Addendum to the ProCurve Access Control Security Design Guide
Microsoft NAP
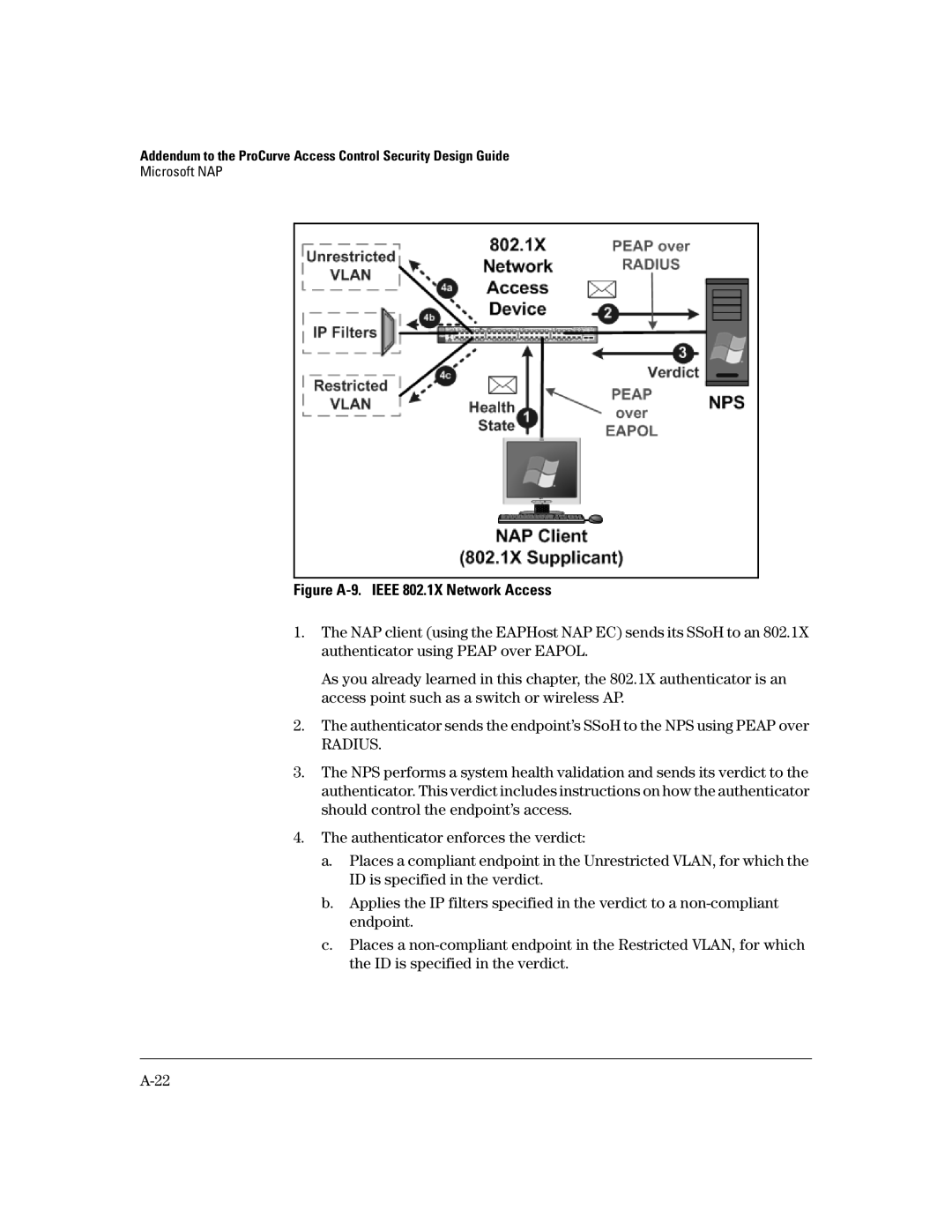
Figure A-9. IEEE 802.1X Network Access
1.The NAP client (using the EAPHost NAP EC) sends its SSoH to an 802.1X authenticator using PEAP over EAPOL.
As you already learned in this chapter, the 802.1X authenticator is an access point such as a switch or wireless AP.
2.The authenticator sends the endpoint’s SSoH to the NPS using PEAP over
RADIUS.
3.The NPS performs a system health validation and sends its verdict to the authenticator. This verdict includes instructions on how the authenticator should control the endpoint’s access.
4.The authenticator enforces the verdict:
a.Places a compliant endpoint in the Unrestricted VLAN, for which the ID is specified in the verdict.
b.Applies the IP filters specified in the verdict to a
c.Places a