Prestige 792H
Page
Trademarks
Disclaimer
Page
Certifications
Page
Information for Canadian Users
Page
Safety Warnings
ZyXEL Limited Warranty
Page
Customer Support
Page
Table of Contents
WAN Setup
LAN Setup
Dynamic DNS Setup
Customized Services 11-1
Firewall Configuration
Content Filtering 12-1
Creating Custom Rules 10-1
15-1
14-1
General Setup 19-1
Maintenance 17-1
WAN Setup 20-4
Dial Backup 21-1
23-1
22-1
24-1
25-1
Snmp Configuration 29-1
Filter Configuration 28-1
System Maintenance 30-1
Firmware and Configuration File Maintenance 31-1
IP Policy Routing 33-1
System Maintenance and Information 32-1
Call Scheduling 34-1
Remote Management 35-1
Troubleshooting 39-1
VPN/IPSec Setup 36-1
SA Monitor 37-1
Internal Sptgen 38-1
List of Figures
Xviii List of Figures
List of Figures Xix
Diagnostic General 17-8
List of Figures Xxi
Xxii List of Figures
List of Figures Xxiii
Xxiv List of Figures
List of Figures Xxv
Page
List of Tables
List of Tables Xxvii
Xxviii List of Tables
28-15
Xxx List of Tables
Page
Syntax Conventions
Related Documentation
Xxxii Preface
Introduction to G.SHDSL
Introduction to DSL
Part
Page
Symmetrical High Speed Internet Access
Features of the Prestige
Getting to Know Your G.SHDSL Router
Scalability
Firewall
IPSec VPN Capability
Traffic Redirect
Snmp Simple Network Management Protocol versions 1
IP Alias
SUA for Single-IP Address Internet Access
IP Policy Routing
10/100MB Auto-negotiation Ethernet/Fast Ethernet Interface
Ease of Installation
Upgrade Firmware via LAN
Universal Plug and Play UPnP
Full Network Management
LAN-to-LAN Application
Internet Access
Application Scenarios for the Prestige
Accessing the Prestige Web Configurator
Introducing the Web Configurator
Web Configurator Overview
Password Screen
Navigating the Prestige Web Configurator
Configuring Password
Label Description
Resetting the Prestige
Uploading a Configuration File Via Console Port
Using The Reset Button
Page
Wizard Setup Introduction
Wizard Setup
WAN Setup
Service Type
Encapsulation
Standard Mode
Transfer Rates
PPP over Ethernet
PPPoA
Multiplexing
4 RFC
VC-based Multiplexing
VPI and VCI
Wizard Setup Configuration First Screen
Rate and the same Transfer Min Rate
Server see Service Type
PPPoE
IP Address and Subnet Mask
VPI
VCI
IP Assignment with PPPoA or PPPoE Encapsulation
IP Address Assignment
Private IP Addresses
IP Assignment with RFC 1483 Encapsulation
IP Assignment with Enet Encap Encapsulation
10 NAT
Wizard Setup Configuration ISP Parameters
Nailed-Up Connection PPP
Internet Connection with PPPoA
Internet
Internet Connection with RFC
11.2 RFC
Enet Encap
Internet Connection with Enet Encap
Internet Connection with PPPoE
PPPoE
Dhcp Setup
IP Pool Setup
Wizard Setup Configuration LAN Configuration
Wizard LAN Configuration
Wizard Screen LAN COnfiguration
Wizard Setup Configuration Connection Tests
Wizard Screen Connection Tests
Test Your Internet Connection
Page
LAN Overview
LAN Setup
DNS Server Address
LANs, WANs and the Prestige
LAN TCP/IP
DNS Server Address Assignment
RIP Setup
Factory LAN Defaults
IP Address and Subnet Mask
Multicast
LAN
Configuring LAN
TCP/IP
LAN
Metric
WAN Setup
WAN Overview
PPPoE Encapsulation
Traffic Shaping
Example of Traffic Shaping
Configuring WAN Setup
WAN Setup
ATM traffic. Enter the VCI assigned to you
Subnet as the remote node
For remote node setup, enter the IP address in the same
Encap in the Encapsulation field
Traffic Redirect
Traffic Redirect LAN Setup
Configuring WAN Backup
WAN Backup
Cost
38400 , 57600 , 115200 or 230400 bps
Outgoing Authentication Protocol
WAN , Traffic Redirect , Dial Backup
Configuring Advanced WAN Backup
Advanced WAN Backup
57600 , 115200 or 230400 bps
Choose Both, In Only or Out Only
Choose RIP-1,RIP-2B or RIP-2M
Connection settings
AT Command Strings
Response Strings
DTR Signal
Configuring Advanced Modem Setup
Advanced Modem Setup
Nmbr
Clid
Part
Page
NAT Overview
Network Address Translation NAT
NAT Definitions
What NAT Does
NAT Application
How NAT Works
NAT Application With IP Alias
NAT Mapping Types
Mapping types
SUA Single User Account Versus NAT
NAT Mapping Types
Type IP Mapping SMT Abbreviation
SUA Server
Port Forwarding Services and Port Numbers
Services and Port Numbers
Configuring Servers Behind SUA Example
Services Port Number
Echo
Multiple Servers Behind NAT Example
Selecting the NAT Mode
Configuring SUA Server
Edit SUA/NAT Server Set
Configuring Address Mapping
Many-to-One and Server mapping types
Address Mapping Rules
Address Mapping Rule Edit
Editing an Address Mapping Rule
Address Mapping Rules screen
Page
Configuring Dynamic DNS
Dynamic DNS Setup
Dynamic DNS
Dyndns Wildcard
Ddns
Firewall and Content Filter
Page
Firewall Overview
Firewalls
Types of Firewalls
Packet Filtering Firewalls
Stateful Inspection Firewalls
Introduction to ZyXEL’s Firewall
Basics
Denial of Service
Common IP Ports
Types of DoS Attacks
Three-Way Handshake
Icmp Commands That Trigger Alerts
Legal Smtp Commands
Legal NetBIOS Commands
Stateful Inspection
Message Request Positive Negative Retarget Keepalive
Stateful Inspection
Stateful Inspection Process
Stateful Inspection and the Prestige
4 UDP/ICMP Security
TCP Security
Security In General
Guidelines for Enhancing Security with Your Firewall
Upper Layer Protocols
Packet Filtering
Packet Filtering Vs Firewall
Firewall
When To Use Filtering
Prestige 792H G.SHDSL Router
Enabling the Firewall
Firewall Configuration
Remote Management and the Firewall
E-mail
Configuring E-mail Alerts
Attack Alert
Daily Weekly Hourly When Log is Full None
Half-Open Sessions
Alerts
Threshold Values
TCP Maximum Incomplete and Blocking Time
Following table describes the labels in this screen
Alert
256
Page
Study these points carefully before configuring rules
Rule Checklist
Creating Custom Rules
Rules Overview
Block means the firewall silently discards the packet
Key Fields For Configuring Rules
Security Ramifications
LAN to WAN Rules
Connection Direction
WAN to LAN Rules
Logs
Label Description Example
Firewall Logs
Block, Forward or None
Rule Summary
Firewall Rules Summary First Screen
Predefined Services
Service Description
Predefined Services
NEWSTCP144
RLOGINTCP513
NNTPTCP119
PINGICMP0
Creating/Editing Firewall Rules
Creating/Editing a Firewall Rule
Source and Destination Addresses
Range Address , Subnet Address and Any Address
Timeout
Timeout
Factors Influencing Choices for Timeout Values
10-16 Creating Custom Rules
Introduction to Customized Services
Customized Services
Creating/Editing a Customized Service
Creating/Editing a Customized Service
Click Rule Summary under Internet to Local Network Set
Example Custom Service Firewall Rule
Configure Source IP Example
Syslog Rule Configuration Example
Rule Summary Example
Configuring Keyword Blocking
Content Filtering
Content Filtering Overview
Content Filter Keyword
Content Filter Schedule
Configuring the Schedule
Content Filter Trusted
Configuring Trusted Computers
Content Filter Logs
Configuring Logs
Blockcybernot
BLOCKUNTRUSTDOMAIN, BLOCKKEYWORD, Blockactivex
BLOCKJAVAAPPLET, BLOCKCOOKIE, Blockproxy
VPN/IPSec
Page
VPN Overview
Introduction to IPSec
IPSec
Security Association
Data Integrity
Data Origin Authentication
VPN Applications
VPN Application
IPSec Architecture
Key Management
IPSec Algorithms
IPSec and NAT
Transport Mode
Tunnel Mode
ESP
Security Protocol Mode NAT
VPN and NAT
VPN Screens
AH Authentication Header Protocol
14.1 VPN/IPSec Overview
IPSec Algorithms
Secure Gateway Address
My IP Address
Dynamic Secure Gateway Address
AH and ESP
IPSec Summary Fields
VPN Summary Screen
VPN Summary
Keep Alive
ID Type and Content
Local ID Type and Content Fields
ID Type and Content Examples
Peer ID Type and Content Fields
Local ID TYPE= CONTENT=
Mismatching ID Type and Content Configuration Example
Matching ID Type and Content Configuration Example
Pre-Shared Key
Editing VPN Policies
VPN IKE
VPN Screens 14-9
14-10 VPN Screens
VPN Screens 14-11
IKE
Authentication Algorithm fields described next
Two Phases to Set Up the IPSec SA
IKE Phases
Diffie-Hellman DH Key Groups
Negotiation Mode
Perfect Forward Secrecy PFS
14.11Configuring Advanced IKE Settings
Label Description VPN IKE
VPN IKE Advanced
VPN Screens 14-17
14-18 VPN Screens
Security Parameter Index SPI
14.12Manual Key Setup
VPN Manual Key
14.13Configuring Manual Key
SPI
14-22 VPN Screens
VPN Screens 14-23
14.14Viewing SA Monitor
10 SA Monitor
SA Monitor
11 Global Setting
14.15Configuring Global Setting
12 VPN Logs
14.16Configuring IPSec Logs
LOG Message Description
13 Sample IKE Key Exchange Logs
Request conflict with rule #d
14 Sample IPSec Logs During Packet Transmission
LOG Display Payload Type
15 RFC-2408 Isakmp Payload Types
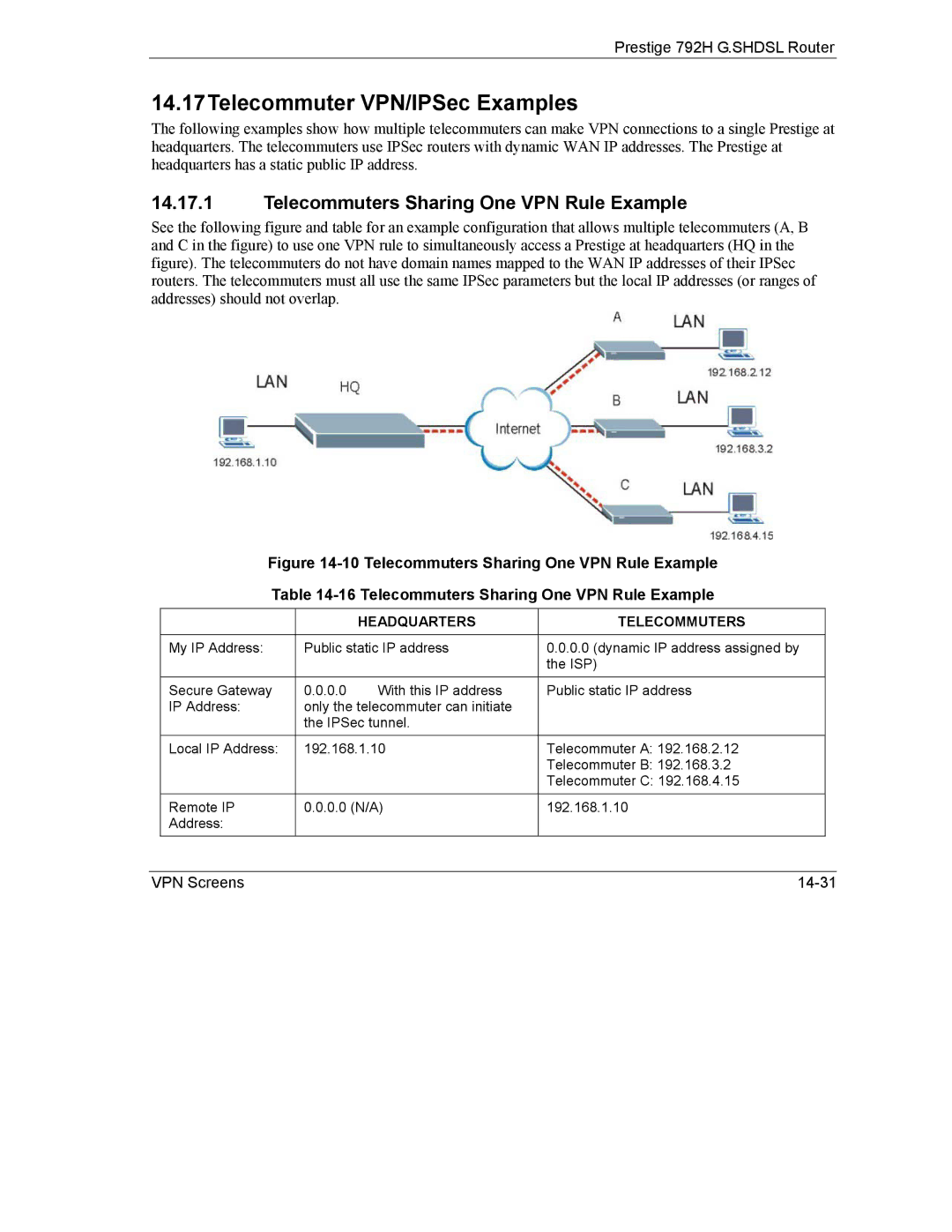
Headquarters Telecommuters
14.17Telecommuter VPN/IPSec Examples
Telecommuters Sharing One VPN Rule Example
All Headquarters Rules All Telecommuter Rules
Telecommuters Using Unique VPN Rules Example
14.18VPN and Remote Management
Remote Management and UPnP
Remote Management Overview
Remote Management Configuration
Remote Management Limitations
Remote Management and NAT
Telnet
System Timeout
15.3 FTP
15.4 Web
Remote Management
Configuring Remote Management
Universal Plug-and-Play UPnP
How do I know if Im using UPnP?
Universal Plug and Play Overview
NAT Transversal
UPnP and ZyXEL
Accessing the Prestige Web Configurator to Configure UPnP
Configuring UPnP
Field Description
Installing UPnP in Windows Example
Installing UPnP in Windows Me
Optional Networking Component
Installing UPnP in Windows XP
Double-clickNetwork Connections
Auto-discover Your UPnP-enabled Network Device
Using UPnP in Windows XP Example
Internet Connection Properties
Connections Select My Network Places under Other Places
Web Configurator Easy Access Example
Click start and then Control Panel
UPnP 16-9
Maintenance
Page
System Status Screen
Maintenance
Maintenance Overview
System Status
VPI/VCI
System Status Show Statistics
System Statistics
Maintenance 17-5
Dhcp Table
Dhcp Table Screen
MAC
Diagnostic Screens
Diagnostic General Screen
Diagnostic General
Prestige 792H G.SHDSL Router
Diagnostic DSL Line Screen
Firmware Screen
Firmware Upgrade
Network Temporarily Disconnected
SMT General Configuration
Procedure for SMT Configuration via Telnet
Procedure for SMT Configuration via Console Port
Entering Password
Introducing the SMT
Prestige SMT Menu Overview
Login Screen
Prestige Menu Overview
Navigating the SMT Interface
Main Menu Commands
Operation Keystroke Description
? or ChangeMe
Menu Title Description
System Management Terminal Interface Summary
Main Menu Summary
Menu 23 System Password
Changing the System Password
Configuring Menu
General Setup
General Setup
Yes
Configure Menu 1.1 Configure Dynamic DNS discussed next
Field Description Example
User
Configuring Dynamic DNS
Page
From the main menu, enter 2 to open menu
WAN Setup Screen
20-5
Configuring Dial Backup in Menu
Dial Backup
Dial Backup Overview
Enter to go to Menu 2.1 Advanced Setup
Advanced WAN Setup
115200
9600, 19200, 38400, 57600, 115200 or 230400 bps
Nmbr =
Field Description Default
Connect
Remote Node Profile Backup ISP
Advanced WAN Port Setup Call Control Parameters
CHAP/PAP
Remote Node Profile Backup ISP
Press Enter to go to Menu 11.3 Remote Node Network
Otherwise select Standard PPP
Editing PPP Options
Editing TCP/IP Options
NAT
Enter to open Menu 11.3 Network Layer Options
Both
Editing Filter Sets
Both/ None /In Only /Out Only and None
RIP-1
Menu 11.5 Remote Node Filter Ethernet
LAN Port Filter Setup
Ethernet Setup
TCP/IP and Dhcp Setup
IP Alias Setup
RIP-2B or RIP-2M
Route IP Setup
Both , In Only or Out Only
General Setup
22.1.4 TCP/IP Ethernet Setup and Dhcp
RIP-1,RIP-2B or RIP-2M
Both Both, In Only, Out Only or None
RIP-1
22-6
Internet Access Setup
Internet Access
Internet Access Overview
Or Enet Encap
Enet Encap
LLC-based
UBR
SUA Only
Dynamic
Advanced Applications
Remote Node Overview
Remote Node Configuration
Remote Node Setup
Encapsulation and Multiplexing Scenarios
Remote Node Setup
Based or LLC-based
Then the Rem Login, Rem Password, My Login, My
To display Menu 11.3 Remote Node Network Layer Options
Chap
To display Menu 11.6 Remote Node ATM Layer Options
Allocated Budget is 10 minutes and the Period hr
Remote
Remote Node Network Layer Options
Static
Options are Both, In Only, Out Only or None
My WAN Addr Sample IP Addresses
Sample IP Addresses for a TCP/IP LAN-to-LAN Connection
Remote Node Filter
Press Enter to open Menu 11.6 Remote Node ATM Layer Options
Editing ATM Layer Options
VC-based Multiplexing non-PPP Encapsulation
Menu 11.6 for LLC-based Multiplexing or PPP Encapsulation
LLC-based Multiplexing or PPP Encapsulation
Static Route Overview
Static Route Setup
Static Route Setup
Edit IP Static Route
Page
Bridge Ethernet Setup
Bridging Setup
Remote Node Bridging Setup
Bridging Overview
Remote Node Bridging Options
Bridge Static Route Setup
Bridge Static Route Setup
26-4 Bridging Setup
Applying NAT
Applying NAT for Internet Access
Full Feature
NAT Setup
Address Mapping Sets
Enter 1 to bring up Menu 15.1 Address Mapping Sets
Address Mapping Rules SUA
Address Mapping Sets
User-Defined Address Mapping Sets
Natset
Field Desription Example
Select Rule item
Global Start/End IPs
Edit
To-One,Many-to-One and Server types
One-to-One
For Server
NAT Server Sets
NAT Server Setup
General NAT Examples
Example 1 Internet Access Only
11 NAT Example
13 NAT Example
Example 2 Internet Access with an Inside Server
14 NAT Example 2 Menu
Example 3 Multiple Public IP Addresses With Inside Servers
15 NAT Example
17 Example 3 Menu
Enter 2 in Menu 15 NAT Setup
19 Example 3- Menu
Example 4 NAT Unfriendly Application Programs
21 Example 4 Menu
22 Example 4 Menu
Advanced Management
Page
About Filtering
Filter Configuration
Outgoing Packet Filtering Process
Filter Rule Process
Execute Filter Rule
Filter Structure of the Prestige
Filter Set Configuration
NetBios WAN Filter Rules Summary
TelnetWAN Filter Rules Summary
Ftpwan Filter Rules Summary
Abbreviations Used in the Filter Rules Summary Menu
Filter Rules Summary Menus
Rule Abbreviations Used
Filter Rule Configuration
Filter Type Description
GEN
Choices are TCP/IP Filter Rule or Generic Filter Rule
28.3.1 TCP/IP Filter Rule
TCP/IP Filter Rule
If More is Yes , then Action Matched and Action Not
TCP/IP Filter Rule
Choices are None , Less , Greater , Equal or Not Equal
Choices are Check Next Rule, Forward or Drop
Check Next Rule
Check Next Rule, Forward or Drop
12 Executing an IP Filter
13 Generic Filter Rule
Generic Filter Rule
Generic Filter Rule Menu Fields
Example Filter
Filter Types and NAT
15 Sample Telnet Filter
16 Sample Filter Rules Summary Menu
17 Sample Filter Rules Summary Menu
Ethernet Traffic
Applying Filters and Factory Defaults
Filter Sets Table
Filter Sets Description
19 Filtering Ethernet Traffic
Remote Node Filters
Page
Snmp Overview
Snmp Configuration
Snmp is only available if TCP/IP is configured
Supported MIBs
Snmp Configuration
Snmp Traps
Snmp Traps
Snmp
Trap # Trap Name Description
29-4 Snmp Configuration
System Status
System Maintenance
System Maintenance Overview
System Maintenance Status
WAN
System Information
System Information
LAN
Menu 1 General Setup
Console Port Speed
Viewing Error Log
Log and Trace
Syslog
Sample Error and Information Messages
CDR
System Maintenance Menu Syslog Parameters
Parameter Description
System Maintenance Diagnostic
Diagnostic
System Maintenance Menu Diagnostic
Page
Filename Conventions
Firmware and Configuration File Maintenance
File Type Internal External Name Description
Backup Configuration
Filename Conventions
Example of FTP Commands from the Command Line
Backup Configuration
Using the FTP Command from the Command Line
Command Description
General Commands for GUI-based FTP Clients
GUI-based FTP Clients
Tftp and FTP over WAN Will Not Work When
GUI-based Tftp Clients
Backup Configuration Using Tftp
Tftp Command Example
General Commands for GUI-based Tftp Clients
Backup Via Console Port
Backup Configuration Example
Restore Configuration
System Maintenance Restore Configuration
Restore Using FTP
Restore Via Console Port
Restore Using FTP Session Example
Firmware File Upload
Uploading Firmware and Configuration Files
13 System Maintenance Upload System Firmware
Configuration File Upload
Tftp File Upload
FTP File Upload Command from the DOS Prompt Example
FTP Session Example of Firmware File Upload
Uploading Via Console Port
Tftp Upload Command Example
Uploading Firmware File Via Console Port
Example Xmodem Firmware Upload Using HyperTerminal
Example Xmodem Configuration Upload Using HyperTerminal
Uploading Configuration File Via Console Port
19 Example Xmodem Upload
Command Interpreter Mode
System Maintenance and Information
Budget Management
Call Control Support
Budget Management
System Maintenance Time and Date Setting
Time and Date Setting
NTP RFC-1305 is similar to Time RFC-868
Resetting the Time
Time and Date Setting Fields
Page
IP Policy Routing Overview
IP Policy Routing
IP Policy Routing Benefits
Routing Policy
IP Routing Policy Setup
IP Routing Policy Setup
Abbreviation Meaning
Service
Criterion
Action
G t
Delay, Max Thruput, Min Cost or Max Reliable
Ethernet IP Policies
Applying an IP Policy
Less, Greater, Less or Equal or Greater or Equal
Matched
33-6 IP Policy Routing
Example of IP Policy Routing
IP Policy Routing Example
IP Routing Policy Example
Applying IP Policies
Page
Call Scheduling Overview
Schedule Setup
Call Scheduling
Schedule Set Setup
Forced On
Once
Applying Schedule Sets to a Remote Node PPPoE
Remote Management
Remote Management and Telnet Services
Remote Management and FTP Services
Remote Management and Web Services
Remote Management Setup
Disabling Remote Management
Remote Management Control
Remote Management and NAT
System Timeout
SMT VPN/IPSec and Internal Sptgen
36.1 VPN/IPSec Overview
VPN/IPSec Setup
IPSec Summary Screen
Menu 27 VPN/IPSec Setup
ESP DES MD5
Tunnel
36-4 VPN/IPSec Setup
IPSec Setup
IPSec Summary
Menu 27.1.1 IPSec Setup
Gateway Address field below
Single
Address field set to
Subnet
Manual Setup
3Menu 27.1.1.1 IKE Setup
IKE Setup
Field
Description Example
MD5
DES
DH1
Mode Security Protocol
Manual Setup
Active Protocol
Active Protocol Encapsulation and Security Protocol
ESP Tunnel
Menu 27.1.1.2 Manual Setup
VPN/IPSec Setup 36-15
Page
SA Monitor Overview
Using SA Monitor
SA Monitor
Refresh
Taiwan
ESP DES
VPN Responder IPSec Log
Diagram 37-1 Example VPN Responder IPSec Log
Viewing IPSec Log
Page
Internal Sptgen Overview
Configuration Text File Format
Internal Sptgen
38-2 Internal Sptgen
Internal Sptgen FTP Download Example
Invalid Parameter Entered Command Line Example
Internal Sptgen FTP Upload Example
Internal Sptgen FTP Upload Example
Appendices and Index
Page
Problems Starting Up the Prestige
Troubleshooting
Problems with the LAN Interface
Troubleshooting the Start-Up of Your Prestige
Problems with Internet Access
Problems with the WAN Interface
Troubleshooting the WAN Interface
Troubleshooting Internet Access
Problems with Telnet
Problems with the Password
Troubleshooting the Password
Troubleshooting Telnet
Page
PPPoE in Action
Appendix a PPPoE
Benefits of PPPoE
Traditional Dial-up Scenario
Prestige as a PPPoE Client
Diagram 2 Prestige as a PPPoE Client
Appendix B Virtual Circuit Topology
Diagram 3 Virtual Circuit Topology
Appendix C
Power Adapter Specifications
North American Plug Standards
United Kingdom Plug Standards
China Standards
European Plug Standards
AA-121ABN
Power Consumption Safety Standards Ccee GB8898
Index
17-10
28-4
30-6
Local Network
10-7
24-1,24-2
24-2
30-5
RIP
Traceroute
TCP/IP