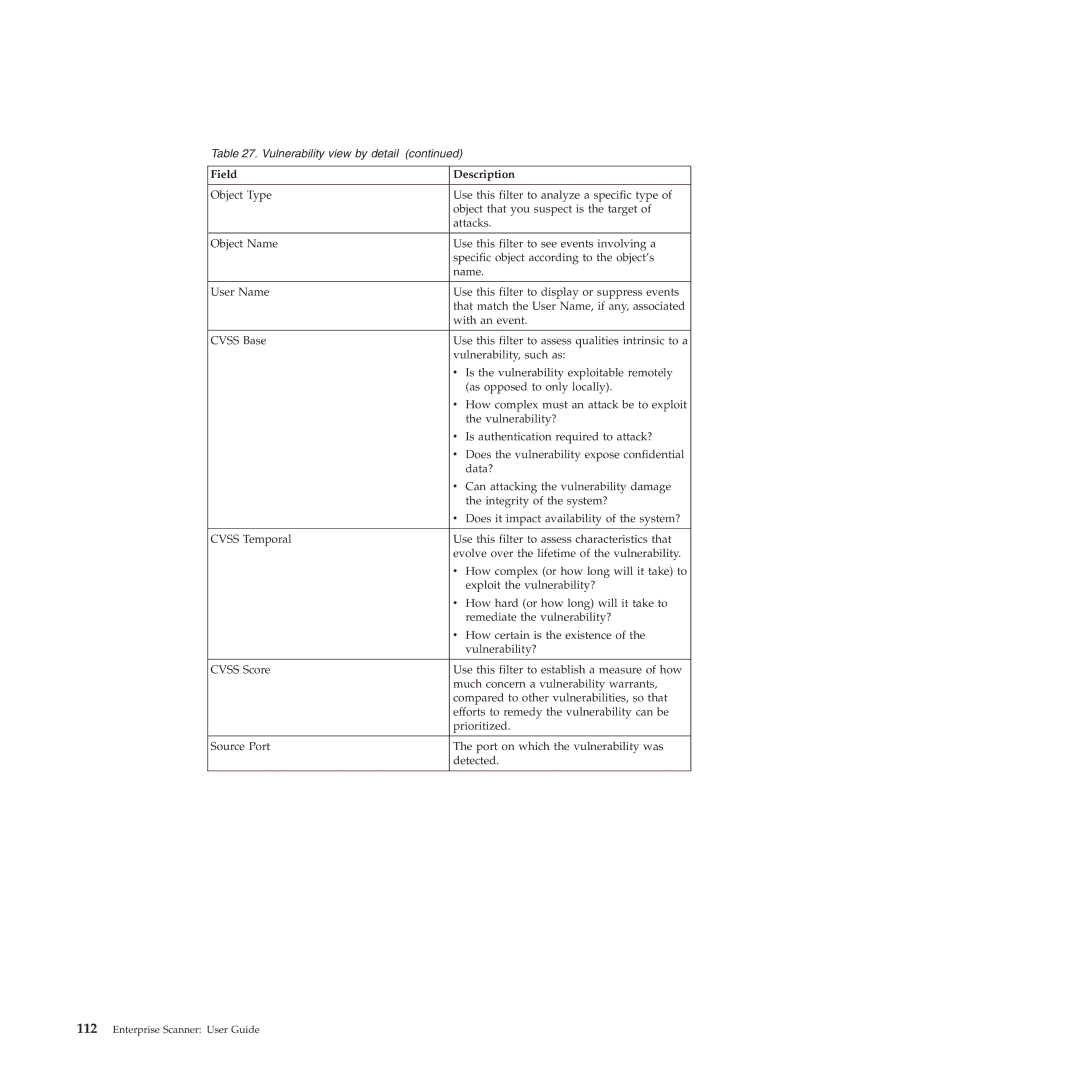
Table 27. Vulnerability view by detail (continued)
Field | Description |
|
|
Object Type | Use this filter to analyze a specific type of |
| object that you suspect is the target of |
| attacks. |
|
|
Object Name | Use this filter to see events involving a |
| specific object according to the object’s |
| name. |
|
|
User Name | Use this filter to display or suppress events |
| that match the User Name, if any, associated |
| with an event. |
|
|
CVSS Base | Use this filter to assess qualities intrinsic to a |
| vulnerability, such as: |
| v Is the vulnerability exploitable remotely |
| (as opposed to only locally). |
| v How complex must an attack be to exploit |
| the vulnerability? |
| v Is authentication required to attack? |
| v Does the vulnerability expose confidential |
| data? |
| v Can attacking the vulnerability damage |
| the integrity of the system? |
| v Does it impact availability of the system? |
CVSS Temporal | Use this filter to assess characteristics that |
| evolve over the lifetime of the vulnerability. |
| v How complex (or how long will it take) to |
| exploit the vulnerability? |
| v How hard (or how long) will it take to |
| remediate the vulnerability? |
| v How certain is the existence of the |
| vulnerability? |
|
|
CVSS Score | Use this filter to establish a measure of how |
| much concern a vulnerability warrants, |
| compared to other vulnerabilities, so that |
| efforts to remedy the vulnerability can be |
| prioritized. |
|
|
Source Port | The port on which the vulnerability was |
| detected. |
|
|