Viewing vulnerabilities by detail in Enterprise Scanner
Use this view to examine event details that might be related to an attack or that you consider unusual.
Benefits
You analyze event data to evaluate the effectiveness of your system’s security and to investigate any suspicious activity. You can analyze event data in several ways:
vExamine events affecting specific agents, hosts, and groups.
vReview
Field descriptions
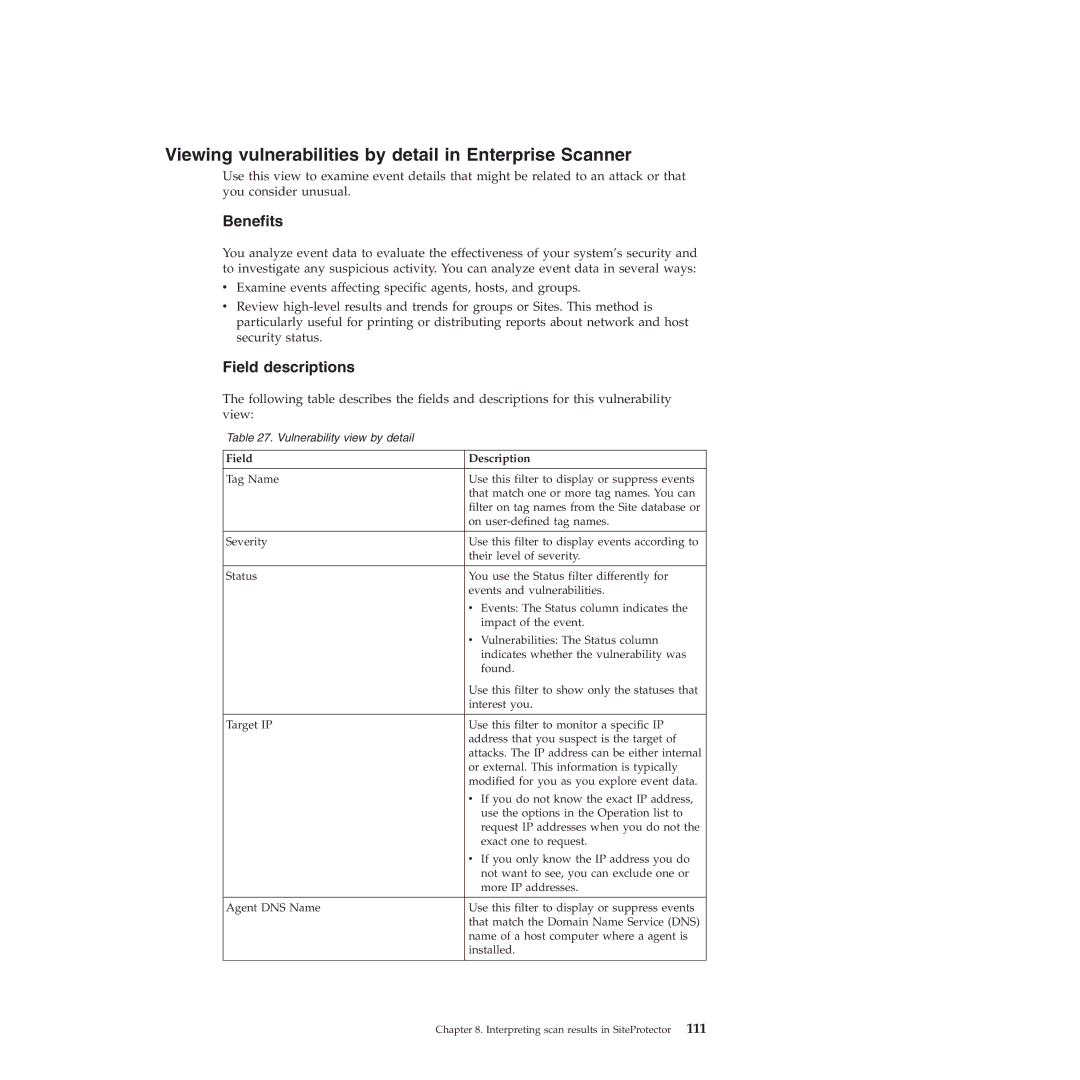
The following table describes the fields and descriptions for this vulnerability view:
Table 27. Vulnerability view by detail
Field | Description |
|
|
Tag Name | Use this filter to display or suppress events |
| that match one or more tag names. You can |
| filter on tag names from the Site database or |
| on |
|
|
Severity | Use this filter to display events according to |
| their level of severity. |
|
|
Status | You use the Status filter differently for |
| events and vulnerabilities. |
| v Events: The Status column indicates the |
| impact of the event. |
| v Vulnerabilities: The Status column |
| indicates whether the vulnerability was |
| found. |
| Use this filter to show only the statuses that |
| interest you. |
|
|
Target IP | Use this filter to monitor a specific IP |
| address that you suspect is the target of |
| attacks. The IP address can be either internal |
| or external. This information is typically |
| modified for you as you explore event data. |
| v If you do not know the exact IP address, |
| use the options in the Operation list to |
| request IP addresses when you do not the |
| exact one to request. |
| v If you only know the IP address you do |
| not want to see, you can exclude one or |
| more IP addresses. |
|
|
Agent DNS Name | Use this filter to display or suppress events |
| that match the Domain Name Service (DNS) |
| name of a host computer where a agent is |
| installed. |
|
|
Chapter 8. Interpreting scan results in SiteProtector 111