Designing Access Controls
Make Decisions about Remote Access (VPN)
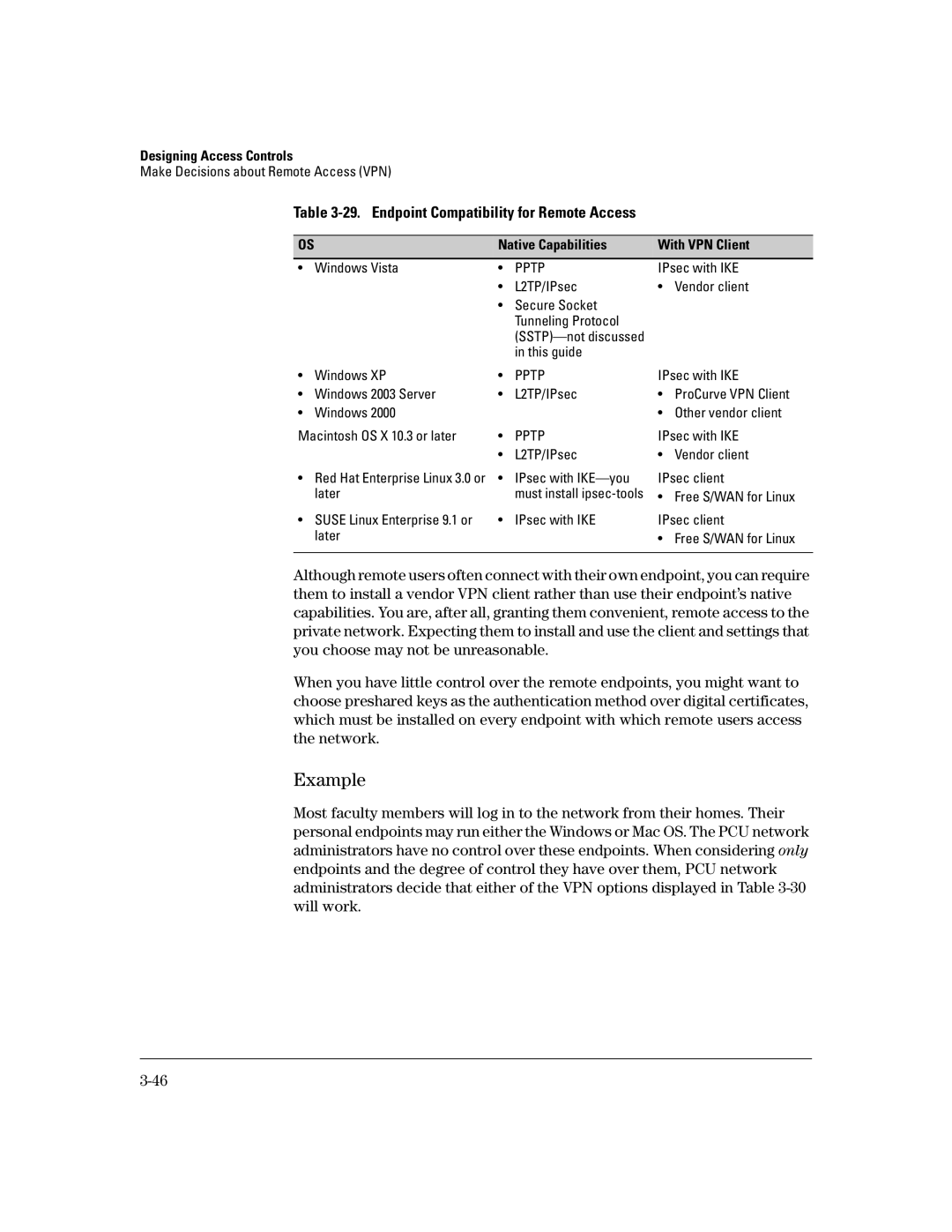
Table 3-29. Endpoint Compatibility for Remote Access
OS |
| Native Capabilities | With VPN Client | ||
• | Windows Vista | • | PPTP | IPsec with IKE | |
|
| • | L2TP/IPsec | • | Vendor client |
|
| • | Secure Socket |
|
|
|
|
| Tunneling Protocol |
|
|
|
|
|
|
| |
|
|
| in this guide |
|
|
• | Windows XP | • | PPTP | IPsec with IKE | |
• | Windows 2003 Server | • | L2TP/IPsec | • | ProCurve VPN Client |
• | Windows 2000 |
|
| • | Other vendor client |
Macintosh OS X 10.3 or later | • | PPTP | IPsec with IKE | ||
|
| • | L2TP/IPsec | • | Vendor client |
• Red Hat Enterprise Linux 3.0 or | • | IPsec with | IPsec client | ||
| later |
| must install | • Free S/WAN for Linux | |
• SUSE Linux Enterprise 9.1 or | • | IPsec with IKE | IPsec client | ||
| later |
|
| • Free S/WAN for Linux | |
|
|
|
|
|
|
Although remote users often connect with their own endpoint, you can require them to install a vendor VPN client rather than use their endpoint’s native capabilities. You are, after all, granting them convenient, remote access to the private network. Expecting them to install and use the client and settings that you choose may not be unreasonable.
When you have little control over the remote endpoints, you might want to choose preshared keys as the authentication method over digital certificates, which must be installed on every endpoint with which remote users access the network.
Example
Most faculty members will log in to the network from their homes. Their personal endpoints may run either the Windows or Mac OS. The PCU network administrators have no control over these endpoints. When considering only endpoints and the degree of control they have over them, PCU network administrators decide that either of the VPN options displayed in Table