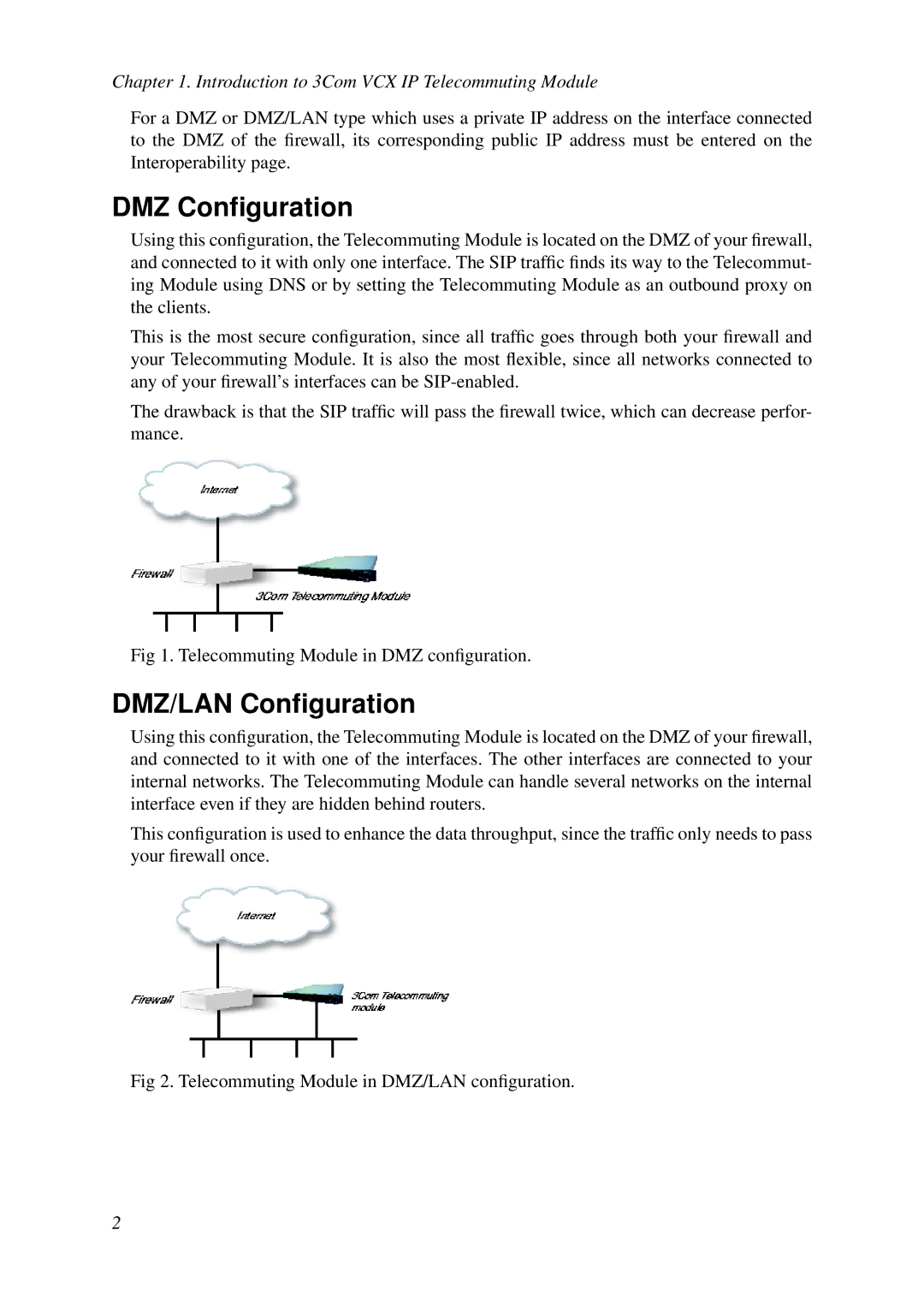
3Com Telecommuting Module
Version
Page
United States Government Legend
Page
Table of Contents
Page
Part I. Introduction to 3Com VCX IP Telecommuting Module
Page
Introduction to 3Com VCX IP Telecommuting Module
What is a Telecommuting Module?
Configuration alternatives
DMZ Configuration
DMZ/LAN Configuration
Quick guide to 3Com VCX IP Telecommuting Module installation
Standalone Configuration
Introduction to 3Com VCX IP Telecommuting Module
About settings in 3Com VCX IP Telecommuting Module
Introduction to 3Com VCX IP Telecommuting Module
Installation with magic ping
Installing 3Com VCX IP Telecommuting Module
Installation
Installation with a serial cable
Page
Page
Page
Page
Installation with a diskette
Page
Page
Turning off a Telecommuting Module
Remember to lock up the Telecommuting Module
Installing 3Com VCX IP Telecommuting Module
Logging on
Configuring 3Com VCX IP Telecommuting Module
Log on again
Log out
Navigation
Site Map
Basic Configuration
Administration
SIP Services
Network Configuration
Failover
Quality of Service
Overview of configuration
Virtual Private Networks
Preliminary and permanent configuration
Page
IP address
Mask/Bits
Name queries in 3Com VCX IP Telecommuting Module
No. of computers Mask Bits
Page
Configuring 3Com VCX IP Telecommuting Module
Part II. How To
Page
DMZ Telecommuting Module, SIP server on the WAN
How To Configure SIP
Networks and Computers
Surroundings
Basic Settings
Interoperability
Filtering
Routing
DMZ Telecommuting Module, SIP server on the LAN
Save/Load Configuration
Networks and Computers
Basic Settings
Routing
Standalone Telecommuting Module, SIP server on the WAN
Basic Settings
Filtering
Client Settings
Standalone Telecommuting Module, SIP server on the LAN
Basic Settings
Interoperability
DMZ/LAN Telecommuting Module, SIP server on the WAN
Basic Settings
Filtering
DMZ/LAN Telecommuting Module, SIP server on the LAN
Interoperability
Filtering
LAN Telecommuting Module
Surroundings
Filtering
Remote SIP Connectivity
Firewall
How To Configure SIP
How To Configure Advanced SIP
Outgoing Calls
Show One Number When Calling
Show Different Numbers When Calling
Incoming Calls
Page
Authentication by Accounts a.k.a SIP Trunk via SIP accounts
Page
Page
Page
Incoming Calls
Page
Multiple Operators Least Cost Routing
Page
Multiple PBXs
How To Configure Advanced SIP
How To Configure Advanced SIP
Page
Page
Page
Page
General
Basic Configuration
Basic Configuration
Name of this Telecommuting Module
DNS Servers
Default domain IP Policy
Policy For Ping To Your 3Com VCX IP Telecommuting Module
Save
Access Control
Cancel
Look up all IP addresses again
Configuration Allowed Via Interface
User Authentication For Web Interface Access
Configuration Transport
Configuration via Http
Configuration via Https
Configuration via SSH
Configuration Computers
DNS Name Or Network Address
Range
Network address
Netmask/Bits
Via IPsec Peer
Radius
Port
Radius Servers
Radius server
Secret
Contact IP Address
Identifier
Status for Radius Servers
Received replies
Score
Sent requests
Consecutive sends
Configuration of a Radius server
Value
Contact person
Snmp v1 and v2c
Telecommuting Module IP address to respond to Snmp requests
Node location
Snmp
Access via SNMPv1 and SNMPv2c
Access via SNMPv3
Community
Snmp Traps
Password
Authentication
User
Trap receiver
Resource Monitoring
Trap sending function
Version
SIP User Registrations Trap Levels
Download the 3Com MIB
SIP Sessions Trap Levels
CPU Load Trap Levels
DynDNS General Configuration
Dynamic DNS update
DynDNS service
Use DynDNS
Wildcard hostnames Offline URL redirection
IP address for updates
User, Smtp Server
Username
Smtp server
DNS Names to Update at DynDNS
Smtp server is backup
DNS Name
Name
Certificates
Private Certificates
Certificate
Create certificate or certificate request
CA Certificates
Advanced
Timeouts
CA Certificate
Timeout for established TCP connections
Timeout for one-way UDP connections
Timeout for two-way UDP connections
Timeout for Icmp connections
DMZ/LAN Configuration
Current Telecommuting Module Type
Telecommuting Module Type configuration
Change Telecommuting Module Type to
Change type
Save/Load Configuration
Administration
Duration of limited test mode
Test Preliminary Configuration
Show Message About Unapplied Changes
Backup
Apply configuration
Save/Load CLI Command File
Abort All Edits
Show Configuration
Revert to Old Configurations
Reload Factory Configuration
Password For the ’admin’ Account
User Administration
Old password
Other Accounts
New password, Confirm password
Change administration password
Account Type
Currently Logged In Administrators
Log Out
Upgrade
Upgrade
Step
Abort upgrade
Try the upgrade
Accept upgrade
Table Look
Edit Column
Date and Time
Change Time Zone
Time
Change Date and Time Manually
Date
Set date and time manually
Change Date and Time With NTP
NTP Servers To Use If NTP Is Enabled
Synchronize time with NTP
Restart the SIP Module
Reboot Your 3Com VCX IP Telecommuting Module
Restart
Automatic Restart of the SIP Module
Administration
Administration 118
Network Configuration
Networks and Computers
Subgroup
Name
Lower Limit
Delete Row
Upper Limit
Interface/VLAN
Create
Priority
Default Gateway
Main Default Gateways
Interface
Policy For Packets From Unused Gateways
Gateway Reference Hosts
Physical device
Interface Network Interface 1
Interface name
Directly Connected Networks
Obtain IP Address Dynamically
Vlan Id
Alias
Broadcast address
Vlan Name
Static Routing
Routed network
Router
Vlan
Named VLANs
Interface Status
Interface Status
Dhcp Client Status
PPPoE Client Status
PPPoE
Authentication
Keep Alive
LCP echo-request interval
Surroundings
Log class for PPPoE negotiations
Network
Data Interfaces
Additional Negotiators
Select a data interface here
Network Configuration 136
Search the Log
Logging
Display Log
Display log
Support Report
Packet Selection
Protocol/Port Selection
Packet Type Selection
IP Address Selection
All IP protocols
Icmp
SIP Methods
SIP Packet Selection
Call-ID
IP addresses
Time Limits
Export the Log
Show This
Show newest at top
Log
Clear form
Display Load
RST
Direction
Packet Load
Time Period
Unit
Value
Diagram Heading
Diagram
Diagram Size
View diagram
Log class for spoofed packets
Inbound Traffic
Log class for non-SIP packets
Log class for broadcast packets
Log class for Snmp errors
Log class for email errors
Log class for Radius errors
Log class for Dhcp requests
Log class for IPsec key negotiation debug messages
VPN Events
Log class for IPsec key negotiations
Log class for ESP packets
SIP Events
Other
Email Address
Log Classes
Local Log
Log Sending
Syslog
Status for Outbound Email
Smtp Server
Syslog Servers
Reverts the fields to the previous configuration 157
Logging 158
Basic Settings
SIP Services
Administration of SIP
SIP Module
Transport
Additional SIP Signaling Ports
Provisioning Relay
Comment
Public IP address for NATed Telecommuting Module
SIP Media Port Range
SIP Servers To Monitor
SIP Logging
Server
Log class for SIP signaling
Loose Routing
Interoperability
Relaxed Refer-To
SIP Server
Remove Via Headers
Translation Exceptions
Except this from translation
Force Translation
Expires Header
Always Translate This
URI Encoding
Loose Username Check
Signaling Order of Re-INVITEs
User Matching
Force Record-Route for Outbound Requests
Accept RTP/AVP With sdescriptions
Transmit RTP/AVP With sdescriptions
Force Record-Route for All Requests
Force Remote TLS Connection Reuse
Accept TCP Marked As TLS
Allow Large UDP Packets
Remove Headers in 180 Responses
Use Cancel Body In ACK
Forward Cancel Body
Preserve RFC 2543 Hold
Open Port 6891 For File Transfer
Allow RFC 2069 Authentication
Convert Escaped Whitespaces in URIs
Strip ICE Attributes
Keep User-Agent Header When Acting as B2BUA
Ports and the maddr Attribute
Sessions and Media
Session timer
Timeout for SIP over TCP/TLS
Session Configuration
Allowed number of concurrent sessions
Media Configuration
Limitation of sender of media streams
Limitation of RTP Codecs
Name
Codecs
Type
This Codec Is Allowed
Local Ringback Played at Call Transfer
Local Ringback
Music on Hold Redirection
Ring Tone for Local Ringback
Requests
Default timeout for Invite requests
Maximum timeout for Invite requests
SIP blacklist interval
Maximum number of retransmissions for Invite requests
Base retransmission timeout for SIP requests
Remote SIP Connectivity
Maximum number of retransmissions for non-INVITE requests
Stun server IP addresses
Stun Server
Stun server
Stun ports
Remote NAT traversal
Remote Clients Signaling Forwarding
Remote NAT Traversal
IP Address for Remote Clients
Forward Signaling from IP Address
NAT timeout for UDP
NAT timeout for TCP
NAT keepalive method
SIP Traffic
SIP Methods
Allow
Method
Traffic To
Auth
From Network
Filtering
Sender IP Filter Rules
Action
Content Type
Content Types
Default Policy For SIP Requests
Allow
Header Filter Rules
Local Registrar
Default Header Filter Policy
Local SIP Domains
Local SIP User Database
Domain
Authentication Name
Authentication and Accounting
Register From
Authentication settings
SIP User Database
Trusted Domains
Asserted-Identity
Use P-Asserted-Identity
Network
Use Dial Plan
Dial Plan
Radius Accounting
Emergency Number
Matching From Header
Reg Expr
Head
Matching Request-URI
Prefix
Tail
Forward To
Min. Tail
Replacement URI
Subno
Dial Plan
Add Prefix
Request-URI
Forward To
Enum Root
Method
Methods in Dial Plan
Register in Dial Plan
Routing
Enum Root
DNS Override For SIP Requests
Relay To
Weight
SIP Routing Order
Port
Class 3xx Message Processing
Routing Function
Also Forward To
Static Registrations
Requests To User
User
For clients not supporting Refer
Local Refer Handling
Always handle Refer locally
Sip/sips
For dialogs with specified User-Agent header
For clients not supporting replaces
For dialogs with specified From URI
From URIs For Which Refer is Handled Locally
Alias
User Routing
Restrict Incoming Callers
Send To Voice Mail
Forward
Action
Voice Mail Server
Request-URI Domain
Outbound Proxy
From Domain
Domain or IP Address
Tel URIs
Gateway
Active Sessions
Registrar and Session Status
Monitored SIP Servers
Monitored SIP server status
Registered Users
Monitored SIP server
Registered from
Network Interface Selection
Tools
Packet Capture
IP Address Selection
Tools Any
Icmp
Check Network
Check Network
Collect data
Test Results
Page
Tools 222
SIP over UDP
Firewall and Client Configuration
DMZ type
SIP over TCP/TLS
DMZ/LAN type
SIP clients
Standalone type
SIP clients
Part IV Com VCX IP Telecommuting Module Serial Console
Page
Connecting to the serial console
Basic Administration
Main Menu
Exit admin
Set password
Command line interface
Wipe email logs
Physical device name
Deactivate other interfaces
Configure from a single computer
Configure from multiple computers
Password
Wipe email logs
Set password
Exit admin
Basic Administration 236
Command Reference
Command Line Reference
Help and Troubleshooting
Modifying Tables
Modify-row
List-tables
Load-factory
Revert-edits
Table Definitions
Config.allowviainterface
Config.allowconfig
Config.authlogclass
Config.httpsservers
Config.authentication
Config.httpservers
Config.mgmtlogclass
Fentalwaysfentexceptions
Failover.ifacerefhosts
Fent.alwaysfent
Fentalwaysfentinterfaces
Fent.fentkeepalive
Fent.mapsignaladdress
Field Name Field Type Explanation Enabled OnOffToggle
Fent.mediarelease
firewall.broadcastlogclass
firewall.defaultpolicy
firewall.blindroutepolicy
firewall.dhcplogclass
firewall.ownlogclass
firewall.networkgroups
firewall.pingpolicy
firewall.spoofinglogclass
firewall.services
firewall.policylogclass
firewall.timeclasses
Idsips.active
Idsips.predefinedipsrules
Ipsec.espproposals
Idsips.ratelimitedips
Ipsec.cryptodef
Ipsec.espahlogclass
Ipsec.ipsecnets
Ipsec.ikelogclass
Ipsec.ikeproposals
Ipsec.nattkeepalive
Ipsec.radiusauthserver
Ipsec.plutologclass
Ipsec.plutoverboselogclass
Field Name Field Type
Ipsec.userauthlogclass
Ipsec.tunnelednets
Ipsec.x509cacerts
Misc.dnsservers
Misc.conntracktimeouts
Ipsec.x509cert
Misc.dyndns
Misc.ntpservers
Misc.dyndnsname
Misc.fversion
Field Name Field Type Explanation DomainName
Misc.usentp
Monitor.cpuloadlevelalarm
Misc.unitname
Monitor.emailalertlogclass
Monitor.hardwarelogclass
Monitor.memorylevelalarm
Monitor.radiuserrorslogclass
Monitor.logclasses
Monitor.snmpagentaddress
Monitor.siplevelalarms
Monitor.snmpagentlogclass
Monitor.snmpnodelocation
Monitor.snmpcontactperson
Monitor.snmpmanagementstations
Monitor.snmppacketlogclass
Monitor.snmptrapsending
Monitor.snmpv1v2caccess
Monitor.snmpv3access
Monitor.snmpv1v2cauth
Monitor.watchdogs
Network.extradefaultgateways
Monitor.syslogservers
Network.aliasaddresses
Network.localnets
Network.interfaces
Network.pppoe
Network.vlans
Network.routetestservers
Network.routes
Field Name Field Type Explanation Server DnsIpAddress
Pptp.grelogclass
Password.adminusers
Pptp.pptpenable
Pptp.pptplogclass
Pptp.pptpneglogclass
Pptp.pptpserverip
Pptp.pptpusers
Field Name Field Type Explanation PPTPOwnIpReference
Qos.bandwidths
Qos.classes
Qos.ingressdefaultqueueing
Qos.egressdefaultqueueing
Qos.egressqueueing
Qos.status
Qos.ingressqueueing
Qos.sipcac
Qos.tagging
Sip.addexpireheader
Sip.acceleratedtls
Sip.active
Sip.allowedcodecs
Sip.b2buaofferfromtemplate
Sip.defaultgateway
Sip.authmethods
Sip.codecfiltering
Sip.externalrelay
Sip.emergency
Sip.externradiusdb
Field Name Field Type Explanation DnsIpAddress
Sip.forcemodify
Sip.forwardcancelbody
Sip.fixfiletransferport
Sip.forwardtoheader
Sip.ignoreuriportwhenmaddr
Sip.headerfilterdefault
Sip.headerfilterrules
Field Name Field Type Explanation Action Sipfilteractionsel
Sip.listen
Sip.largeudp
Sip.lcscompanion
Sip.localdomains
Sip.lrtrue
Sip.loosereferto
Sip.looseusernamecheck
Sip.mediaencryptionpolicy
Sip.mediaports
Sip.mediaencryptionsettings
Sip.mediaencryptionsuite
Field Name Field Type Explanation Portslower PortNumber
Sip.message
Sip.mediatimeouts
Sip.mediarestriction
Sip.mfull
Sip.monitorserver
Sip.optiontimeout
Sip.mimetypes
Sip.musiconhold
Sip.percent20towhitespace
Field Name Field Type Explanation Timeout OptionTimeout
Sip.outboundproxy
Sip.preserve2543hold
Sip.registrarlimits
Sip.radiusacct
Sip.recurseon3xxinb2bua
Sip.relayrules
Sip.rewritetoforregisterindp
Sip.removevia
Sip.replyconfig
Sip.ringback
Sip.rroutealways
Sip.routeusesport
Sip.routingorder
Sip.rrouteoutbound
Sip.sessionlimits
Sip.signaladdressfordestination
Sip.siperrorslogclass
Sip.sipalias
Sip.sipmedialogclass
Sip.sipsignalinglogclass
Sip.siplicenselogclass
Sip.sipmessagelogclass
Sip.stripiceattributes
Sip.tcptimeout
Sip.sttype
Sip.surroundings
Sip.tlsclientcfg
Sip.tlssettings
Sip.tlscacerts
Sip.tlsservercfg
Sip.uriencoding
Sip.transactionconfig
Sip.trusteddomain
Field Name Field Type Explanation Uriencodingsel
Sipswitch.b2buatransferenable
Sip.usecancelbodyinack
Sipswitch.accounts
Sip.uaregister
Sipswitch.dialplanenable
Sipswitch.b2buatransferfromuser
Sipswitch.dialplan
Field Name Field Type Explanation User AliasAlias
Sipswitch.forwardto
Sipswitch.dialplanmethods
Sipswitch.enumroot
Field Name Field Type Explanation Enabled Fallbacksel
Sipswitch.requestto
Sipswitch.incomingunauth
Sipswitch.requestfrom
Field Name Field Type Explanation Url SipWildcardUrl
Sipswitch.userrouting
Sipswitch.users
Userdb.radiusservers
Sipswitch.voicemail
Userdb.radiuslocalendpoint
Voipsm.voipsm
Field Types
AdminPassword
AdminTypeSel
Voipsm.voipsmdomains
AliasIpReference AliasUser
AdminUser
AliasAlias
AuthData
CryptoDefReference DepUsableVlanInterface DnsDynIpAddress
CaReference
CertReference
DnsDynIpNetworkInterface DnsDynIpOtherHost
EnumReference
DyndnsPassword
DyndnsServiceSel
EspCryptoReference FirewallLogclassReference
IpsRuleName
InterfaceSel
InviteRetransmitCount
IpsecAuthSel
MaxMessageSizeInteger
IsakmpSALife
LogclassReference
MaxReg
OnOffToggle
NonemptyString
OnOffButton
OnOffToggleOn
OptDSCPInteger
OptDnsAutoRuntimeReachableHost OptDnsIpAddress
OptComment
OptDepOwnIpReference
OptIpsecNetReference
OptForwardToReference
OptIcmpRangeList
OptIpsecPeerReference
OptPercent
OptPassword
OptServicesReference
OptPercentFloat
OptString
OptionTimeout
OptSipUserDomain
OptTimeclassReference
PPTPOwnIpReference
PptpPassword
RegTimeout
Percent
SipUserPassword
SessionTimeout
SipUserDomainDefaultAll
SIPRadiusSel
SipWildcardUrl
SnmpPassword
TimerAFloat
SubGroup
Accounttypesel
Accountvoicemailsel
Blindsel
Addexpireheadersel
Autonegsel
Bypasstransportsel
Fallbacksel
Configauthsel
Dpactionsel
Fentkeepalivesel
Hitsnumber
Functionsel
Fwtypesel
Mediaencryptionsuitesel
Pqueuesel
Pingpolicysel
Policysel
Qostypesel
Restfuncsel
Rfc2782weight
RegexpwithAt
Rfc2782priority
Sipfunctionsel
Sipauthdirsel
Sipfilteractionsel
Sipsel
Snmpv3privacysel
Snmptrapversionsel
Snmpv3authsel
Sttypesel
Tlsclientmethods
Sysloglevelsel
Tlsservermethods
Uriencodingsel
Tlsconfsel
Trusteddomaintransportsel
Voipsmmethodsel
Add and change firewall rules
CLI command examples
Windownumber
Apply a configuration
Part V. Appendices
Page
Appendix A. More About SIP
Why use SIP?
SIP Protocol
SIP and Firewalls
Managing Your Own SIP Domain
Configuring the 3Com VCX IP Telecommuting Module
Page
Configuring the DNS Server
Configuring the PBX
Configuring the SIP Clients
SIP in 3Com VCX IP Telecommuting Module
SIP Sessions
Establishing a SIP session
SIP Packet Headers
Contact
Record-Route
Content-Type
Via
Route
Appendix A. More About SIP 328
No traffic shown in the log
Appendix B. Troubleshooting
Network troubleshooting
Traffic discarded as spoofed
SIP users can’t register through the Telecommuting Module
SIP troubleshooting
SIP users can’t register on the Telecommuting Module
SIP Trunking calls via SIP operator
Administration troubleshooting
Call is established, but there is no voice
SIP send failure -1 on socket -1 event number
SIP errors
Log Messages
Destination IP addressport is known bad. Skipping
Starting SIP UDP server at port
IPsec key negotiations
Starting SIP TCP server at port
Stopped SIP TCP server
Configuration server logins
List of the most important reserved ports
Name Port/protocol Description
WWW
Cmip
Krcmd Kerberos encrypted remote shell -kfall
List of Icmp types
Type Name
Type Name Reference
Icmp codes
Icmp type Name Code Description
Unreachable for Type
Internet protocols and their numbers
Protocol number Keyword
IP intervals
Set bits Mask IP address class
Reserved IP addresses
Class IP in- tervals
Page
Appendix D. Definitions of terms
ARP
DMZ
349
Https
NAT
Nntp
353
PPP
SIP
Uucp
357
Appendix D. Definitions of terms 358
BSD derived licenses
Appendix E. License Conditions
Software developed by Peter Åstrand
Terms
Software developed by Carnegie Mellon University
Software developed by Gregory M Christy
Software developed by Cisco Systems
Software developed by Digital Equipment Corporation
Dhcp license
Software developed by Jason Downs
Software developed by Brian Gladman
Version 2, June
Software developed by Google, Inc
GNU General Public License GPL
Preamble
GNU General Public License
367
368
No Warranty
IBM Public License
Software developed by Ingate Systems
Software developed in the GIE Dyade cooperation
Software developed by Tommi Komulainen
GNU Library General Public License Lgpl v
USA
374
GNU Library General Public License
376
377
Page
379
380
GNU Lesser General Public License Lgpl v
Version 2.1, February
382
GNU Lesser General Public License
384
385
386
Page
Glibc Tzdata 2006a 388
Software in the GNU C distribution
Appendix E. License Conditions
Appendix E. License Conditions
392
More software in the GNU C distribution
394
License exceptions for gcc/libgcc2.c
License
License exceptions for libstdc++
License for lilo
Disclaimer
Software developed by Paul Mackerras
Software developed by Pedro Roque Marques
Software developed at M I T
License for Net-SNMP
Part 1 CMU/UCD copyright notice BSD like
Part 4 Sun Microsystems, Inc. copyright notice BSD
Part 5 Sparta, Inc copyright notice BSD
Part 6 Cisco/BUPTNIC copyright notice BSD
License for NTP
License for OpenSSH
404
Appendix E. License Conditions
406
407
Snprintf replacement Copyright Patrick Powell
409
License for OpenSSL
License for OpenSWAN
Python license
Release Derived Year Owner GPL- compatible? From
Terms and Conditions for Accessing or Otherwise Using Python
Beopen Python Open Source License Agreement Version
Cnri License Agreement for Python
License for Python Imaging Library
CWI License Agreement for Python 0.9.0 Through
License for Rdisc
Software developed by RSA Data Security, Inc
More software developed by RSA Data Security, Inc
License for SSL
License for stunnel
Software developed by Sun Microsystems, Inc
More software developed by Sun Microsystems, Inc
License for Sun RPC
License for termcap
Software developed by Trusted Information Systems, Inc
Software developed by Andrew Tridgell
Software developed by Paul Vixie
Software developed by Rayan S Zachariassen
Vovida Software License v
Vovida Software License, Version
License for zlib
Software developed at University of California
Openswan-kernel
427
Appendix E. License Conditions
Appendix E. License Conditions Readlink
Appendix E. License Conditions 430
Purchase Extended Warranty Professional Services
Register Your Product to Gain Service Benefits
Solve Problems Online
Appendix F. Obtaining Support for Your 3Com Products
Telephone Technical Support and Repair
Access Software Downloads
Contact Us
Asia, Pacific Rim Telephone Technical Support and Repair
Latin America Telephone Technical Support and Repair
Country Telephone Number
US and Canada Telephone Technical Support and Repair
For administration
Index
Configuration logins
From the Telecommuting Module
MIBs