Designing Access Controls
Choose the Access Control Methods
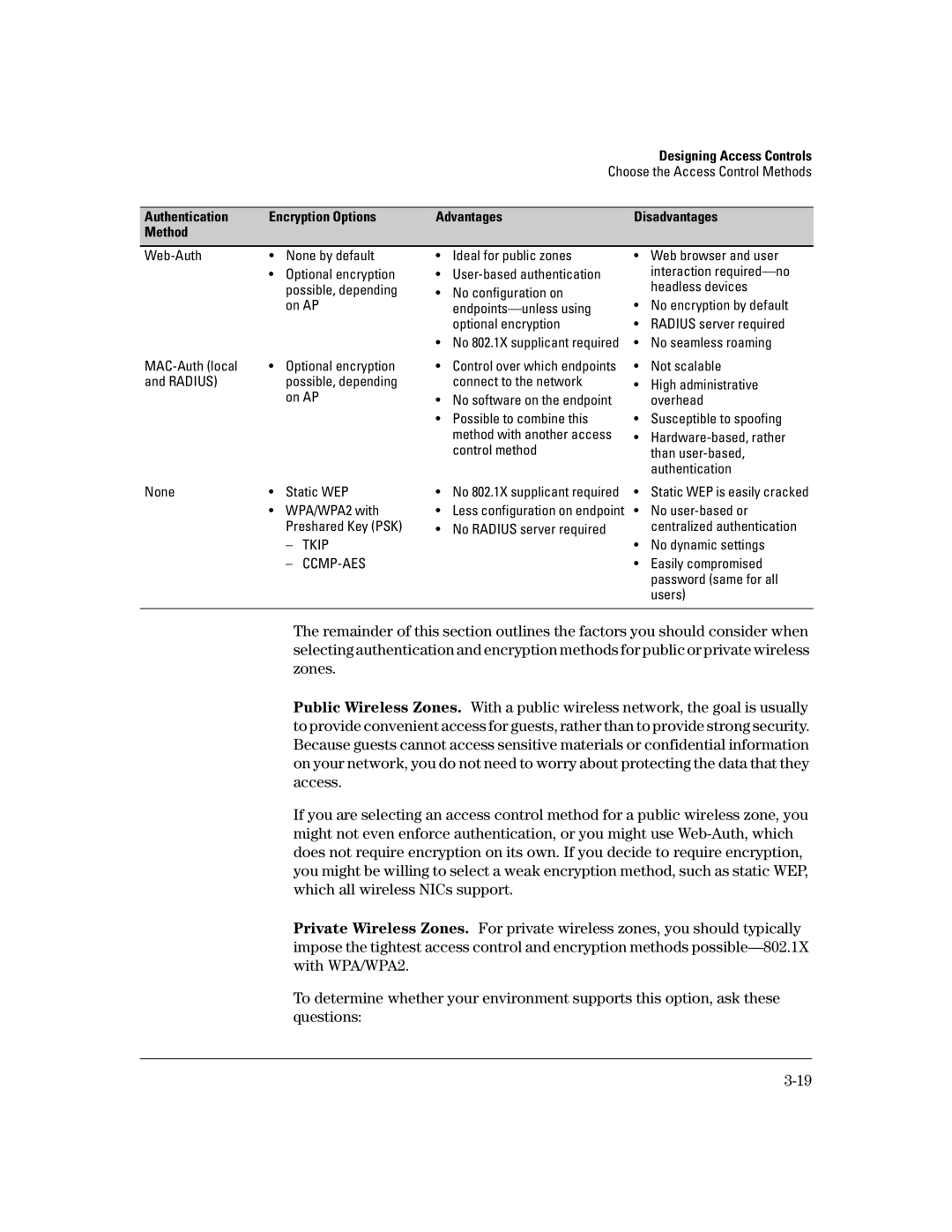
Authentication | Encryption Options | Advantages | Disadvantages |
Method |
|
|
|
|
|
|
|
| • | None by default |
| • | Optional encryption |
|
| possible, depending |
|
| on AP |
• | Optional encryption | |
and RADIUS) |
| possible, depending |
|
| on AP |
•Ideal for public zones
•User-based authentication
•No configuration on
•No 802.1X supplicant required
•Control over which endpoints connect to the network
•No software on the endpoint
•Possible to combine this method with another access control method
•Web browser and user interaction
•No encryption by default
•RADIUS server required
•No seamless roaming
•Not scalable
•High administrative overhead
•Susceptible to spoofing
•
None | • | Static WEP | |
| • | WPA/WPA2 with | |
|
| Preshared Key (PSK) | |
|
| – | TKIP |
|
| – | |
• No 802.1X supplicant required | • | Static WEP is easily cracked |
• Less configuration on endpoint | • | No |
• No RADIUS server required |
| centralized authentication |
| • | No dynamic settings |
| • | Easily compromised |
|
| password (same for all |
|
| users) |
The remainder of this section outlines the factors you should consider when selecting authentication and encryption methods for public or private wireless zones.
Public Wireless Zones. With a public wireless network, the goal is usually to provide convenient access for guests, rather than to provide strong security. Because guests cannot access sensitive materials or confidential information on your network, you do not need to worry about protecting the data that they access.
If you are selecting an access control method for a public wireless zone, you might not even enforce authentication, or you might use
Private Wireless Zones. For private wireless zones, you should typically impose the tightest access control and encryption methods
To determine whether your environment supports this option, ask these questions: