Use the Firewall Log
The Firewall Log captures and stores network traffic information such as the type of data traffic, the time, the source and destination address / port, as well as the action taken by the firewall.
View Firewall Logs
(Available in Wireless Routing Client and Gateway modes)
Step 1:
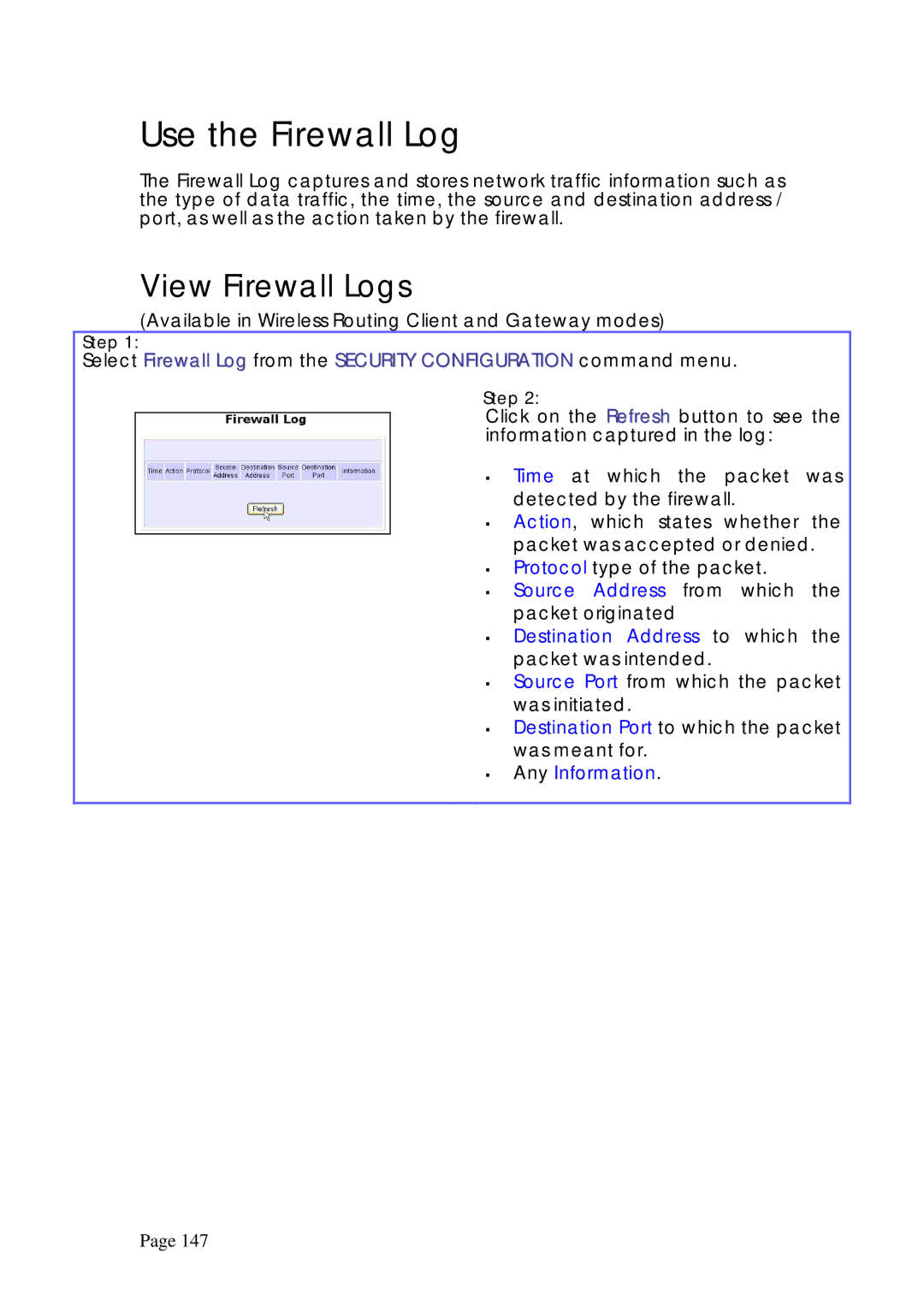
Select Firewall Log from the SECURITY CONFIGURATION command menu.
Step 2:
Click on the Refresh button to see the information captured in the log:
Time at which the packet was detected by the firewall.
Action, which states whether the
packet was accepted or denied. Protocol type of the packet.
Source Address from which the packet originated
Destination Address to which the packet was intended.
Source Port from which the packet was initiated.
Destination Port to which the packet was meant for.
Any Information.
Page 147