Appendix D Wireless LANs
Security Parameters Summary
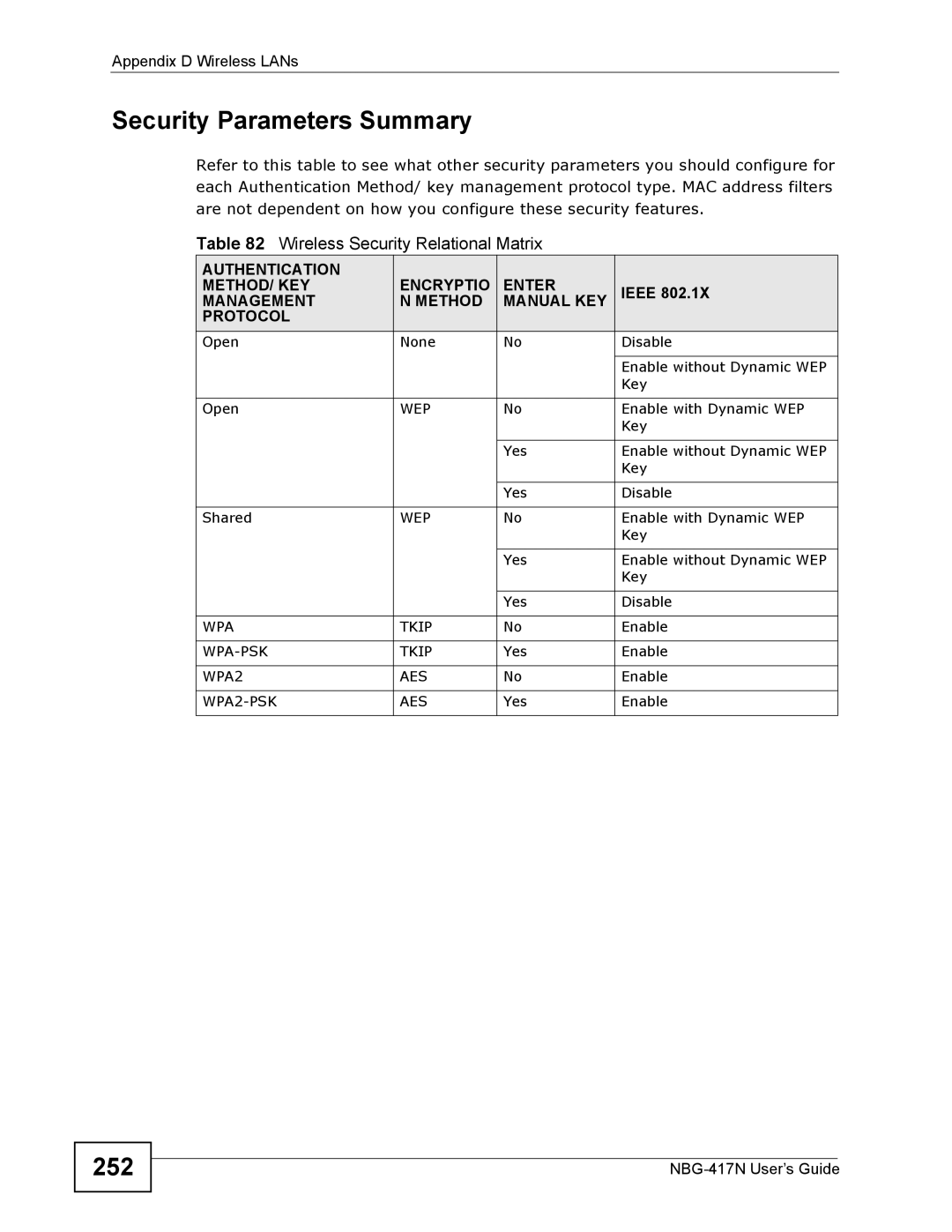
Refer to this table to see what other security parameters you should configure for each Authentication Method/ key management protocol type. MAC address filters are not dependent on how you configure these security features.
Table 82 Wireless Security Relational Matrix
AUTHENTICATION | ENCRYPTIO | ENTER |
|
METHOD/ KEY | IEEE 802.1X | ||
MANAGEMENT | N METHOD | MANUAL KEY | |
PROTOCOL |
|
|
|
Open | None | No | Disable |
|
|
|
|
|
|
| Enable without Dynamic WEP |
|
|
| Key |
|
|
|
|
Open | WEP | No | Enable with Dynamic WEP |
|
|
| Key |
|
|
|
|
|
| Yes | Enable without Dynamic WEP |
|
|
| Key |
|
|
|
|
|
| Yes | Disable |
|
|
|
|
Shared | WEP | No | Enable with Dynamic WEP |
|
|
| Key |
|
|
|
|
|
| Yes | Enable without Dynamic WEP |
|
|
| Key |
|
|
|
|
|
| Yes | Disable |
|
|
|
|
WPA | TKIP | No | Enable |
|
|
|
|
TKIP | Yes | Enable | |
|
|
|
|
WPA2 | AES | No | Enable |
|
|
|
|
AES | Yes | Enable | |
|
|
|
|