keying material for use with ISAKMP, and for other security associations such as AH and ESP for the IPsec DOI.
3.6.1 IPSec
The IPSec services can provide access control, connectionless integrity, data origin authentication, rejection of replayed packets that is a form of partial sequence integrity, and confidentiality by encryption. These objectives are met through the use of two traffic security protocols, the Authentication Header (AH) and the Encapsulating Security Payload (ESP), and through the use of cryptographic key management procedures and protocols.
Policy Table
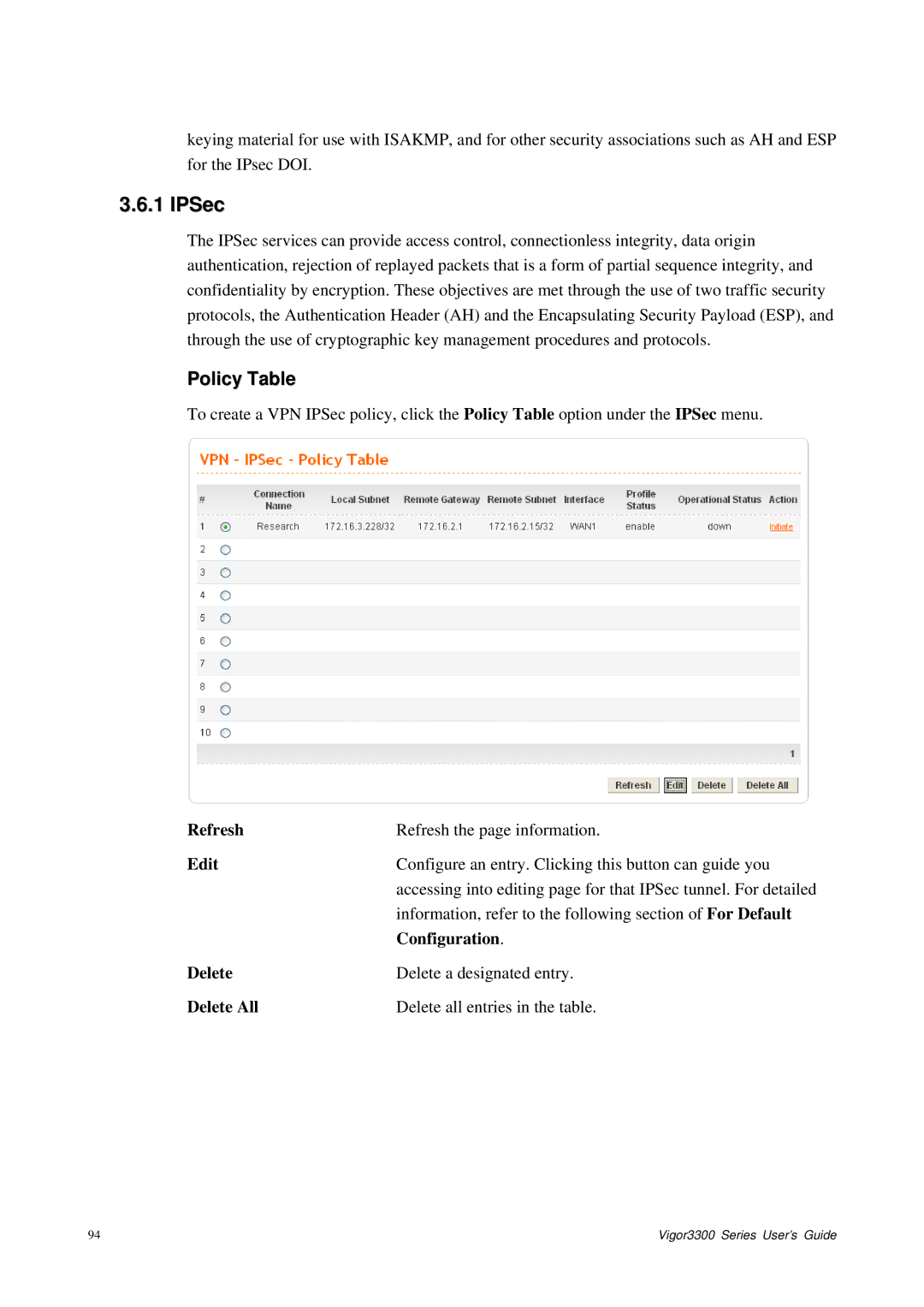
To create a VPN IPSec policy, click the Policy Table option under the IPSec menu.
Refresh | Refresh the page information. |
Edit | Configure an entry. Clicking this button can guide you |
| accessing into editing page for that IPSec tunnel. For detailed |
| information, refer to the following section of For Default |
| Configuration. |
Delete | Delete a designated entry. |
Delete All | Delete all entries in the table. |
94 | Vigor3300 Series User’s Guide |