GS716Tv2 and GS724Tv3 Software Administration Manual
The Profile Summary table shows the rules that are configured for the profile, as the following table describes.
Field | Description | |
Rule Type | Identifies the action the rule takes, which is either Permit or Deny. | |
|
| |
Service Type | Displays the type of service to allow or prohibit from accessing the switch | |
| management interface: | |
| • | SNMP |
| • | HTTP |
| • | HTTPS |
Source IP Address | Displays the IP Address of the client that may or may not originate | |
| management traffic. | |
|
| |
Mask | Displays the subnet mask associated with the IP address. | |
|
| |
Priority | Displays the priority of the rule. The rules are validated against the incoming | |
| management request in the ascending order of their priorities. If a rule | |
| matches, action is performed and subsequent rules below are ignored. | |
|
|
|
Click Refresh to update the page with the most current information.
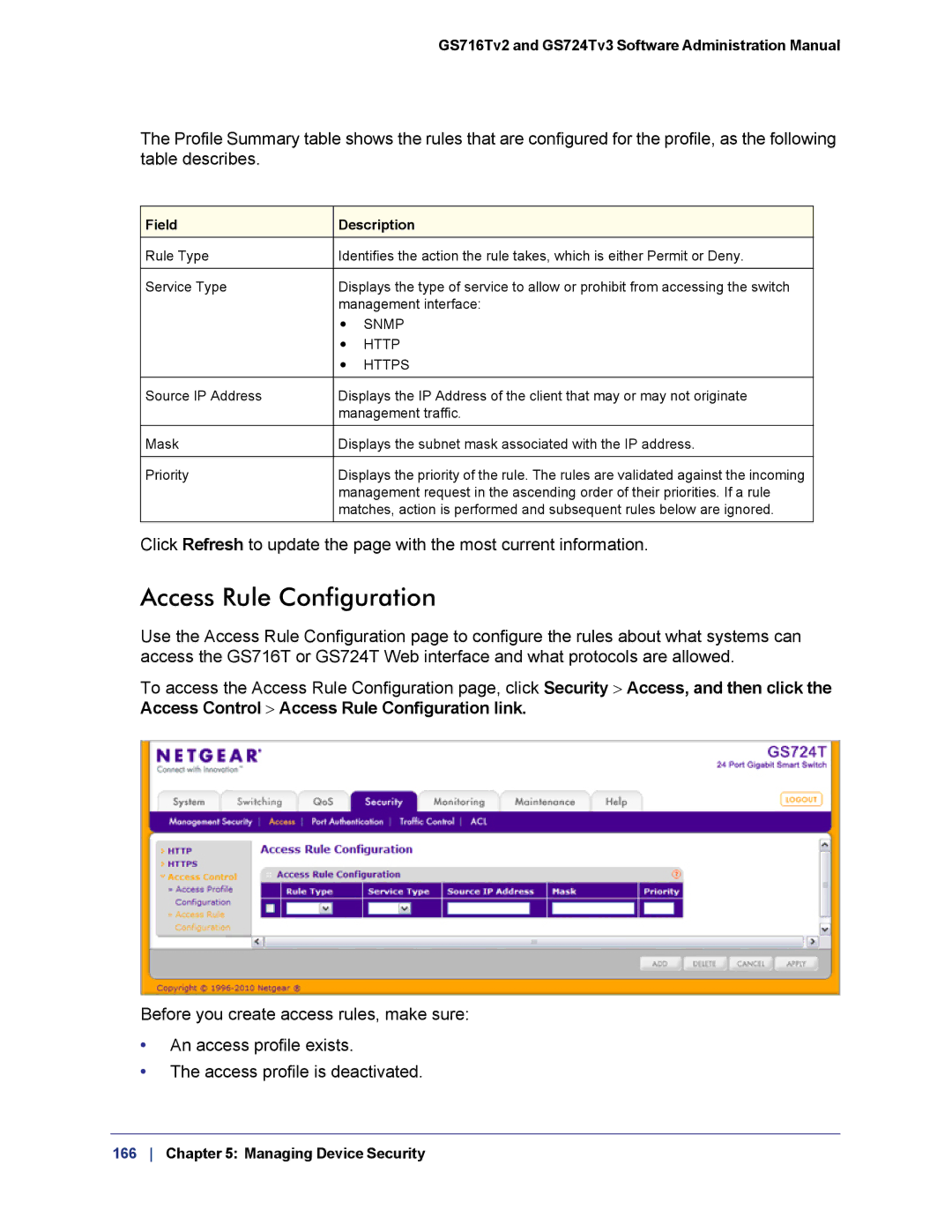
Access Rule Configuration
Use the Access Rule Configuration page to configure the rules about what systems can access the GS716T or GS724T Web interface and what protocols are allowed.
To access the Access Rule Configuration page, click Security > Access, and then click the Access Control > Access Rule Configuration link.
Before you create access rules, make sure:
•An access profile exists.
•The access profile is deactivated.
166 Chapter 5: Managing Device Security