Access Control Concepts
Network Access Control Technologies
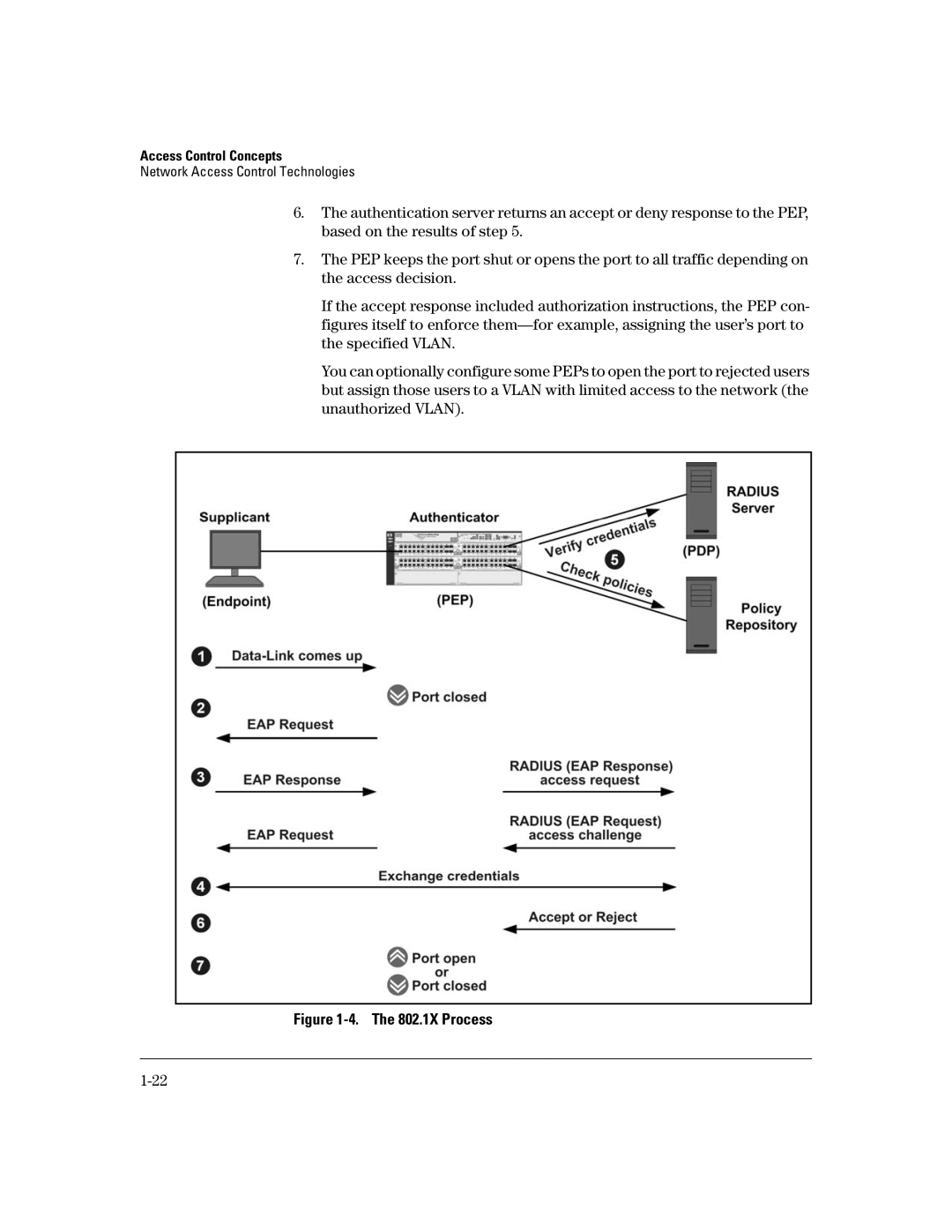
6.The authentication server returns an accept or deny response to the PEP, based on the results of step 5.
7.The PEP keeps the port shut or opens the port to all traffic depending on the access decision.
If the accept response included authorization instructions, the PEP con- figures itself to enforce
You can optionally configure some PEPs to open the port to rejected users but assign those users to a VLAN with limited access to the network (the unauthorized VLAN).