Access Control Concepts
Network Access Control Technologies
Network Access Control Process
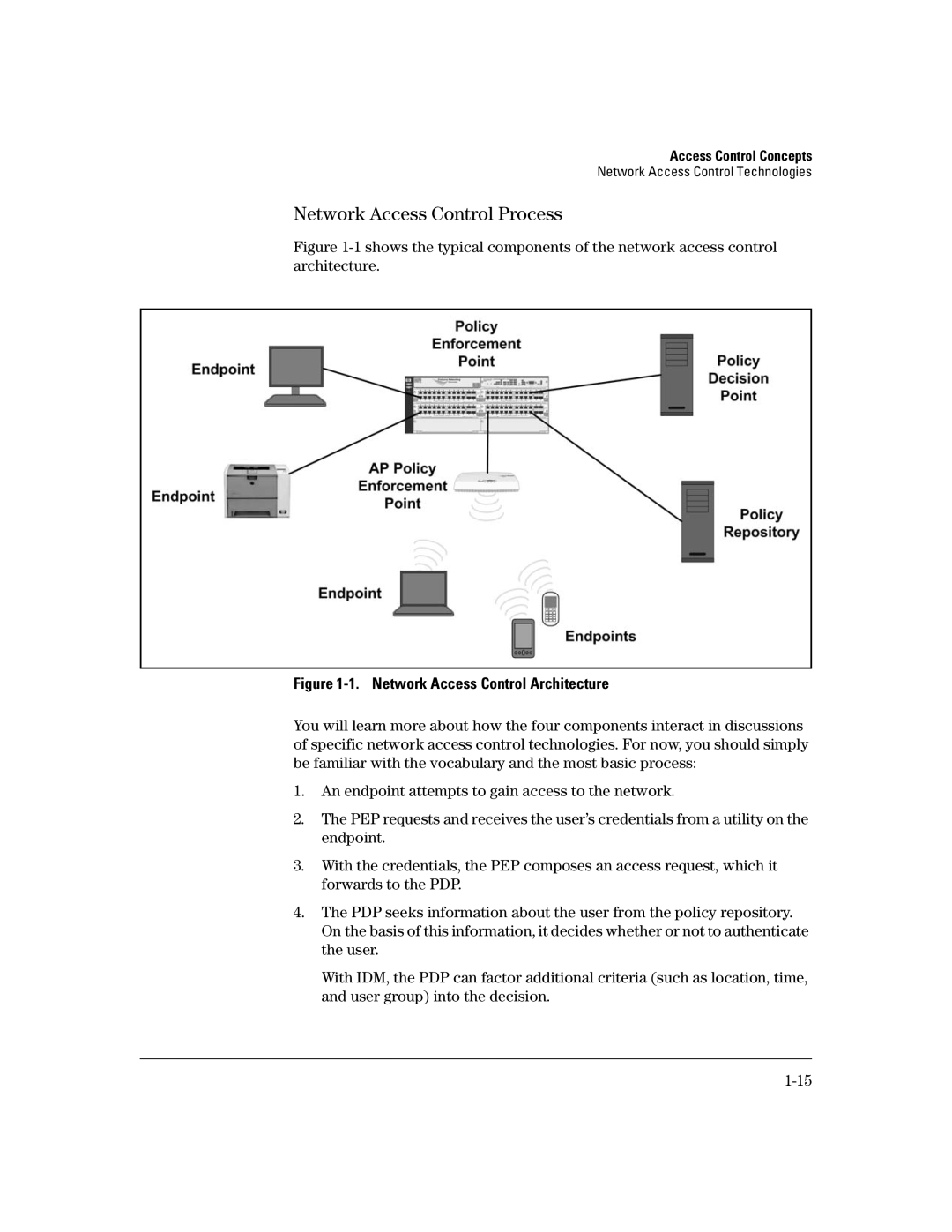
Figure 1-1 shows the typical components of the network access control architecture.
Figure 1-1. Network Access Control Architecture
You will learn more about how the four components interact in discussions of specific network access control technologies. For now, you should simply be familiar with the vocabulary and the most basic process:
1.An endpoint attempts to gain access to the network.
2.The PEP requests and receives the user’s credentials from a utility on the endpoint.
3.With the credentials, the PEP composes an access request, which it forwards to the PDP.
4.The PDP seeks information about the user from the policy repository. On the basis of this information, it decides whether or not to authenticate the user.
With IDM, the PDP can factor additional criteria (such as location, time, and user group) into the decision.