Designing Access Controls
Make Decisions about Remote Access (VPN)
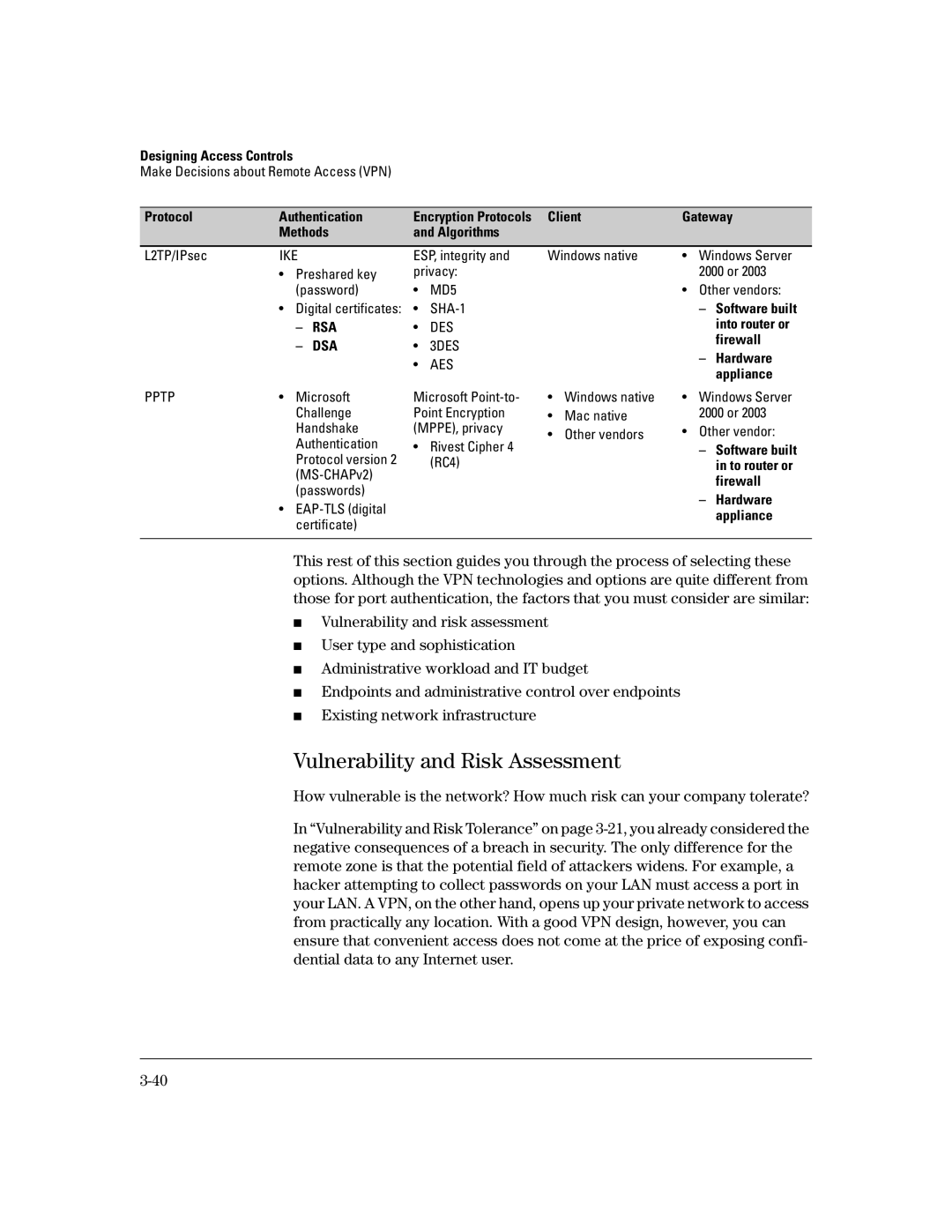
Protocol | Authentication | Encryption Protocols Client | Gateway |
| Methods | and Algorithms |
|
|
|
|
|
L2TP/IPsec | IKE |
| ESP, integrity and | ||
| • | Preshared key | privacy: | ||
|
| (password) | • | MD5 | |
| • | Digital certificates: | • |
| |
|
| – | RSA | • | DES |
|
| – | DSA | • | 3DES |
|
|
|
| • | AES |
PPTP | • | Microsoft | Microsoft | ||
|
| Challenge | Point Encryption | ||
|
| Handshake | (MPPE), privacy | ||
|
| Authentication | • | Rivest Cipher 4 | |
|
| Protocol version 2 |
| (RC4) | |
•
Windows native | • | Windows Server | |
|
| 2000 or 2003 | |
| • | Other vendors: | |
|
| – | Software built |
|
|
| into router or |
|
|
| firewall |
|
| – | Hardware |
|
|
| appliance |
• | Windows native | • | Windows Server | |
• | Mac native |
| 2000 or 2003 | |
• | Other vendors | • | Other vendor: | |
|
|
| – | Software built |
|
|
|
| in to router or |
|
|
|
| firewall |
|
|
| – | Hardware |
|
|
|
| appliance |
This rest of this section guides you through the process of selecting these options. Although the VPN technologies and options are quite different from those for port authentication, the factors that you must consider are similar:
■Vulnerability and risk assessment
■User type and sophistication
■Administrative workload and IT budget
■Endpoints and administrative control over endpoints
■Existing network infrastructure
Vulnerability and Risk Assessment
How vulnerable is the network? How much risk can your company tolerate?
In “Vulnerability and Risk Tolerance” on page