|
|
|
|
|
| Designing Access Controls |
|
|
|
|
|
| Finalize Security Policies |
|
|
|
|
|
|
|
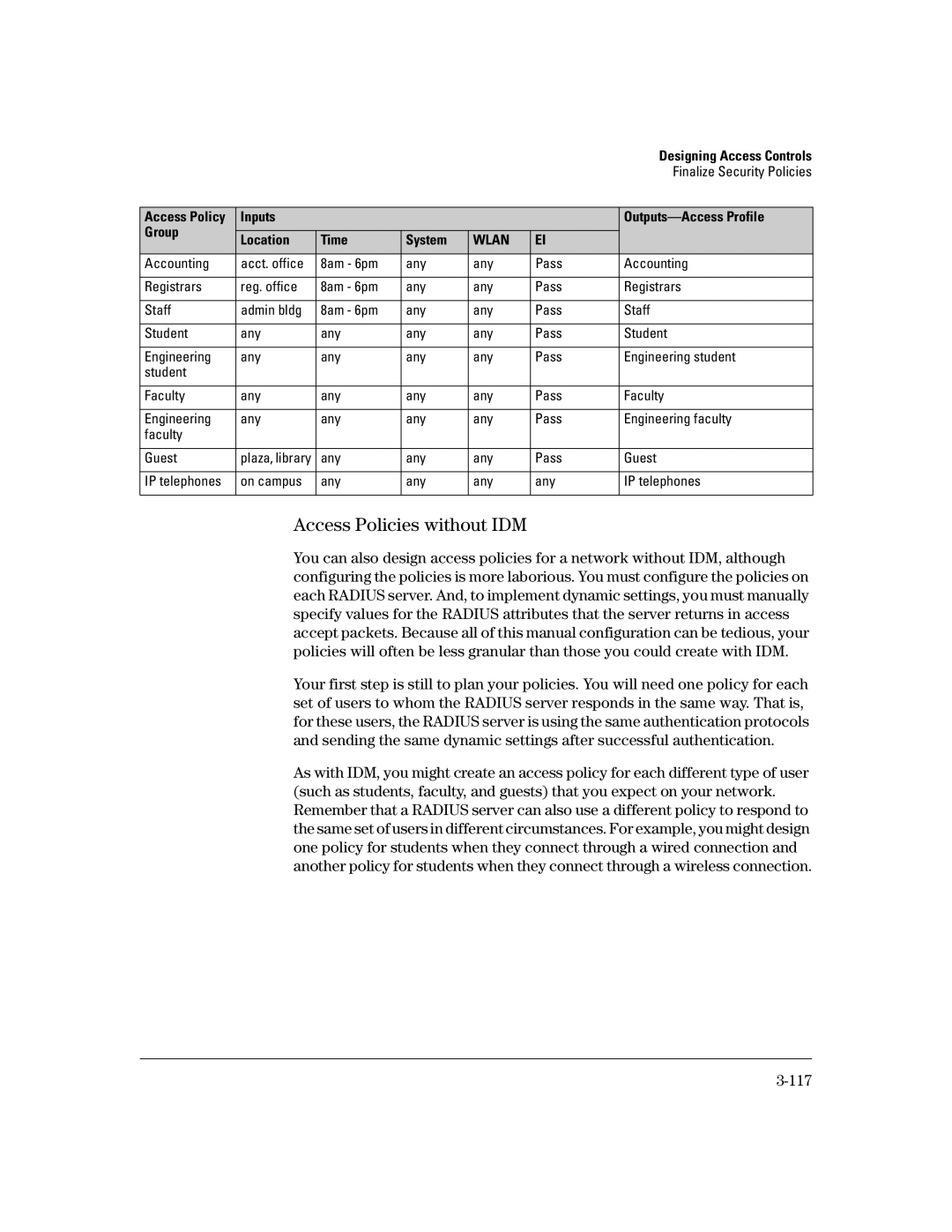
Access Policy | Inputs |
|
|
|
|
|
Group |
|
|
|
|
|
|
Location | Time | System | WLAN | EI |
| |
|
| |||||
|
|
|
|
|
|
|
Accounting | acct. office | 8am - 6pm | any | any | Pass | Accounting |
|
|
|
|
|
|
|
Registrars | reg. office | 8am - 6pm | any | any | Pass | Registrars |
|
|
|
|
|
|
|
Staff | admin bldg | 8am - 6pm | any | any | Pass | Staff |
|
|
|
|
|
|
|
Student | any | any | any | any | Pass | Student |
|
|
|
|
|
|
|
Engineering | any | any | any | any | Pass | Engineering student |
student |
|
|
|
|
|
|
|
|
|
|
|
|
|
Faculty | any | any | any | any | Pass | Faculty |
|
|
|
|
|
|
|
Engineering | any | any | any | any | Pass | Engineering faculty |
faculty |
|
|
|
|
|
|
|
|
|
|
|
|
|
Guest | plaza, library | any | any | any | Pass | Guest |
|
|
|
|
|
|
|
IP telephones | on campus | any | any | any | any | IP telephones |
|
|
|
|
|
|
|
Access Policies without IDM
You can also design access policies for a network without IDM, although configuring the policies is more laborious. You must configure the policies on each RADIUS server. And, to implement dynamic settings, you must manually specify values for the RADIUS attributes that the server returns in access accept packets. Because all of this manual configuration can be tedious, your policies will often be less granular than those you could create with IDM.
Your first step is still to plan your policies. You will need one policy for each set of users to whom the RADIUS server responds in the same way. That is, for these users, the RADIUS server is using the same authentication protocols and sending the same dynamic settings after successful authentication.
As with IDM, you might create an access policy for each different type of user (such as students, faculty, and guests) that you expect on your network. Remember that a RADIUS server can also use a different policy to respond to the same set of users in different circumstances. For example, you might design one policy for students when they connect through a wired connection and another policy for students when they connect through a wireless connection.