Designing Access Controls
Comprehensive Security Policy
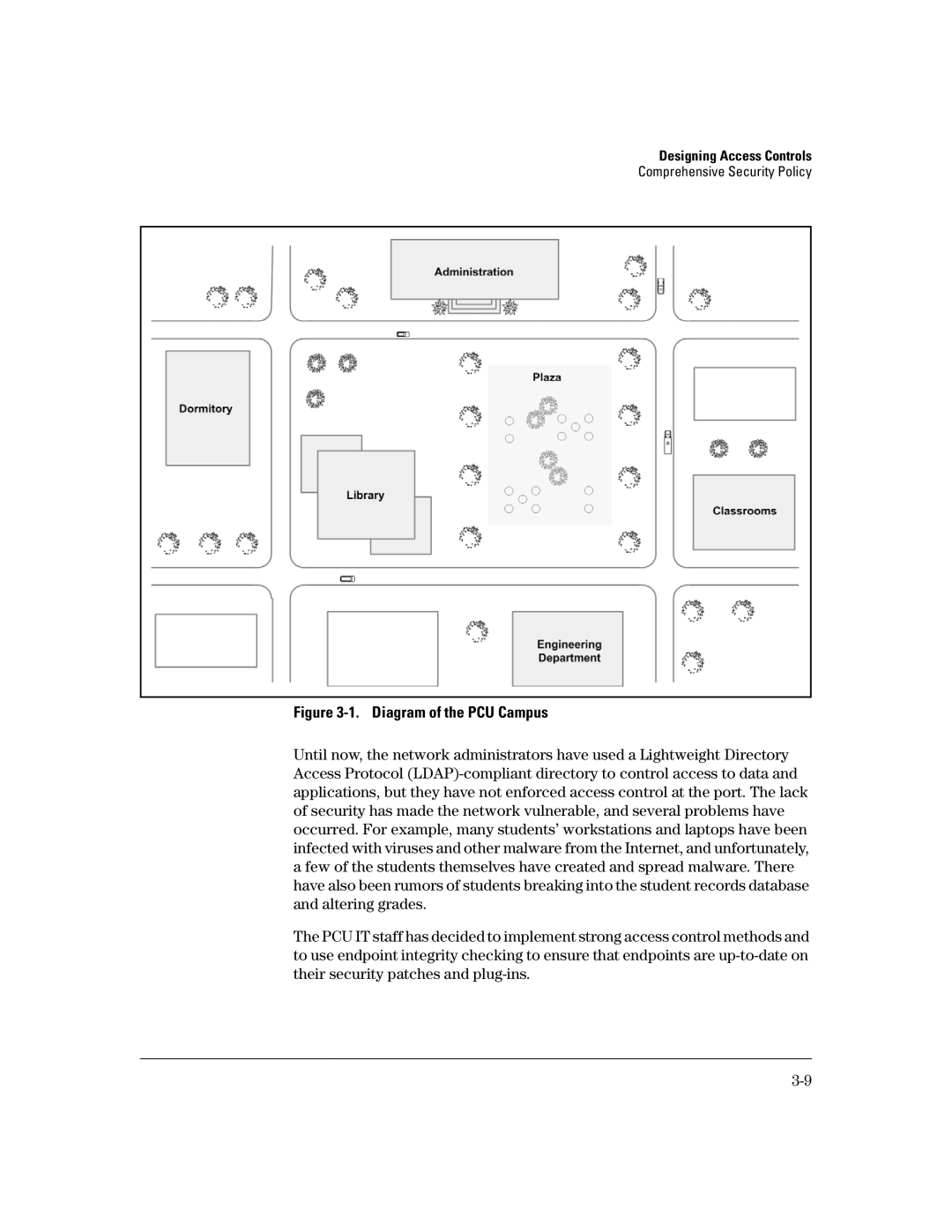
Figure 3-1. Diagram of the PCU Campus
Until now, the network administrators have used a Lightweight Directory Access Protocol
The PCU IT staff has decided to implement strong access control methods and to use endpoint integrity checking to ensure that endpoints are