Appendix E: Understanding IP and IP addressing 159
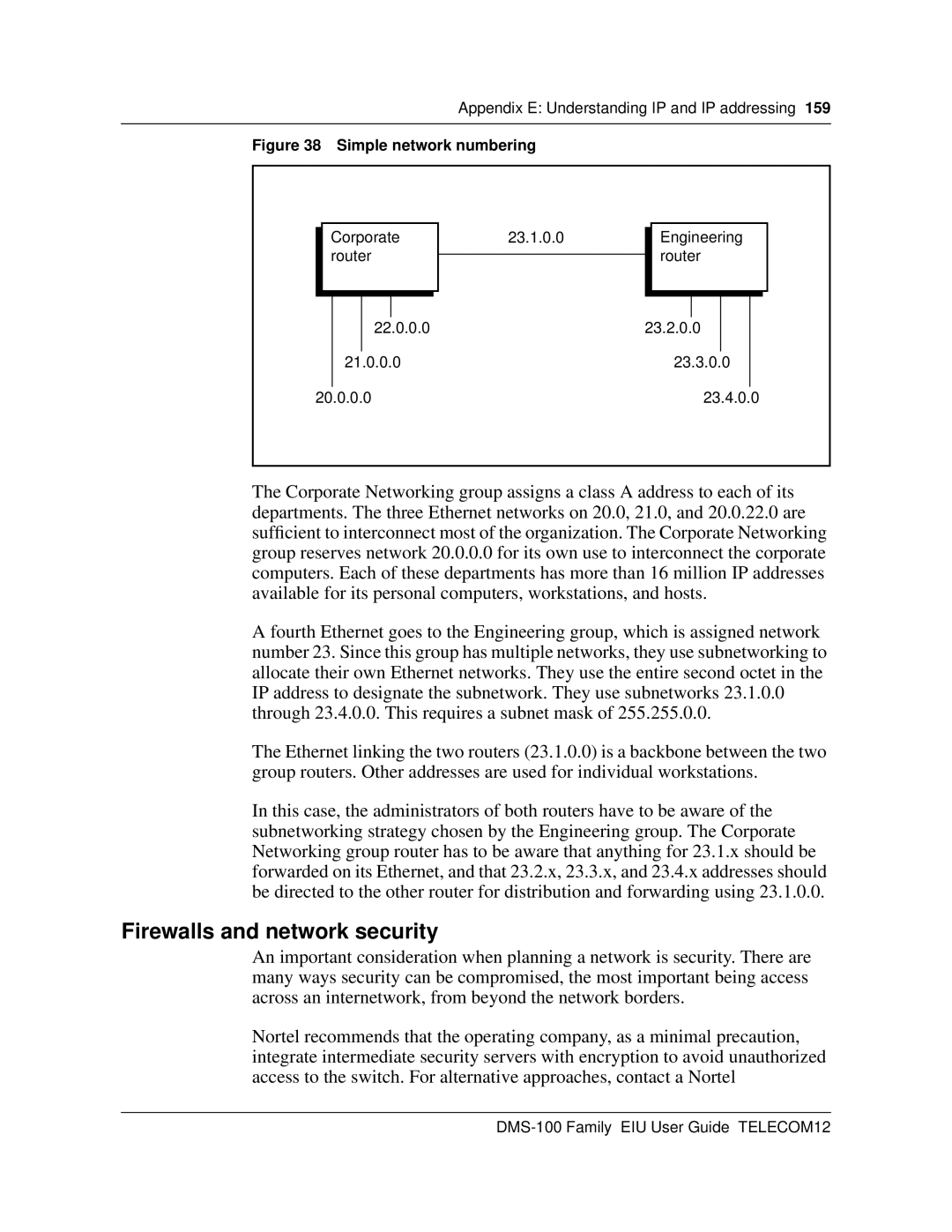
Figure 38 Simple network numbering
Corporate router
23.1.0.0
Engineering router
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| 22.0.0.0 |
|
| 23.2.0.0 |
|
|
|
| ||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| 21.0.0.0 |
| 23.3.0.0 |
|
| |||||||||
|
|
|
|
|
|
|
|
|
|
|
|
|
|
| |
20.0.0.0 |
|
|
| 23.4.0.0 |
| ||||||||||
The Corporate Networking group assigns a class A address to each of its departments. The three Ethernet networks on 20.0, 21.0, and 20.0.22.0 are sufficient to interconnect most of the organization. The Corporate Networking group reserves network 20.0.0.0 for its own use to interconnect the corporate computers. Each of these departments has more than 16 million IP addresses available for its personal computers, workstations, and hosts.
A fourth Ethernet goes to the Engineering group, which is assigned network number 23. Since this group has multiple networks, they use subnetworking to allocate their own Ethernet networks. They use the entire second octet in the IP address to designate the subnetwork. They use subnetworks 23.1.0.0 through 23.4.0.0. This requires a subnet mask of 255.255.0.0.
The Ethernet linking the two routers (23.1.0.0) is a backbone between the two group routers. Other addresses are used for individual workstations.
In this case, the administrators of both routers have to be aware of the subnetworking strategy chosen by the Engineering group. The Corporate Networking group router has to be aware that anything for 23.1.x should be forwarded on its Ethernet, and that 23.2.x, 23.3.x, and 23.4.x addresses should be directed to the other router for distribution and forwarding using 23.1.0.0.
Firewalls and network security
An important consideration when planning a network is security. There are many ways security can be compromised, the most important being access across an internetwork, from beyond the network borders.
Nortel recommends that the operating company, as a minimal precaution, integrate intermediate security servers with encryption to avoid unauthorized access to the switch. For alternative approaches, contact a Nortel