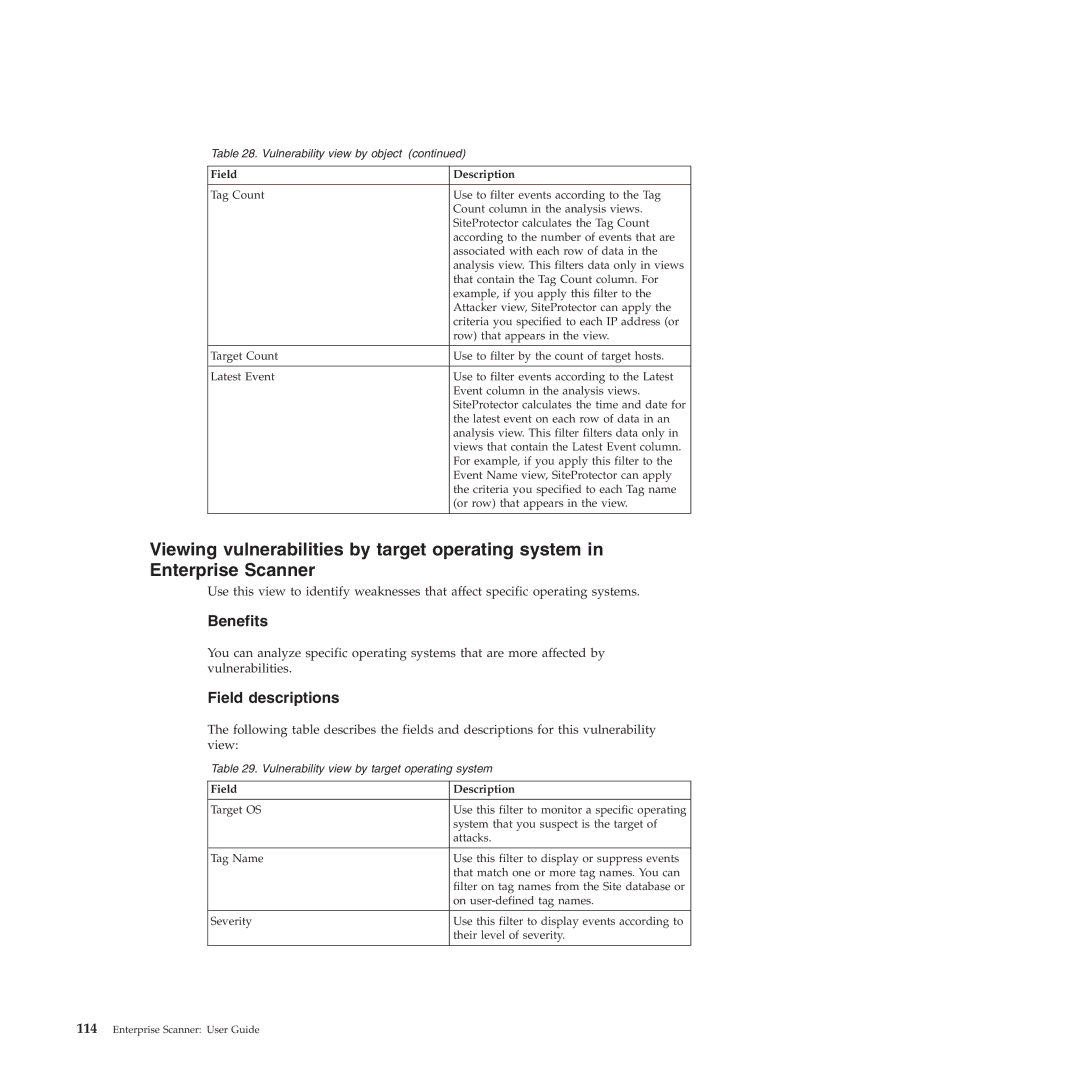
Table 28. Vulnerability view by object (continued)
Field | Description |
|
|
Tag Count | Use to filter events according to the Tag |
| Count column in the analysis views. |
| SiteProtector calculates the Tag Count |
| according to the number of events that are |
| associated with each row of data in the |
| analysis view. This filters data only in views |
| that contain the Tag Count column. For |
| example, if you apply this filter to the |
| Attacker view, SiteProtector can apply the |
| criteria you specified to each IP address (or |
| row) that appears in the view. |
|
|
Target Count | Use to filter by the count of target hosts. |
|
|
Latest Event | Use to filter events according to the Latest |
| Event column in the analysis views. |
| SiteProtector calculates the time and date for |
| the latest event on each row of data in an |
| analysis view. This filter filters data only in |
| views that contain the Latest Event column. |
| For example, if you apply this filter to the |
| Event Name view, SiteProtector can apply |
| the criteria you specified to each Tag name |
| (or row) that appears in the view. |
|
|
Viewing vulnerabilities by target operating system in Enterprise Scanner
Use this view to identify weaknesses that affect specific operating systems.
Benefits
You can analyze specific operating systems that are more affected by vulnerabilities.
Field descriptions
The following table describes the fields and descriptions for this vulnerability view:
Table 29. Vulnerability view by target operating system
Field
Target OS
Tag Name
Severity
Description
Use this filter to monitor a specific operating system that you suspect is the target of attacks.
Use this filter to display or suppress events that match one or more tag names. You can filter on tag names from the Site database or on
Use this filter to display events according to their level of severity.