Designing Access Controls
Choose the Access Control Methods
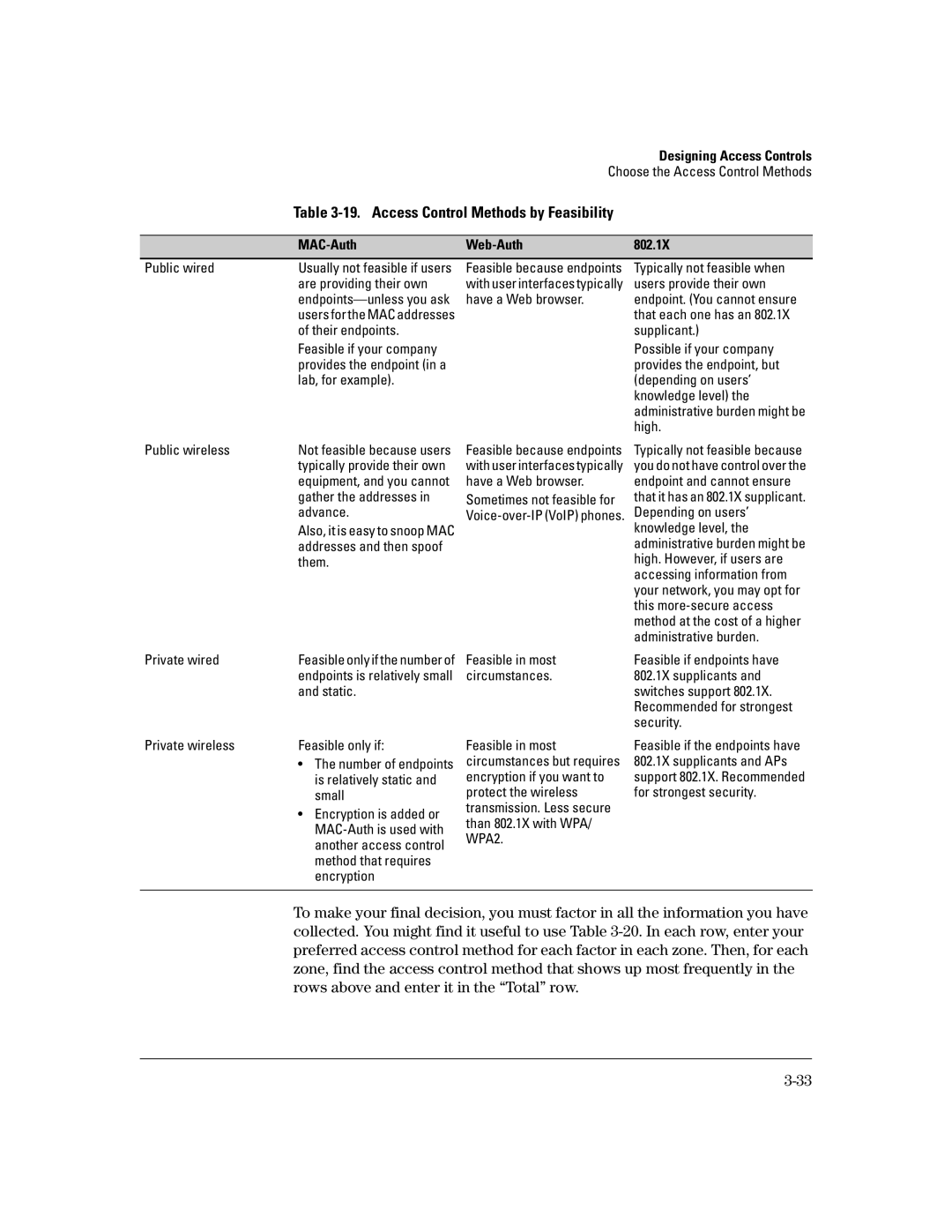
Table 3-19. Access Control Methods by Feasibility
| 802.1X | |
|
|
|
Public wired | Usually not feasible if users |
| are providing their own |
| |
| users for the MAC addresses |
| of their endpoints. |
| Feasible if your company |
| provides the endpoint (in a |
| lab, for example). |
Feasible because endpoints | Typically not feasible when |
with user interfaces typically | users provide their own |
have a Web browser. | endpoint. (You cannot ensure |
| that each one has an 802.1X |
| supplicant.) |
| Possible if your company |
| provides the endpoint, but |
| (depending on users’ |
| knowledge level) the |
| administrative burden might be |
| high. |
Public wireless | Not feasible because users |
| typically provide their own |
| equipment, and you cannot |
| gather the addresses in |
| advance. |
| Also, it is easy to snoop MAC |
| addresses and then spoof |
| them. |
Feasible because endpoints | Typically not feasible because |
with user interfaces typically | you do not have control over the |
have a Web browser. | endpoint and cannot ensure |
Sometimes not feasible for | that it has an 802.1X supplicant. |
Depending on users’ | |
| knowledge level, the |
| administrative burden might be |
| high. However, if users are |
| accessing information from |
| your network, you may opt for |
| this |
| method at the cost of a higher |
| administrative burden. |
Private wired | Feasible only if the number of | Feasible in most |
| endpoints is relatively small | circumstances. |
| and static. |
|
Private wireless | Feasible only if: | Feasible in most |
| • The number of endpoints | circumstances but requires |
| is relatively static and | encryption if you want to |
| small | protect the wireless |
| • Encryption is added or | transmission. Less secure |
| than 802.1X with WPA/ | |
| ||
| WPA2. | |
| another access control | |
|
| |
| method that requires |
|
| encryption |
|
Feasible if endpoints have 802.1X supplicants and switches support 802.1X. Recommended for strongest security.
Feasible if the endpoints have 802.1X supplicants and APs support 802.1X. Recommended for strongest security.
To make your final decision, you must factor in all the information you have collected. You might find it useful to use Table