Chapter 6
Advanced Virtual Private Networking
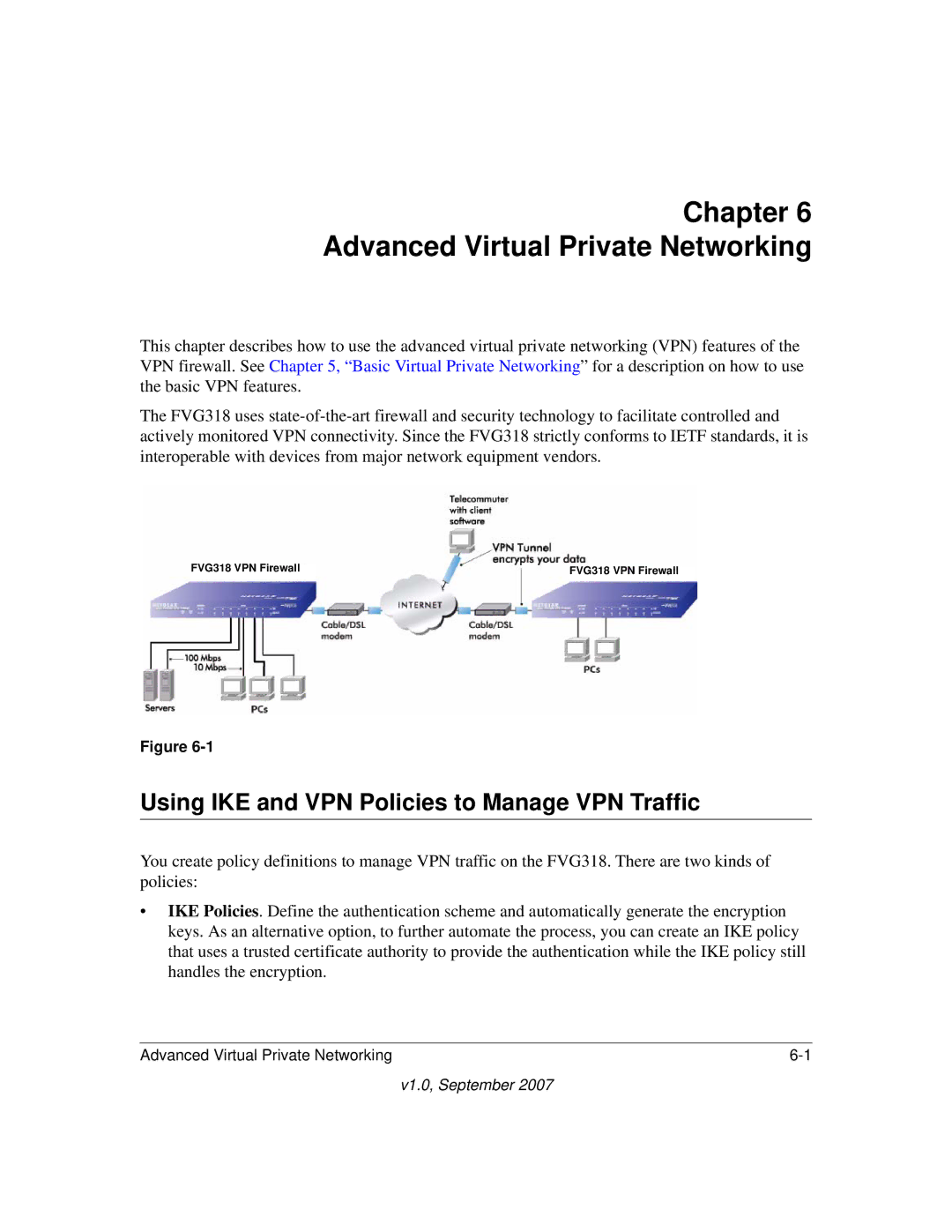
This chapter describes how to use the advanced virtual private networking (VPN) features of the VPN firewall. See Chapter 5, “Basic Virtual Private Networking” for a description on how to use the basic VPN features.
The FVG318 uses
|
|
|
FVG318 VPN Firewall |
| |
FVG318 VPN Firewall | ||
|
|
|
Figure
Using IKE and VPN Policies to Manage VPN Traffic
You create policy definitions to manage VPN traffic on the FVG318. There are two kinds of policies:
•IKE Policies. Define the authentication scheme and automatically generate the encryption keys. As an alternative option, to further automate the process, you can create an IKE policy that uses a trusted certificate authority to provide the authentication while the IKE policy still handles the encryption.
Advanced Virtual Private Networking |