Chapter 1 | Authentication and Authorization |
|
|
|
|
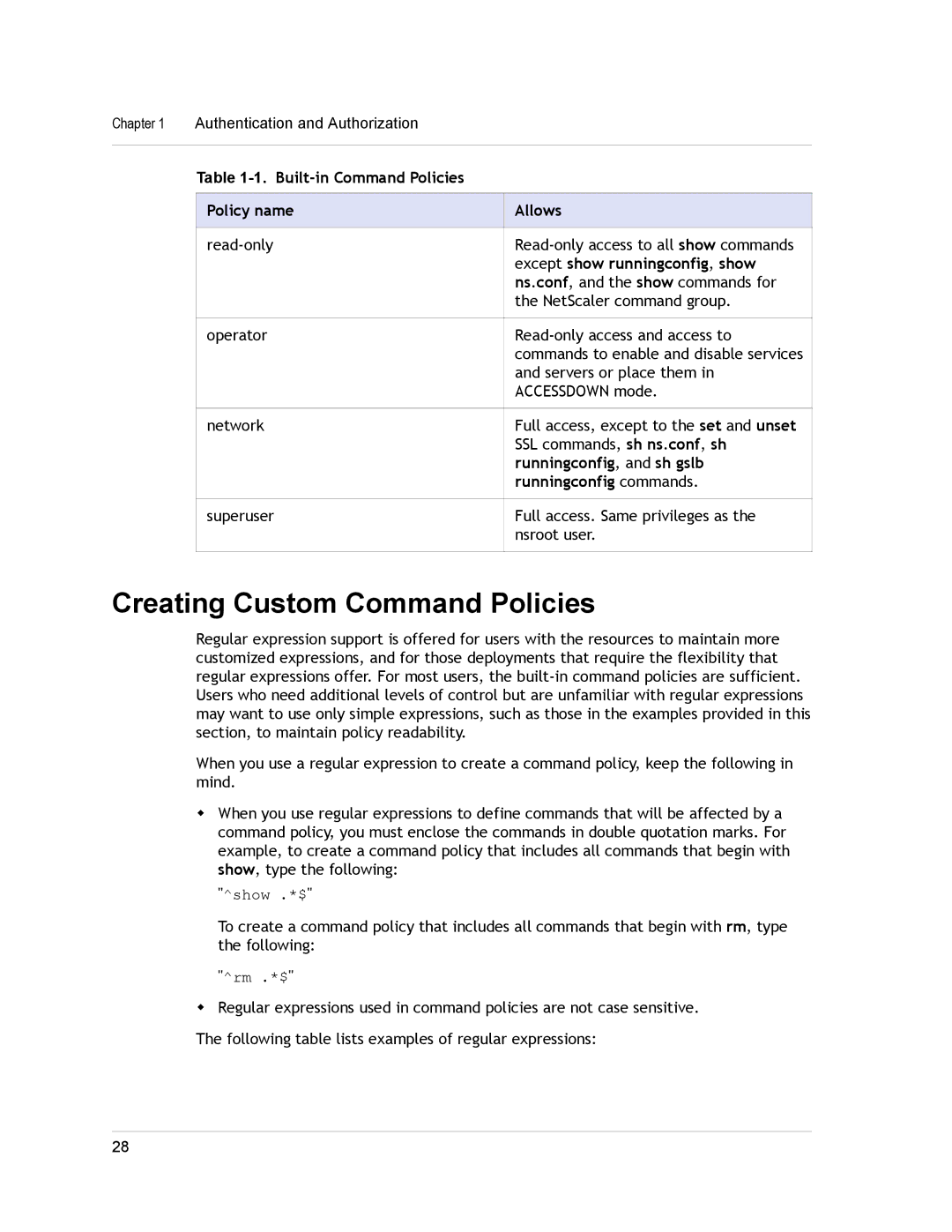
| Table |
|
|
|
|
| Policy name | Allows |
|
|
|
| ||
|
| except show runningconfig, show |
|
| ns.conf, and the show commands for |
|
| the NetScaler command group. |
|
|
|
| operator | |
|
| commands to enable and disable services |
|
| and servers or place them in |
|
| ACCESSDOWN mode. |
|
|
|
| network | Full access, except to the set and unset |
|
| SSL commands, sh ns.conf, sh |
|
| runningconfig, and sh gslb |
|
| runningconfig commands. |
|
|
|
| superuser | Full access. Same privileges as the |
|
| nsroot user. |
|
|
|
Creating Custom Command Policies
Regular expression support is offered for users with the resources to maintain more customized expressions, and for those deployments that require the flexibility that regular expressions offer. For most users, the
When you use a regular expression to create a command policy, keep the following in mind.
wWhen you use regular expressions to define commands that will be affected by a command policy, you must enclose the commands in double quotation marks. For example, to create a command policy that includes all commands that begin with show, type the following:
"^show .*$"
To create a command policy that includes all commands that begin with rm, type the following:
"^rm .*$"
wRegular expressions used in command policies are not case sensitive.
The following table lists examples of regular expressions:
28