking. It permits or blocks
Host Intrusion Prevention provides a static list of processes that are permitted or blocked. This list is updated with content update releases. In addition, processes that are permitted to hook can be added dynamically to the list when process analysis is enabled. This analysis is performed:
Each time the client is started and running processes are enumerated.
Each time a process starts.
Each time the process monitoring list is updated by the ePolicy Orchestrator server.
Each time the list of processes that listen on a network port is updated.
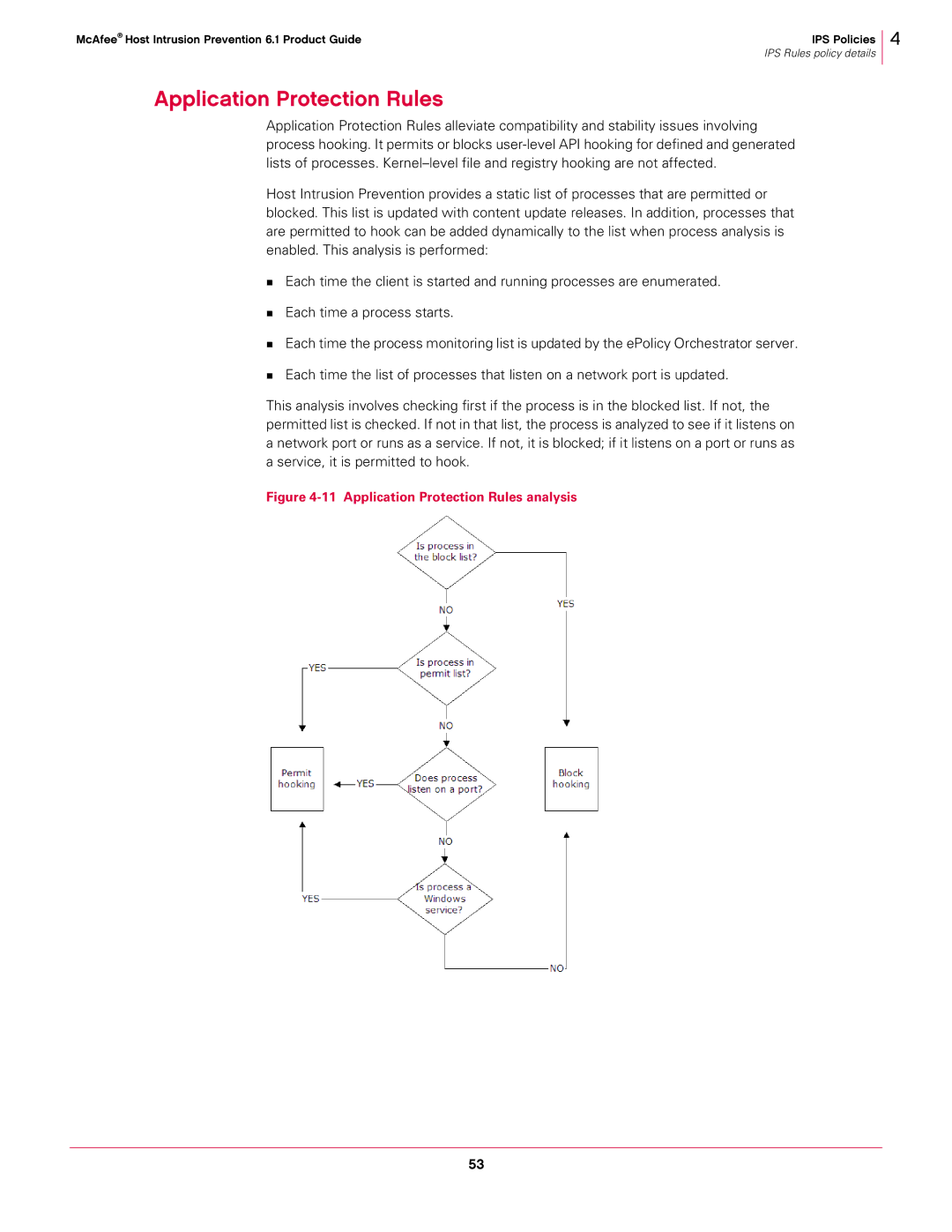
This analysis involves checking first if the process is in the blocked list. If not, the permitted list is checked. If not in that list, the process is analyzed to see if it listens on a network port or runs as a service. If not, it is blocked; if it listens on a port or runs as a service, it is permitted to hook.
Figure 4-11 Application Protection Rules analysis
53