Designing Access Controls
Comprehensive Security Policy
laptops. Resource endpoints consist of databases, specialized server clusters, the supercomputer, and other
■Remote
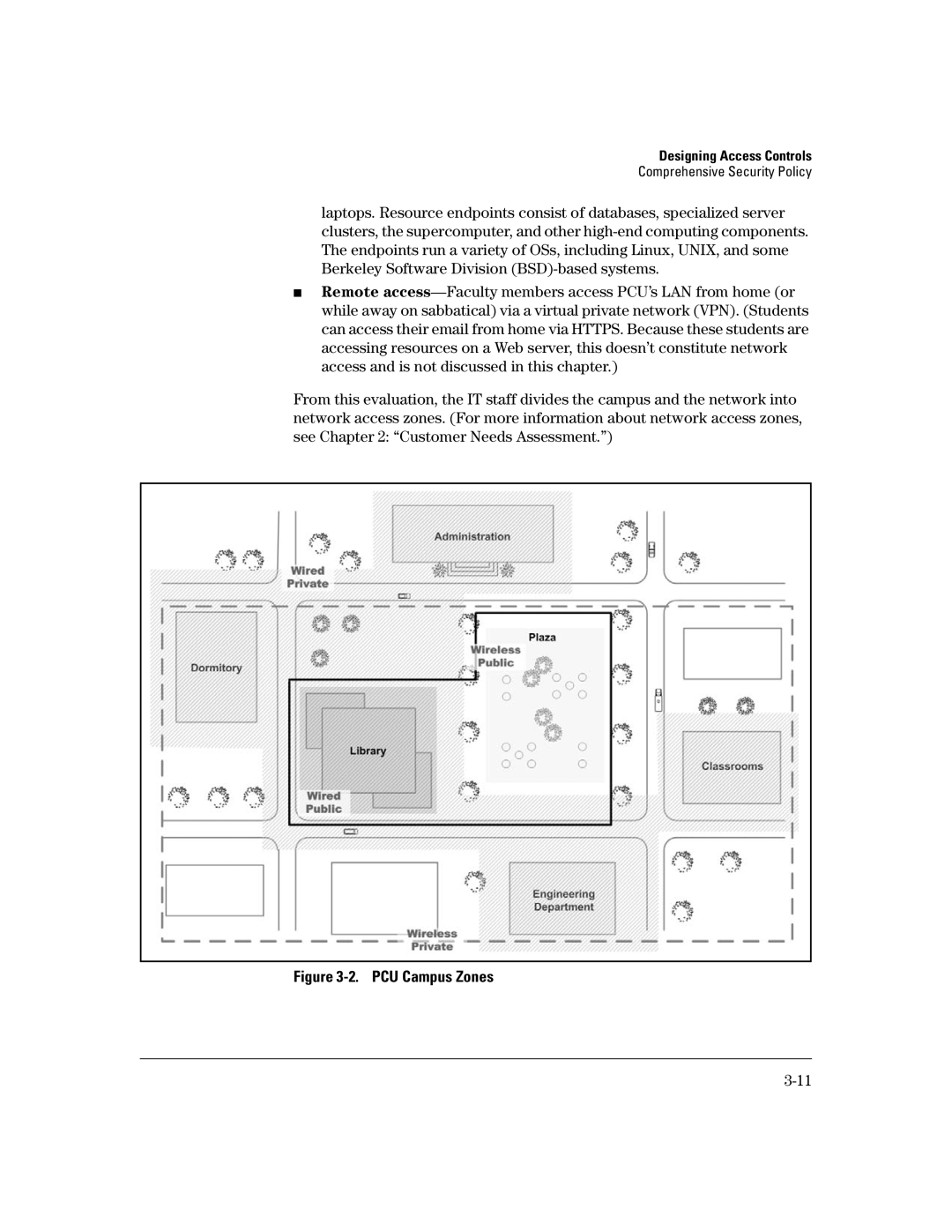
From this evaluation, the IT staff divides the campus and the network into network access zones. (For more information about network access zones, see Chapter 2: “Customer Needs Assessment.”)