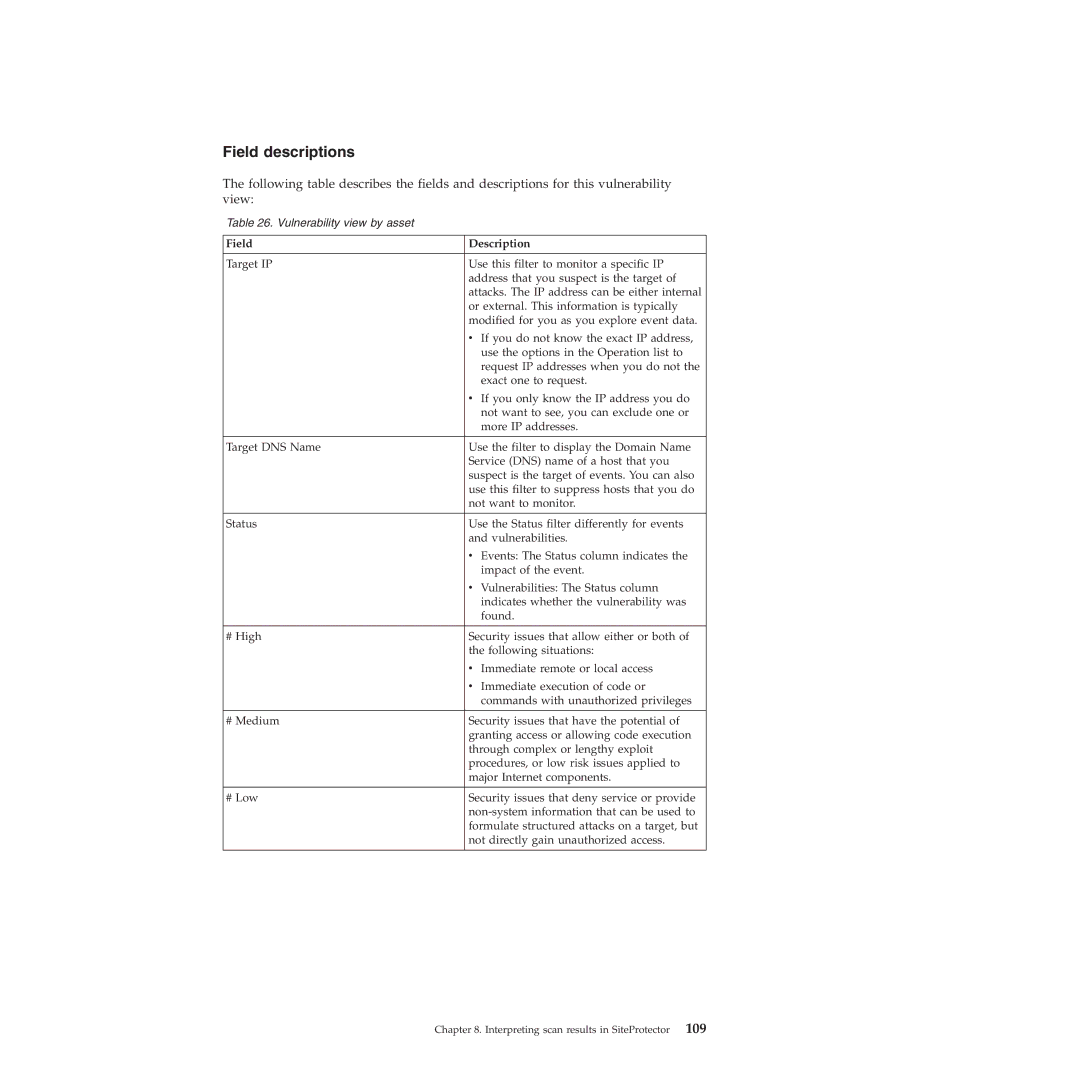
Field descriptions
The following table describes the fields and descriptions for this vulnerability view:
Table 26. Vulnerability view by asset
Field | Description |
|
|
Target IP | Use this filter to monitor a specific IP |
| address that you suspect is the target of |
| attacks. The IP address can be either internal |
| or external. This information is typically |
| modified for you as you explore event data. |
| v If you do not know the exact IP address, |
| use the options in the Operation list to |
| request IP addresses when you do not the |
| exact one to request. |
| v If you only know the IP address you do |
| not want to see, you can exclude one or |
| more IP addresses. |
|
|
Target DNS Name | Use the filter to display the Domain Name |
| Service (DNS) name of a host that you |
| suspect is the target of events. You can also |
| use this filter to suppress hosts that you do |
| not want to monitor. |
|
|
Status | Use the Status filter differently for events |
| and vulnerabilities. |
| v Events: The Status column indicates the |
| impact of the event. |
| v Vulnerabilities: The Status column |
| indicates whether the vulnerability was |
| found. |
|
|
# High | Security issues that allow either or both of |
| the following situations: |
| v Immediate remote or local access |
| v Immediate execution of code or |
| commands with unauthorized privileges |
|
|
# Medium | Security issues that have the potential of |
| granting access or allowing code execution |
| through complex or lengthy exploit |
| procedures, or low risk issues applied to |
| major Internet components. |
|
|
# Low | Security issues that deny service or provide |
| |
| formulate structured attacks on a target, but |
| not directly gain unauthorized access. |
|
|
Chapter 8. Interpreting scan results in SiteProtector 109