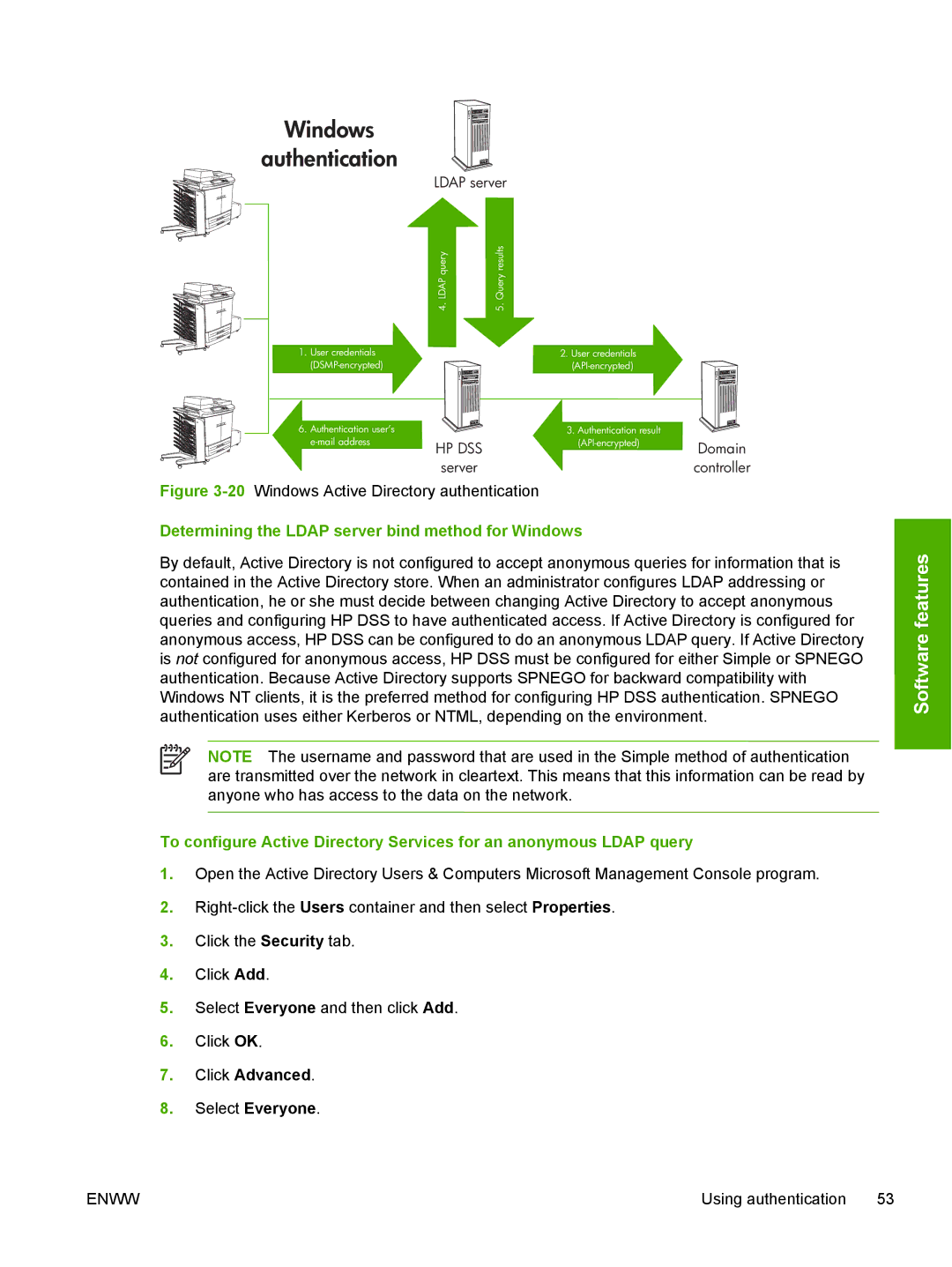
Windows |
|
|
|
authentication |
|
|
|
| LDAP server |
| |
| queryLDAP | resultsQuery |
|
| .4 | .5 |
|
1. User credentials |
| 2. User credentials |
|
|
| ||
6. Authentication user’s |
| 3. Authentication result |
|
HP DSS | Domain | ||
|
| ||
| server |
| controller |
Figure |
| ||
Determining the LDAP server bind method for Windows |
| ||
By default, Active Directory is not configured to accept anonymous queries for information that is | |||
contained in the Active Directory store. When an administrator configures LDAP addressing or | |||
authentication, he or she must decide between changing Active Directory to accept anonymous | |||
queries and configuring HP DSS to have authenticated access. If Active Directory is configured for | |||
anonymous access, HP DSS can be configured to do an anonymous LDAP query. If Active Directory | |||
is not configured for anonymous access, HP DSS must be configured for either Simple or SPNEGO | |||
authentication. Because Active Directory supports SPNEGO for backward compatibility with | |||
Windows NT clients, it is the preferred method for configuring HP DSS authentication. SPNEGO | |||
authentication uses either Kerberos or NTML, depending on the environment. | |||
NOTE The username and password that are used in the Simple method of authentication | |||
are transmitted over the network in cleartext. This means that this information can be read by | |||
anyone who has access to the data on the network. |
| ||
To configure Active Directory Services for an anonymous LDAP query |
| ||
1.Open the Active Directory Users & Computers Microsoft Management Console program.
2.
3.Click the Security tab.
4.Click Add.
5.Select Everyone and then click Add.
6.Click OK.
7.Click Advanced.
8.Select Everyone.
ENWW | Using authentication | 53 |