|
|
|
|
| Other Resources | |
|
|
|
|
|
| Implementation |
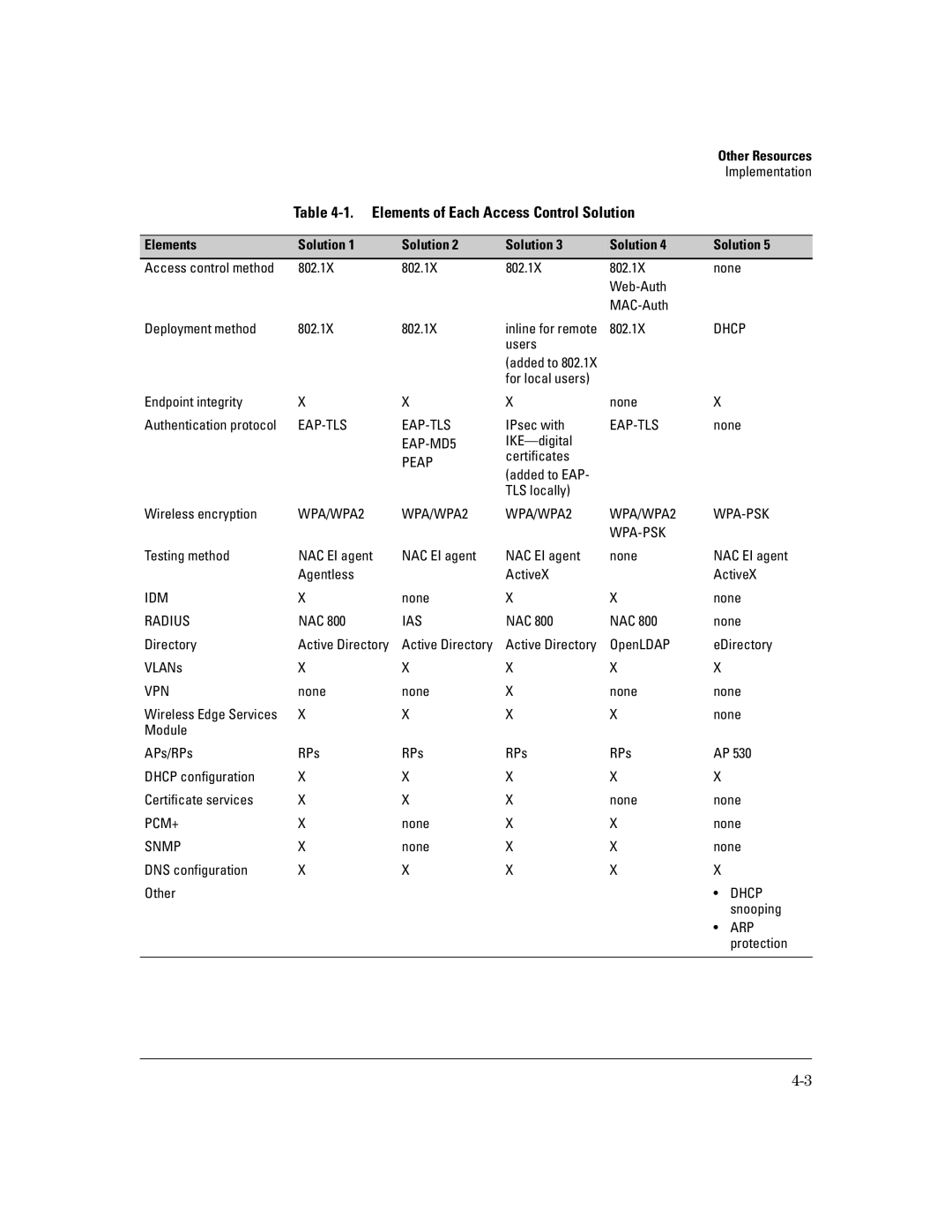
| Table |
|
| |||
|
|
|
|
|
| |
Elements | Solution 1 | Solution 2 | Solution 3 | Solution 4 | Solution 5 | |
|
|
|
|
|
| |
Access control method | 802.1X | 802.1X | 802.1X | 802.1X | none | |
|
|
|
|
|
| |
|
|
|
|
|
| |
Deployment method | 802.1X | 802.1X | inline for remote | 802.1X | DHCP | |
|
|
| users |
|
|
|
|
|
| (added to 802.1X |
|
|
|
|
|
| for local users) |
|
|
|
Endpoint integrity | X | X | X | none | X |
|
Authentication protocol | IPsec with | none | ||||
|
|
|
|
| ||
|
| PEAP | certificates |
|
|
|
|
| (added to EAP- |
|
|
| |
|
|
|
|
|
| |
|
|
| TLS locally) |
|
|
|
Wireless encryption | WPA/WPA2 | WPA/WPA2 | WPA/WPA2 | WPA/WPA2 | ||
|
|
|
|
|
| |
Testing method | NAC EI agent | NAC EI agent | NAC EI agent | none | NAC EI agent | |
| Agentless |
| ActiveX |
| ActiveX | |
IDM | X | none | X | X | none | |
RADIUS | NAC 800 | IAS | NAC 800 | NAC 800 | none | |
Directory | Active Directory | Active Directory | Active Directory | OpenLDAP | eDirectory | |
VLANs | X | X | X | X | X |
|
VPN | none | none | X | none | none | |
Wireless Edge Services | X | X | X | X | none | |
Module |
|
|
|
|
|
|
APs/RPs | RPs | RPs | RPs | RPs | AP 530 | |
DHCP configuration | X | X | X | X | X |
|
Certificate services | X | X | X | none | none | |
PCM+ | X | none | X | X | none | |
SNMP | X | none | X | X | none | |
DNS configuration | X | X | X | X | X |
|
Other |
|
|
|
| • | DHCP |
|
|
|
|
|
| snooping |
|
|
|
|
| • | ARP |
|
|
|
|
|
| protection |
|
|
|
|
|
|
|