Administration Guide
Cisco Systems, Inc. All rights reserved 78-20776-03
FCC Radiation Exposure Statement For ISA550W and ISA570W
Important Note
Déclaration dexposition aux radiations
Industry Canada statement
Canada Radiation Exposure Statement For ISA550W and ISA570W
UL/CB
Getting Started
Configuration Wizards
Using Remote Access VPN Wizard for SSL Remote Access
Status
Networking 115
Understanding Dscp Values 171
Vlan Setup 180 Wireless Setup 181 User Authentication
Wireless for ISA550W and ISA570W only 206
Firewall 251
Vlan Setup 222 Wireless Setup 223 User Authentication
Security Services 291
VPN 333
General Application Control Settings 314
Client Mode 366 Network Extension Mode 367
Device Management 403
User Management 388
Contents
Appendix D Where to Go From Here 479
Appendix a Troubleshooting 453
Getting Started
Introduction
Model Description Configuration
Getting Started
ISA550W
Front Panel, Back Panel,
Product Overview
Front Panel
Light Description
POWER/SYS
VPN
USB
Speed
Back Panel
LINK/ACT
ISA550 and ISA550W Back Panel
ANT01/ANT02
Feature Description
Reset Button
Getting Started with the Configuration Utility
Power Switch
Power
Logging in to the Configuration Utility
Number Component Description
Navigating Through the Configuration Utility
Icon Description Action
Using the Help System
Configuration Utility Icons
Getting Started
Default Settings of Key Features
Factory Default Settings
Restoring the Factory Default Settings
Parameter Default Value
Performing Basic Configuration Tasks
Changing the Default Administrator Password
Click Continue
Upgrading your Firmware After your First Login
Backing Up Your Configuration
Configuration Wizards
Configuration Wizards
Using the Setup Wizard for the Initial Configuration
Starting the Setup Wizard
Enabling Firmware Upgrade
Enabling Bonjour and CDP Discovery Protocols
Validating Security License
Configuring Remote Administration
Configuring Physical Ports
Configuring WAN Redundancy
Configuring the Primary WAN
Configuring the Secondary WAN
Configuring Default LAN Settings
Configuring DMZ
Configuring DMZ Services
Configuration Wizards
WAN IP
Configuring Wireless Radio Settings
WAN
Configuring Intranet Wlan Access
Security Services
Configure Security Services
Viewing Configuration Summary
Starting the Dual WAN Wizard
Configuring a Configurable Port as a Secondary WAN Port
Click Configuration Wizards Dual WAN Wizard
Configuring the Primary WAN
Configuring Network Failure Detection
Using the Remote Access VPN Wizard for IPsec Remote
Using the Remote Access VPN Wizard
Click Configuration Wizards Remote Access VPN Wizard
Starting the Remote Access VPN Wizard
Configuring IPsec Remote Access Group Policy
Configuring Operation Mode
Configuring WAN Settings
Configuring DNS and Wins Settings
Configuring Access Control Settings
Viewing Group Policy Summary
Configuring Backup Servers
Configuring Split Tunneling
Viewing IPsec Remote Access Summary
Configuring IPsec Remote Access User Groups
Configuring SSL VPN Gateway
Using Remote Access VPN Wizard for SSL Remote Access
Client Netmask Client Address Pool
Configuring SSL VPN Group Policy
Configuration Wizards
Configuration Wizards
Configuring SSL VPN User Groups
Viewing SSL VPN Summary
Using the Site-to-Site VPN Wizard to Configure Site-to-Site
Starting the Site-to-Site VPN Wizard
Configuring VPN Peer Settings
Click Configuration Wizards Site-to-Site VPN Wizard
Configuring IKE Policies
Configuring Transform Policies
Configuring Local and Remote Networks
Configuring Ddns Profiles
Using the DMZ Wizard to Configure DMZ Settings
Click Configuration Wizards DMZ Wizard
Starting the DMZ Wizard
Configuring DMZ Network
Configuration Wizards
Configuring DMZ Services
WAN
Click Configuration Wizards Wireless Wizard
Using the Wireless Wizard for ISA550W and ISA570W only
Starting the Wireless Wizard
Configuring Wireless Connectivity Types
Configuring the Ssid for Intranet Wlan Access
Specify Wireless Connectivity Settings for All Enabled SSIDs
Configuring Wireless Security,
Configuring the Ssid for Guest Wlan Access
Configuration Wizards
Configuration Wizards
Configuration Wizards
Status Dashboard
Device Status Dashboard
Field Description
System Information
Resource Utilization
Status
Licenses
Syslog Summary
Routing Mode
Remote Access VPN
Site-to-Site VPN
Physical Ports
Field
Status Summary
Network Status
Status Summary
Ethernet
Vlan Pvid
DMZ
Vlan
Traffic Statistics
Traffic Statistics
Usage Reports
Status
WAN Bandwidth Reports
Dhcp Bindings
ARP Table
ARP Table
Dhcp Bindings
Interface Status Table
STP Status
STP Status Global Status
Status
CDP Neighbor
Wireless Status, Client Status,
Wireless Status for ISA550W and ISA570W only
Wireless Status
NAT Status
NAT Status
Client Status
IPsec VPN Status
VPN Status
IPsec VPN Status, SSL VPN Status,
VPN Status IPsec VPN Status
Statistics
VPN Status SSL VPN Status
SSL VPN Status
Teleworker VPN Client
SSL VPN Statistics
Active User Sessions
Active User Sessions
Web Security Report
Security Services Reports
Anti-Virus Report
Email Security Report
Network Reputation Report
IPS Report
Application Control Report
Processes
System Status
Processes, Resource Utilization,
System Status Processes
System Status Resource Utilization
Resource Utilization
CPU Utilization
Memory Utilization
Status
Networking
Viewing Network Status
Configuring IPv4 or IPv6 Routing
Managing Ports
Networking
Viewing Status of Physical Interfaces
Configuring Physical Ports
Configuring Port Mirroring
Configuring Port-Based 802.1x Access Control
Networking
Release or renew a Dhcp WAN connection,
Configuring the WAN
Configuring WAN Settings for Your Internet Connection
Configure the primary WAN
Networking
Network Addressing Mode
Configure a secondary WAN
Network Addressing Configuration Mode
Dhcp Client
Static IP
ISP
PPPoE
Pptp
L2TP
Dual WAN Settings
Networking
Configuring Link Failover Detection
Networking
Adding or modifying a Ddns service
Configuring Dynamic DNS
Ddns Services Table
Measuring and Limiting Traffic with the Traffic Meter
Networking
Configuring a Vlan
Networking
Networking
Networking
About DMZ networks
Configuring DMZ
Example DMZ with One Public IP Address for WAN and DMZ
Example DMZ with Two Public IP Addresses
Configuring a DMZ
Networking
Networking
Security Levels for Zones
Configuring Zones
Predefined Zones
Configuring Zones
Services
Configuring Routing
Configuring Dhcp Reserved IPs
Viewing the Routing Table
Configuring Routing Mode
Configuring Static Routing
Configuring Dynamic Routing RIP
Configuring Policy-Based Routing
Networking
Click Networking QoS General Settings
Configuring Quality of Service
General QoS Settings
Click Networking QoS WAN QoS Bandwidth
Configuring WAN QoS
Managing WAN Bandwidth for Upstream Traffic
Configuring WAN Queue Settings
Click Networking QoS WAN QoS Queue Settings
Configuring Traffic Selectors
Networking
Click Networking QoS WAN QoS QoS Policy Profile
Configuring WAN QoS Policy Profiles
Configuring WAN QoS Class Rules
Mapping WAN QoS Policy Profiles to WAN Interfaces
WAN QoS Configuration Example
WAN1IP
WAN1
Class Name
Configure WAN QoS for Voice Traffic from LAN to WAN
Source Address
Policy Name
QoS Class Rules
Configuring WAN QoS for Voice Traffic from WAN to LAN
QoS Class Rule
Configuring LAN QoS
Configuring LAN QoS Classification Methods
Configuring LAN Queue Settings
Click Networking QoS LAN QoS Queue Settings
Click Networking QoS LAN QoS Classification Methods
Mapping Dscp to LAN Queue
Mapping CoS to LAN Queue
LAN Queue CoS Value
Click Networking QoS LAN QoS Mapping CoS to Queue
Configuring Default CoS
Configuring Wireless QoS
Default Wireless QoS Settings
802.1p Priority 802.11e Priority
Click Networking QoS Wireless QoS Classification Methods
Configuring Wireless QoS Classification Methods
Ieee 802.11e to 802.1p Mapping
802.11e Priority 802.1p Priority
Mapping Dscp to Wireless Queue
Mapping CoS to Wireless Queue
Understanding Dscp Values
Dscp Value Decimal Value Meaning
011
Configuring Igmp
100
Click Networking Igmp
Click Networking Vrrp
Configuring Vrrp
Networking
Configuring Addresses, Configuring Address Groups,
Configuring Addresses
Address Management
Click Networking Address Management
Configuring Address Groups
Configuring Services
Service Management
Configuring Services, Configuring Service Groups,
Click Networking Service Management
Configuring Service Groups
Requirements
Configuring Captive Portal
Before You Begin
Vlan Setup
User Authentication
Configuring a Captive Portal
Wireless Setup
Networking
Networking
Networking
Troubleshooting
Using External Web-Hosted CGI Scripts
Networking
Networking
Networking
Networking
Networking
Networking
Networking
Networking
CGI Source Code Example No Authentication and Accept Button
Networking
Networking
Networking
Networking
Networking
If result == 2 result == 5 //document.form1.UserName.focus
Networking
Networking
Support
Related Information
Documentation
Cisco Small Business
Cisco Small Business Home
Wireless for ISA550W and ISA570W only
Viewing Wireless Statistics
Viewing Wireless Status
Wireless for ISA550W and ISA570W only
Wireless Wireless Status Wireless Status
Click Wireless Basic Settings
Configuring the Basic Settings
Viewing Wireless Client Status
Wireless for ISA550W and ISA570W only
Configuring Ssid Profiles
Open
Configuring Wireless Security
Security Mode Description
WPA
WEP
WPA + WPA2
WPA2
WPA/WPA2-Personal mixed Supports
WPA/WPA2-Enterprise mixed Supports
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Controlling Wireless Access Based on MAC Addresses
Mapping the Ssid to Vlan
Configuring Ssid Schedule
Click Wireless Wi-Fi Protected Setup
Configuring Wi-Fi Protected Setup
Wireless for ISA550W and ISA570W only
Configuring Captive Portal
Requirements
Configuring a Captive Portal
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Troubleshooting
Using External Web-Hosted CGI Scripts
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
CGI Source Code Example No Authentication and Accept Button
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
If result == 2 result == 5 //document.form1.UserName.focus
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Related Information
Click Wireless Rogue AP Detection
Configuring Wireless Rogue AP Detection
Click Wireless Advanced Settings
Advanced Radio Settings
Wireless for ISA550W and ISA570W only
Wireless for ISA550W and ISA570W only
Firewall
Firewall
About Security Zones
Security Levels and Predefined Zones Description
Click Firewall Access Control Default Policies
Default Firewall Settings
Priorities of Firewall Rules
Preliminary Tasks for Configuring Firewall Rules
Click Firewall Access Control ACL Rules
General Firewall Settings
Configuration Examples,
Configuring a Firewall Rule
Firewall
MAC Address Filtering to Permit or Block Traffic,
Configuring a Firewall Rule to Allow Multicast Traffic
Configuring Firewall Logging Settings
Configuring NAT Rules to Securely Access a Remote Network
Firewall NAT NAT Status
Viewing NAT Translation Status
Outbound Traffic
Priorities of NAT Rules
Inbound Traffic
Click Firewall NAT Dynamic PAT
Configuring Dynamic PAT Rules
Click Firewall NAT Static NAT
Configuring Static NAT Rules
Click Firewall NAT Port Forwarding
Configuring Port Forwarding Rules
Firewall
Click Firewall NAT Port Triggering
Configuring Port Triggering Rules
Click Firewall NAT Advanced NAT
Configuring Advanced NAT Rules
Configuring IP Alias for Advanced NAT rules
Http
As Any
From Any
Configuring an Advanced NAT Rule to Support NAT Hairpinning
Defaultnetwork
Default
FTP-CONTROL
WAN WAN1 WAN IP WAN1IP
Allowing Inbound Traffic Using the WAN IP Address
Firewall and NAT Rule Configuration Examples
ANY
Enable Port Forwarding
Translated IP InternalFTP
RDP
Allowing Inbound Traffic Using a Public IP Address
Translated IP RDPServer
WAN WAN1 WAN IP
Address Original Destination PublicIP Original Services
Netmask
Name
Port
Zone
Translated IP InternalIP
Enable Port Forwarding Create Firewall Rule Off
CU-SEEME
Schedule
Blocking Outbound Traffic by Schedule and IP Address Range
Blocking Outbound Traffic to an Offsite Mail Server
Click Firewall Content Filtering Content Filtering Policies
Configuring Content Filtering to Control Internet Access
Configuring Content Filtering Policy Profiles
Configuring Website Access Control List
Click Firewall Content Filtering Policy to Zone Mapping
Mapping Content Filtering Policy Profiles to Zones
Click Firewall Content Filtering Advanced Settings
Configuring Advanced Content Filtering Settings
Click Firewall MAC Filtering MAC Address Filtering
Configuring MAC Address Filtering to Permit or Block Traffic
Click Firewall MAC Filtering IP MAC Binding Rules
Configuring IP-MAC Binding to Prevent Spoofing
Click Firewall Attack Protection
Configuring Attack Protection
Click Firewall Session Limits
Configuring Session Limits
Click Firewall Application Level Gateway
Configuring Application Level Gateway
Firewall
Security Services
IPS
About Security Services
Priority of Security Services
Activating Security Services
Click Security Services Dashboard
Security Services Dashboard
Viewing Security Services Reports
Viewing IPS Report, Viewing Application Control Report,
Viewing Web Security Report
Viewing Anti-Virus Report
Viewing Email Security Report
System Date
Viewing Network Reputation Report
Total Since Activated
Total Last 7 Days
Graph
Viewing IPS Report
Total Today
Viewing Application Control Report
Configuring Anti-Virus
Click Security Services Anti-Virus General Settings
General Anti-Virus Settings
Notify + Drop Connection Drop the connection
Protocol Action
Http Notification,
FTP
Cifs
Netbios
Notification,
Click Security Services Anti-Virus Advanced Settings
Configuring Advanced Anti-Virus Settings
Configuring Email Notification
Configuring Http Notification
Click Security Services Anti-Virus Http Notification
Click Security Services Anti-Virus Email Notification
Updating Anti-Virus Signatures
Updating Application Signature Database,
Configuring Application Control
Important Tips
Configuring Application Control Policies
General Application Control Policy Settings
Adding an Application Control Policy
Security Services
Permitting or Blocking Traffic for an Application
General Application Control Settings
Mapping Application Control Policies to Zones
Enabling Application Control Service
Configuring Application Control Policy Mapping Rules
Updating Application Signature Database
Click Update Database
Advanced Application Control Settings
Click Security Services Spam Filter
Configuring Spam Filter
Security Services
Configuring Intrusion Prevention
Security Services
Configuring Signature Actions
Updating IPS Signature Database
Configuring Web Reputation Filtering
Click Security Services Web Reputation Filtering
Configuring Web URL Filtering
Click Security Services Web URL Filtering Policy Profile
Configuring Web URL Filtering Policy Profiles
Configuring Website Access Control List
Mapping Web URL Filtering Policy Profiles to Zones
Configuring Advanced Web URL Filtering Settings
Click Security Services Web URL Filtering Advanced Settings
Security Services
Network Reputation
VPN
About VPNs
Viewing IPsec VPN Status
Viewing VPN Status
Viewing IPsec VPN Status, Viewing SSL VPN Status,
VPN VPN Status IPsec VPN Status
Field Description
VPN VPN Status SSL VPN Status
Viewing SSL VPN Status
SSL VPN Statistics
VPN
Site-to-Site VPN
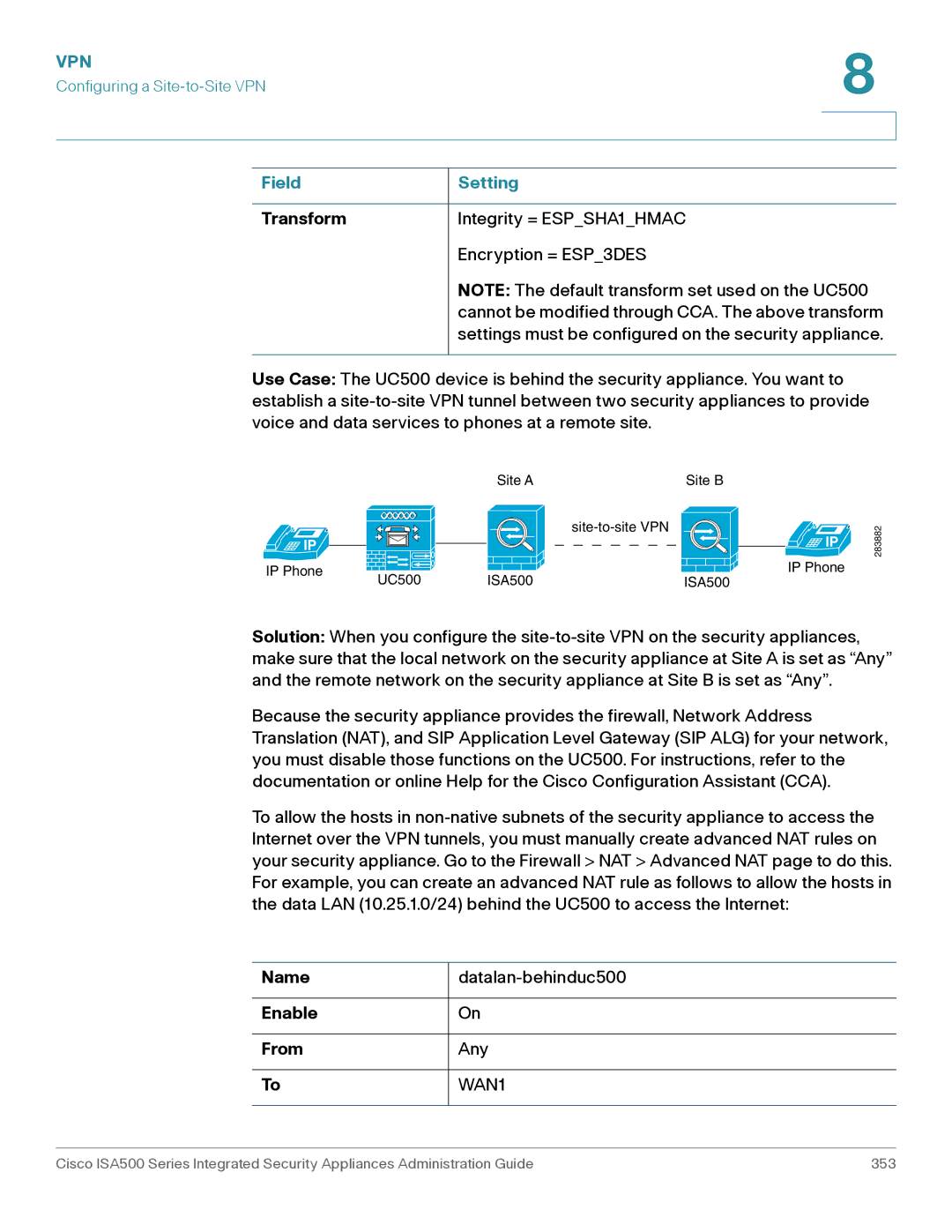
Configuring a Site-to-Site VPN
Click VPN Site-to-Site IPsec Policies
Configuration Tasks to Establish a Site-to-Site VPN Tunnel
General Site-to-Site VPN Settings
VPN
Configuring IPsec VPN Policies
VPN
VPN
VPN
283058
VPN
Click VPN Site-to-Site IKE Policies
VPN
Click VPN Site-to-Site Transform Policies
Configuring Transform Sets
Field Setting
Remote Teleworker Configuration Examples
Remote Network
IKE Policy
Transform
Name Enable From
Address Translated
Destination Address Translated Services
Configuring IPsec Remote Access
Then choose Cisco VPN Client
Cisco VPN Client Compatibility
Click VPN IPsec Remote Access
Enabling IPsec Remote Access
Configuring IPsec Remote Access Group Policies
VPN
VPN
IKE Authentication
Allowing IPsec Remote VPN Clients to Access the Internet
Group Name
WAN Interface
Client Internet Disable Access WAN Failover
Mode Client Pool Range for Client Start IP
Name VPNClienttoWAN1 Enable From Any
LAN
WAN2IP
Name VPNClienttoWAN2 Enable From Any
WAN2
Translated Any Destination Address Translated Services
Configuring Teleworker VPN Client
Transform Set
Required IPsec VPN Servers
Client Mode,
Benefits of the Teleworker VPN Client Feature
Modes of Operation
Network Extension Mode,
Client Mode
IPsec VPN Network Extension Connection
Network Extension Mode
Click VPN Teleworker VPN Client
General Teleworker VPN Client Settings
Configuring Teleworker VPN Client Group Policies
VPN
VPN
Configuring SSL VPN
Elements of the SSL VPN
SSL Remote User Access
Configuration Tasks to Establish a SSL VPN Tunnel
Installing Cisco AnyConnect Secure Mobility Client
Configuring SSL VPN Users
Importing Certificates for User Authentication
Configuring SSL VPN Gateway
Click VPN SSL Remote User Access SSL VPN Configuration
Client Netmask Client Address Pool
VPN
Click VPN SSL Remote User Access SSL VPN Group Policies
Configuring SSL VPN Group Policies
VPN
VPN
Allowing SSL VPN Clients to Access the Internet
Accessing SSL VPN Portal
Name SSLVPNtoWAN1 Enable From Any
Enable From Any
Address Original Destination Any Original Services
Sslvpnaddresspool
Name SSLVPNtoWAN2 Enable From Any
Click VPN L2TP Server
Configuring L2TP Server
Service
Click VPN VPN Passthrough
Configuring VPN Passthrough
Users Active User Sessions
Viewing Active User Sessions
Default User and User Group
Configuring Users and User Groups
Available Services for User Groups
User Management
Click Users Users and Groups
Preempt Administrators
Configuring Local Users
Configuring Local User Groups
User Management
Configuring User Authentication Settings
Click Users User Authentication
Using Local Database for User Authentication
Using Radius Server for User Authentication
Local Database Settings Radius Server Settings
Local Radius Server Settings Database
Click Users User Authentication
Using Ldap for User Authentication
User Management
Using Local Database and Ldap for Authentication
Click Users Radius Servers
Configuring Radius Servers
User Management
Device Management
Viewing Resource Utilization
Viewing System Status
Viewing Process Status
Administration
Configuring Administrator Settings
Example https//209.165.201.18080
Configuring Email Alert Settings
Click Device Management Administration Email Alert
CPU Overload Alert
Event Description
New Firmware Alert
Your Firmware from Cisco.com,
Log Facilities,
Settings page. See Configuring Log Settings,
Security License,
WAN Up/Down Alert
Check Site-to-Site VPN Up/Down Alert in the Enable column
Up/Down Alert
Anti-Virus Alert
Traffic Meter Alert
IPS Alert
Settings. See Configuring Application Control,
Click Device Management Administration Snmp
Configuring Snmp
Click Device Management Backup/Restore
Backing Up and Restoring a Configuration
Device Management
Managing Certificates for Authentication
Click Device Management Certificate Management
Viewing Certificate Status and Details
Certificate Type Details
Exporting Certificates to Your Local PC
Importing Certificates from Your Local PC
Exporting Certificates to a USB Device
Generating New Certificate Signing Requests
Importing Certificates from a USB Device
Importing Signed Certificate for CSR from Your Local PC
Configuring Cisco Services and Support Settings
Configuring Cisco OnPlus
Sending Contents for System Diagnosis
Configuring Remote Support Settings
Click Device Management Date and Time
Configuring System Time
Diagnostic Utilities
Configuring Device Properties
Click Device Management Device Properties
Ping, Traceroute, DNS Lookup, Packet Capture,
Click Device Management Diagnostic Utilities Traceroute
Click Device Management Diagnostic Utilities Ping
Ping
Traceroute
DNS Lookup
Device Discovery Protocols
Packet Capture
UPnP Discovery, Bonjour Discovery, CDP Discovery,
Click Device Management Discovery Protocols UPnP
UPnP Discovery
Lldp Discovery,
CDP Discovery
Bonjour Discovery
Click Device Management Discovery Protocols Bonjour
Click Device Management Discovery Protocols CDP
Click Device Management Discovery Protocols Lldp
Lldp Discovery
View the firmware status. See Viewing Firmware Information,
Firmware Management
Firmware Version area, click Switch Firmware
Using the Secondary Firmware
Viewing Firmware Information
Click Device Management Firmware
Upgrading your Firmware from Cisco.com
Upgrading Firmware from a PC or a USB Device
Firmware Auto Fall Back Mechanism
Using Rescue Mode to Recover the System
Managing Security License
Click Device Management License Management
Checking Security License Status
Installing or Renewing Security License
Click Device Management Logs View Logs
Log Management
Viewing Logs
Click Query
Click Device Management Logs Log Settings
Configuring Log Settings
Emergency level
Severity Level Description
Critical level
Notification level
Device Management
Click Device Management Logs Logs Facilities
Configuring Log Facilities
Reset Device area, click Reset to Factory Defaults
Rebooting and Resetting the Device
Click Device Management Reboot/Reset
Click Device Management Schedules
Configuring Schedules
Rebooting the Security Appliance
Device Management
Device Management
Device Management
Recommended Actions
Internet Connection
Click Status Dashboard
Troubleshooting
Recommended Actions Click Networking WAN WAN Settings
Date and Time
Enable the Daylight Saving Time Adjustment feature
Date and Time
Pinging to Test LAN Connectivity
Testing the LAN Path from Your PC to Your Security Appliance
Testing the LAN Path from Your PC to a Remote Device
ISA570
Feature ISA550
Physical Specifications
Internal Power Supply
Device Management
Feature Setting
Remote Administration
Snmp
Factory Default Settings
CDP
Lldp
Local Users
User Management
User Groups
Networking
User Authentication Methods
IPv4 or IPv6 Routing
Network Addressing Modes
VLANs
Port-based Access Control
WAN Redundancy Operation Modes
Routing
Zones
Vrrp
LAN QOS
Wireless
Rogue AP Detection
Wi-Fi Protected Setup WPS
Captive Portal
IKE Policies
SSL VPN
IPsec Remote Access
Firewall
Security Services
Features Setting
NAT
Content Filtering
MAC Address Filtering
IP MAC Binding
Reports
Service Name Protocol Port Description Start End
Default Service Objects
FTP-DATA TCP
IKE UDP
Rtelnet TCP
Address Name Type IP, IP/Netmask, or IP Range
Default Address Objects
Support
Product Resources
Product Documentation
Cisco Small Business