Chapter 7 - VPN Client Tunnels | 127 |
|
|
STEP/STAMP Encryption Secret
This is a shared alphanumeric long term secret between
The same secret must be entered into the VPN client in order for encryption and decryption to succeed.
IKE Policy
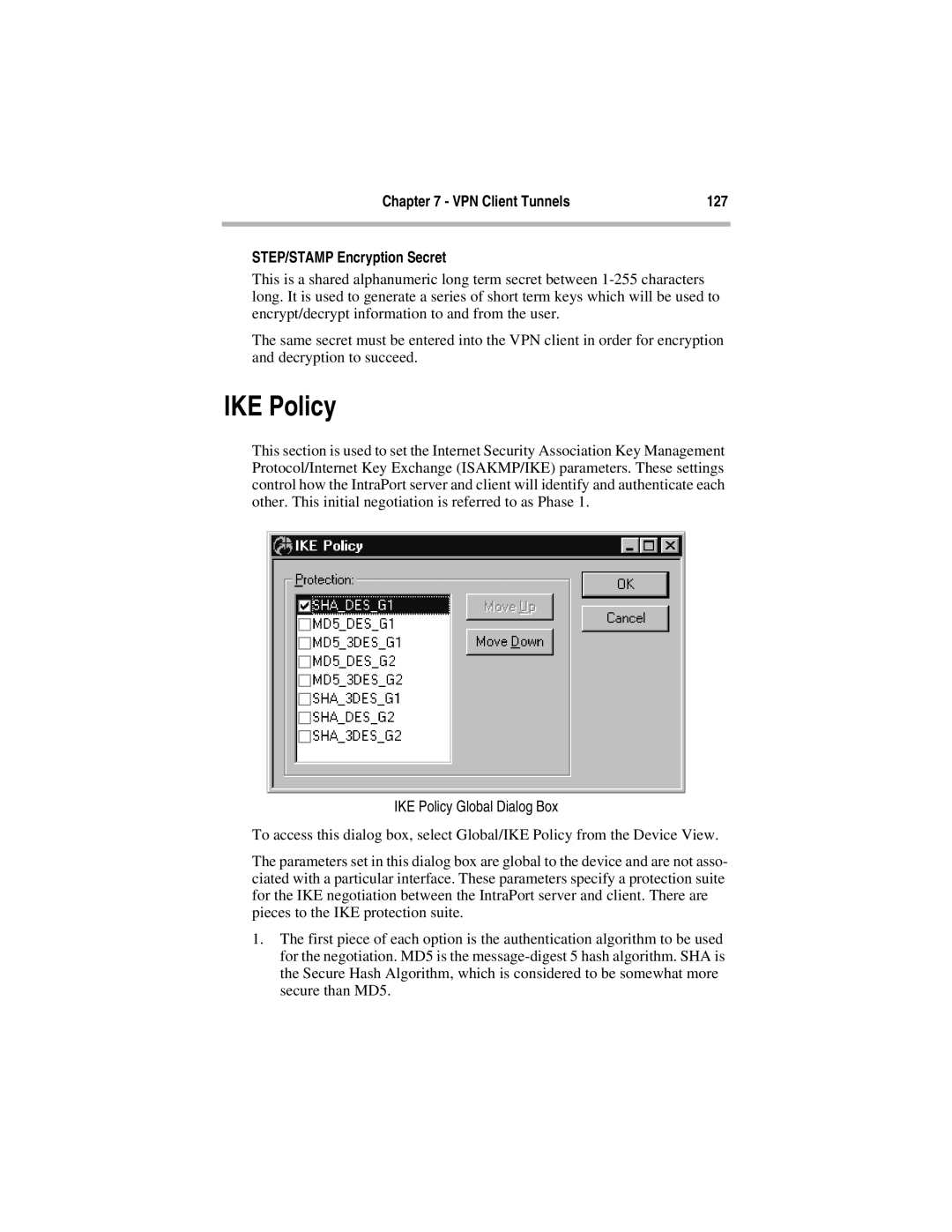
This section is used to set the Internet Security Association Key Management Protocol/Internet Key Exchange (ISAKMP/IKE) parameters. These settings control how the IntraPort server and client will identify and authenticate each other. This initial negotiation is referred to as Phase 1.
IKE Policy Global Dialog Box
To access this dialog box, select Global/IKE Policy from the Device View.
The parameters set in this dialog box are global to the device and are not asso- ciated with a particular interface. These parameters specify a protection suite for the IKE negotiation between the IntraPort server and client. There are pieces to the IKE protection suite.
1.The first piece of each option is the authentication algorithm to be used for the negotiation. MD5 is the