Designing Access Controls
Select an EAP Method for 802.1X
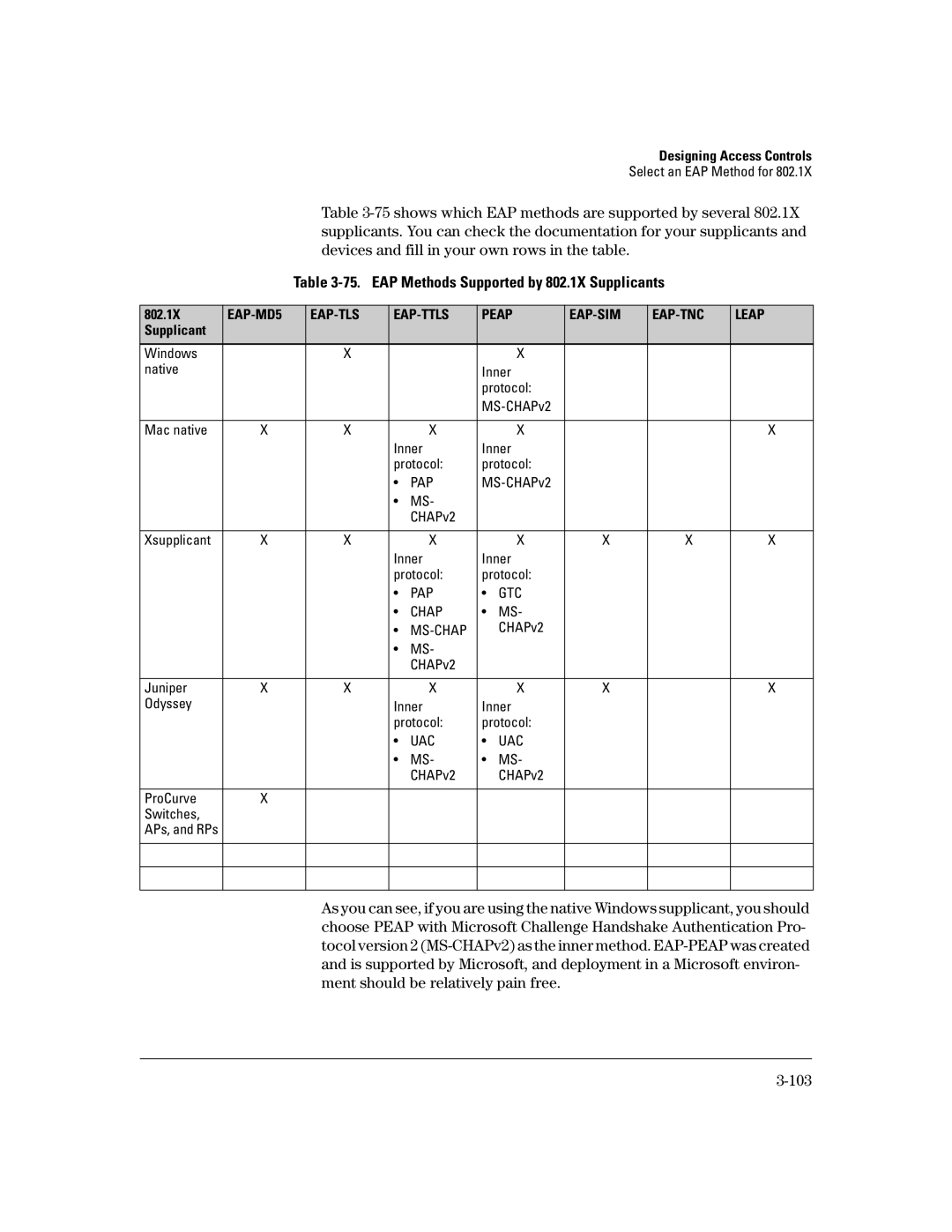
Table
Table 3-75. EAP Methods Supported by 802.1X Supplicants
802.1X |
|
|
| PEAP |
|
| LEAP | ||
Supplicant |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Windows |
| X |
|
|
| X |
|
|
|
native |
|
|
|
| Inner |
|
|
| |
|
|
|
|
| protocol: |
|
|
| |
|
|
|
|
|
|
|
| ||
|
|
|
|
|
|
|
|
|
|
Mac native | X | X |
| X |
| X |
|
| X |
|
|
| Inner | Inner |
|
|
| ||
|
|
| protocol: | protocol: |
|
|
| ||
|
|
| • | PAP |
|
|
| ||
|
|
| • | MS- |
|
|
|
|
|
|
|
|
| CHAPv2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Xsupplicant | X | X |
| X |
| X | X | X | X |
|
|
| Inner | Inner |
|
|
| ||
|
|
| protocol: | protocol: |
|
|
| ||
|
|
| • | PAP | • | GTC |
|
|
|
|
|
| • | CHAP | • | MS- |
|
|
|
|
|
| • |
| CHAPv2 |
|
|
| |
|
|
| • | MS- |
|
|
|
|
|
|
|
|
| CHAPv2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Juniper | X | X |
| X |
| X | X |
| X |
Odyssey |
|
| Inner | Inner |
|
|
| ||
|
|
| protocol: | protocol: |
|
|
| ||
|
|
| • | UAC | • | UAC |
|
|
|
|
|
| • | MS- | • | MS- |
|
|
|
|
|
|
| CHAPv2 |
| CHAPv2 |
|
|
|
|
|
|
|
|
|
|
|
|
|
ProCurve | X |
|
|
|
|
|
|
|
|
Switches, |
|
|
|
|
|
|
|
|
|
APs, and RPs |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
As you can see, if you are using the native Windows supplicant, you should choose PEAP with Microsoft Challenge Handshake Authentication Pro- tocol version 2