Access Control Concepts
Network Access Control Technologies
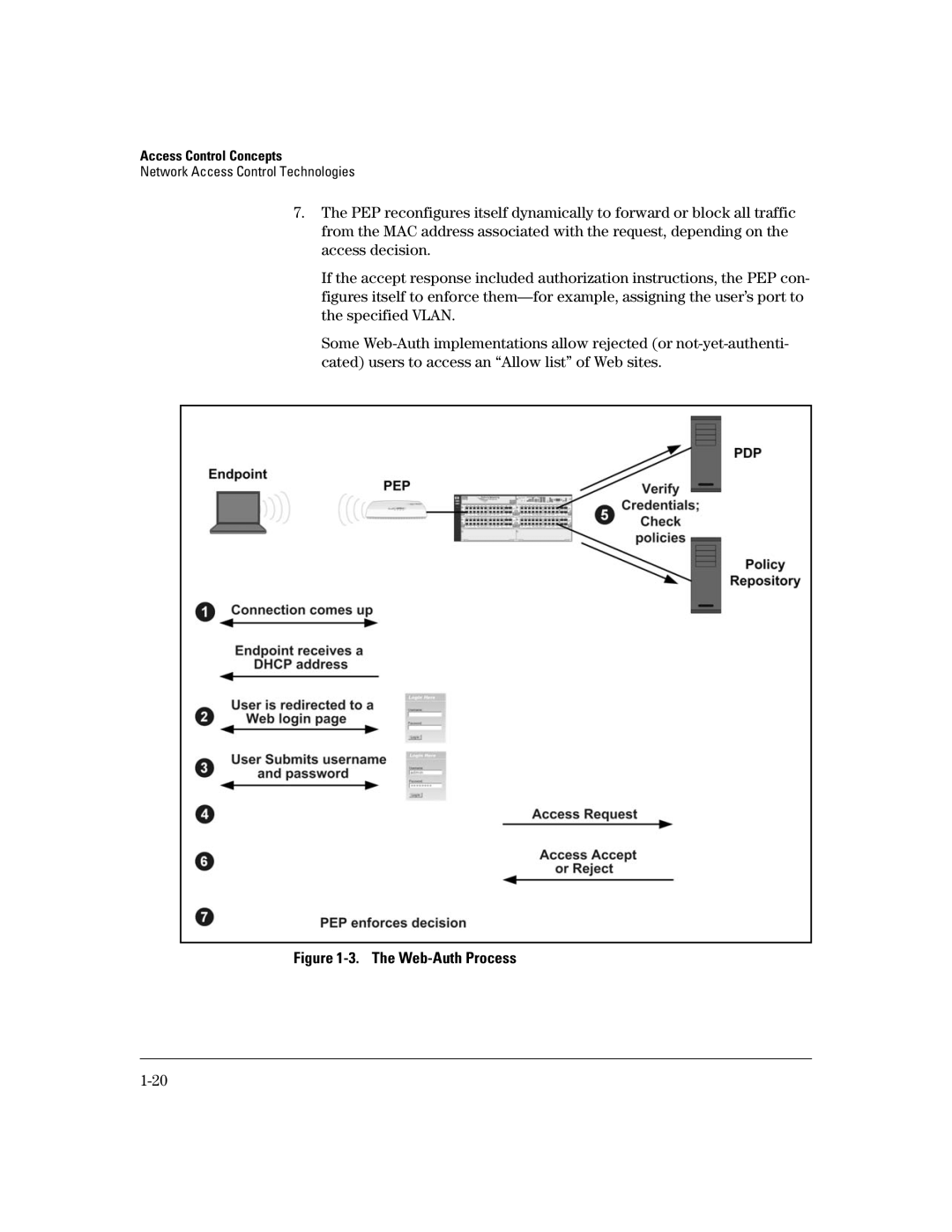
7.The PEP reconfigures itself dynamically to forward or block all traffic from the MAC address associated with the request, depending on the access decision.
If the accept response included authorization instructions, the PEP con- figures itself to enforce
Some