Chapter 1 | Authentication and Authorization |
| |
|
|
| |
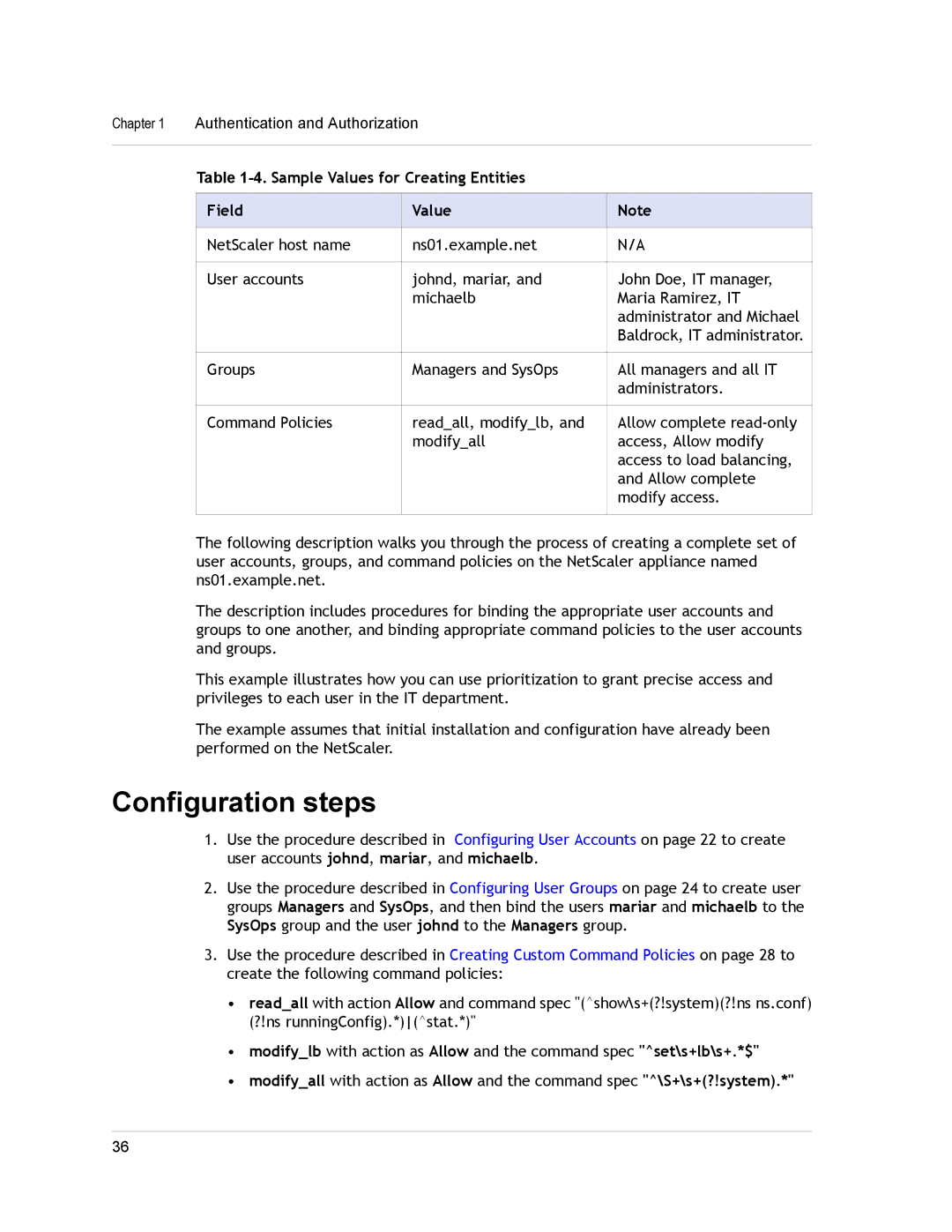
| Table |
| |
|
|
|
|
| Field | Value | Note |
|
|
|
|
| NetScaler host name | ns01.example.net | N/A |
|
|
|
|
| User accounts | johnd, mariar, and | John Doe, IT manager, |
|
| michaelb | Maria Ramirez, IT |
|
|
| administrator and Michael |
|
|
| Baldrock, IT administrator. |
|
|
|
|
| Groups | Managers and SysOps | All managers and all IT |
|
|
| administrators. |
|
|
|
|
| Command Policies | read_all, modify_lb, and | Allow complete |
|
| modify_all | access, Allow modify |
|
|
| access to load balancing, |
|
|
| and Allow complete |
|
|
| modify access. |
|
|
|
|
The following description walks you through the process of creating a complete set of user accounts, groups, and command policies on the NetScaler appliance named ns01.example.net.
The description includes procedures for binding the appropriate user accounts and groups to one another, and binding appropriate command policies to the user accounts and groups.
This example illustrates how you can use prioritization to grant precise access and privileges to each user in the IT department.
The example assumes that initial installation and configuration have already been performed on the NetScaler.
Configuration steps
1.Use the procedure described in Configuring User Accounts on page 22 to create user accounts johnd, mariar, and michaelb.
2.Use the procedure described in Configuring User Groups on page 24 to create user groups Managers and SysOps, and then bind the users mariar and michaelb to the SysOps group and the user johnd to the Managers group.
3.Use the procedure described in Creating Custom Command Policies on page 28 to create the following command policies:
•read_all with action Allow and command spec "(^show\s+(?!system)(?!ns ns.conf) (?!ns runningConfig).*)(^stat.*)"
•modify_lb with action as Allow and the command spec "^set\s+lb\s+.*$"
•modify_all with action as Allow and the command spec "^\S+\s+(?!system).*"
36