Chapter 6 - VPN Ports and | 101 |
|
|
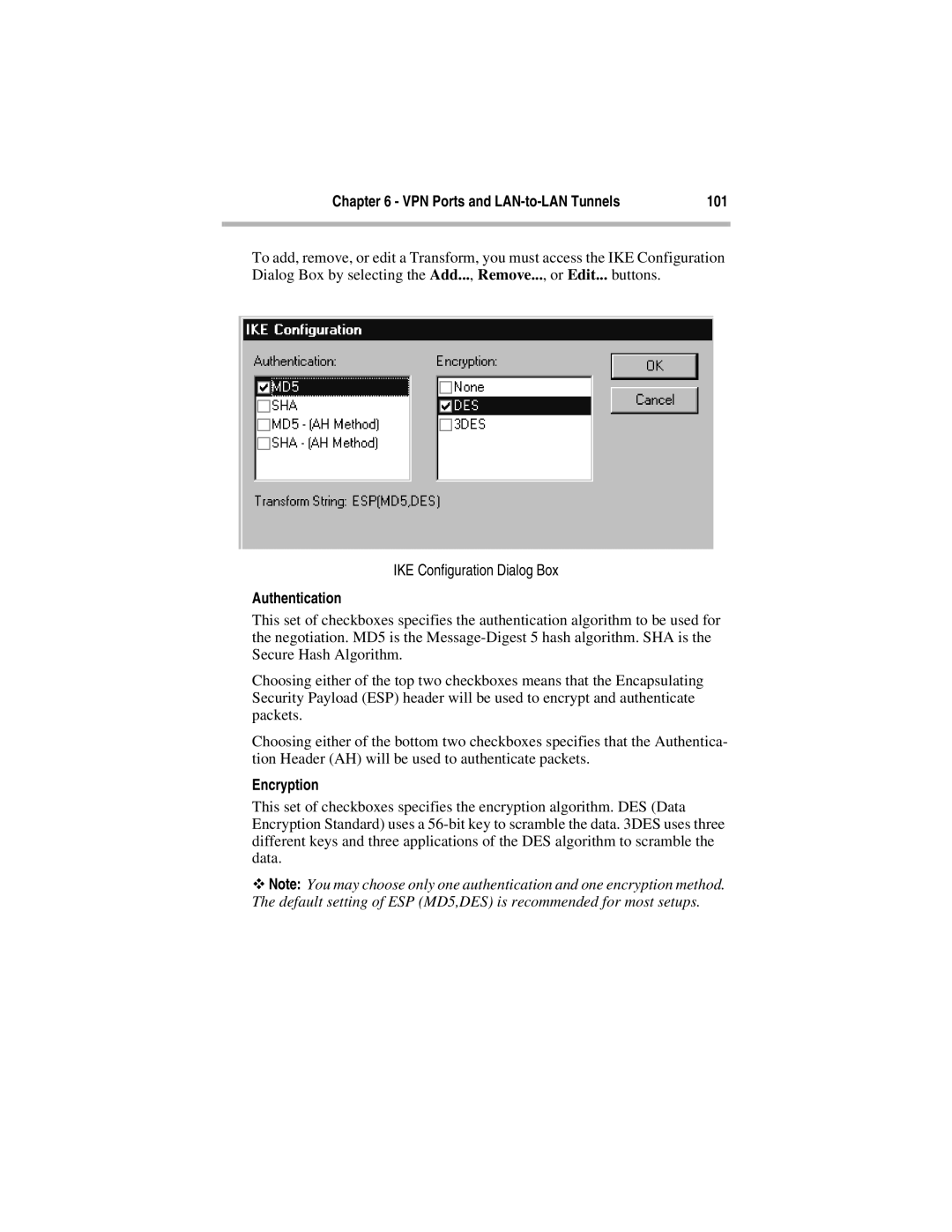
To add, remove, or edit a Transform, you must access the IKE Configuration Dialog Box by selecting the Add..., Remove..., or Edit... buttons.
IKE Configuration Dialog Box
Authentication
This set of checkboxes specifies the authentication algorithm to be used for the negotiation. MD5 is the
Choosing either of the top two checkboxes means that the Encapsulating Security Payload (ESP) header will be used to encrypt and authenticate packets.
Choosing either of the bottom two checkboxes specifies that the Authentica- tion Header (AH) will be used to authenticate packets.
Encryption
This set of checkboxes specifies the encryption algorithm. DES (Data Encryption Standard) uses a
ϖNote: You may choose only one authentication and one encryption method. The default setting of ESP (MD5,DES) is recommended for most setups.