Designing Access Controls
Choose RADIUS Servers
Choose RADIUS Servers
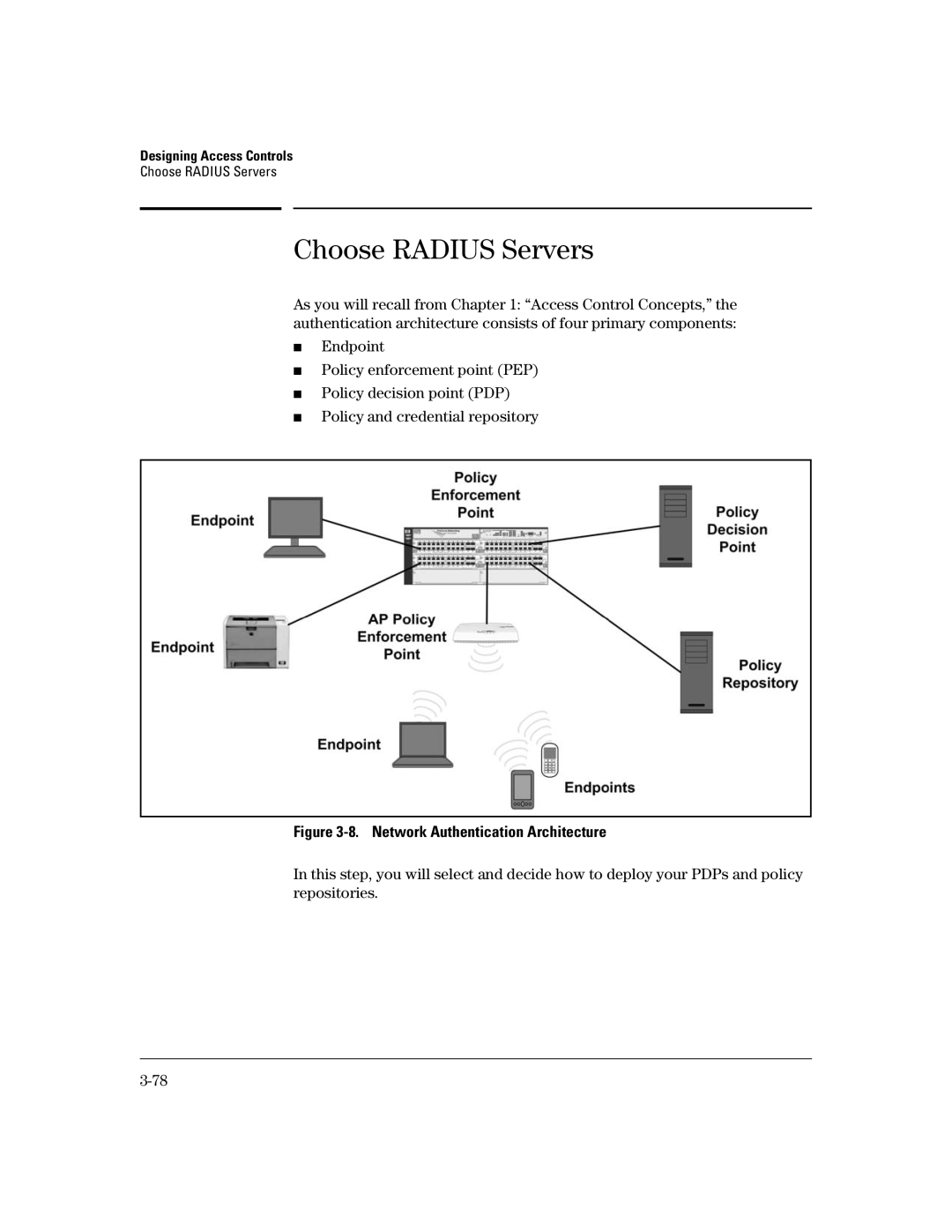
As you will recall from Chapter 1: “Access Control Concepts,” the authentication architecture consists of four primary components:
■Endpoint
■Policy enforcement point (PEP)
■Policy decision point (PDP)
■Policy and credential repository
Figure 3-8. Network Authentication Architecture
In this step, you will select and decide how to deploy your PDPs and policy repositories.