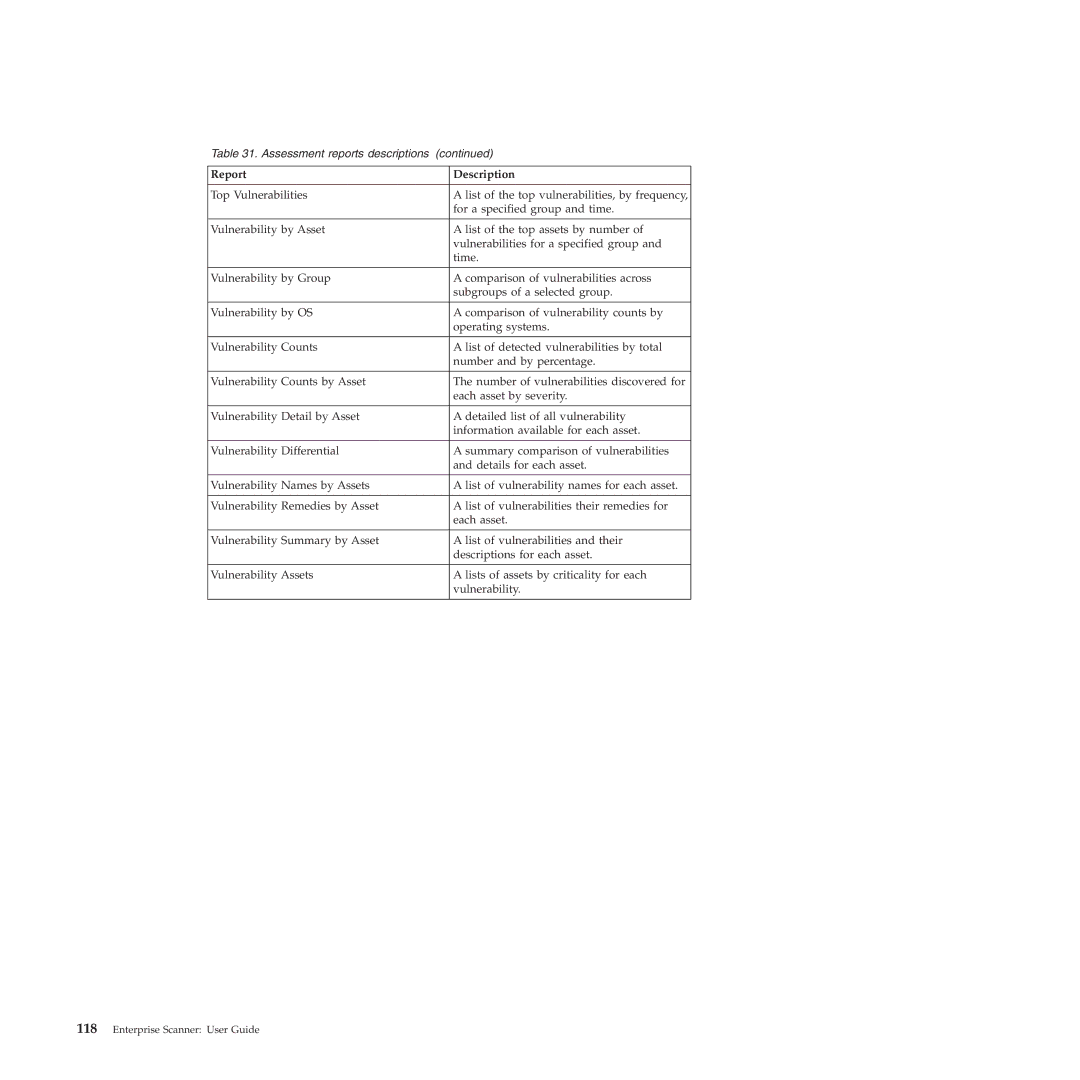
Table 31. Assessment reports descriptions (continued)
Report | Description |
|
|
Top Vulnerabilities | A list of the top vulnerabilities, by frequency, |
| for a specified group and time. |
|
|
Vulnerability by Asset | A list of the top assets by number of |
| vulnerabilities for a specified group and |
| time. |
|
|
Vulnerability by Group | A comparison of vulnerabilities across |
| subgroups of a selected group. |
|
|
Vulnerability by OS | A comparison of vulnerability counts by |
| operating systems. |
|
|
Vulnerability Counts | A list of detected vulnerabilities by total |
| number and by percentage. |
|
|
Vulnerability Counts by Asset | The number of vulnerabilities discovered for |
| each asset by severity. |
|
|
Vulnerability Detail by Asset | A detailed list of all vulnerability |
| information available for each asset. |
|
|
Vulnerability Differential | A summary comparison of vulnerabilities |
| and details for each asset. |
|
|
Vulnerability Names by Assets | A list of vulnerability names for each asset. |
|
|
Vulnerability Remedies by Asset | A list of vulnerabilities their remedies for |
| each asset. |
|
|
Vulnerability Summary by Asset | A list of vulnerabilities and their |
| descriptions for each asset. |
|
|
Vulnerability Assets | A lists of assets by criticality for each |
| vulnerability. |
|
|