User’s Manual of
packet of destination unreachable to the spoofed source address. Eventually leading it to be unreachable by other clients and the system will go down.
•ICMP DoS - Ping of A malicious attacker sending a malformed ICMP request packet larger than the
Death | 65,536 bytes to the target system. Some target systems cannot handle the |
| packet larger than the maximum IP packet size, which often causes target |
| system froze, crashed or rebooted. |
|
|
• ICMP DoS - Smurf | A malicious attacker sending a malformed ICMP request packet with broadcast |
| destination addresses to the target system. After receiving the packet, all |
| reachable hosts send an ICMP echo reply packet back to the spoofed source |
| address. Thus, the target host will suffer from a larger amount of traffic |
| generated. |
|
|
|
|
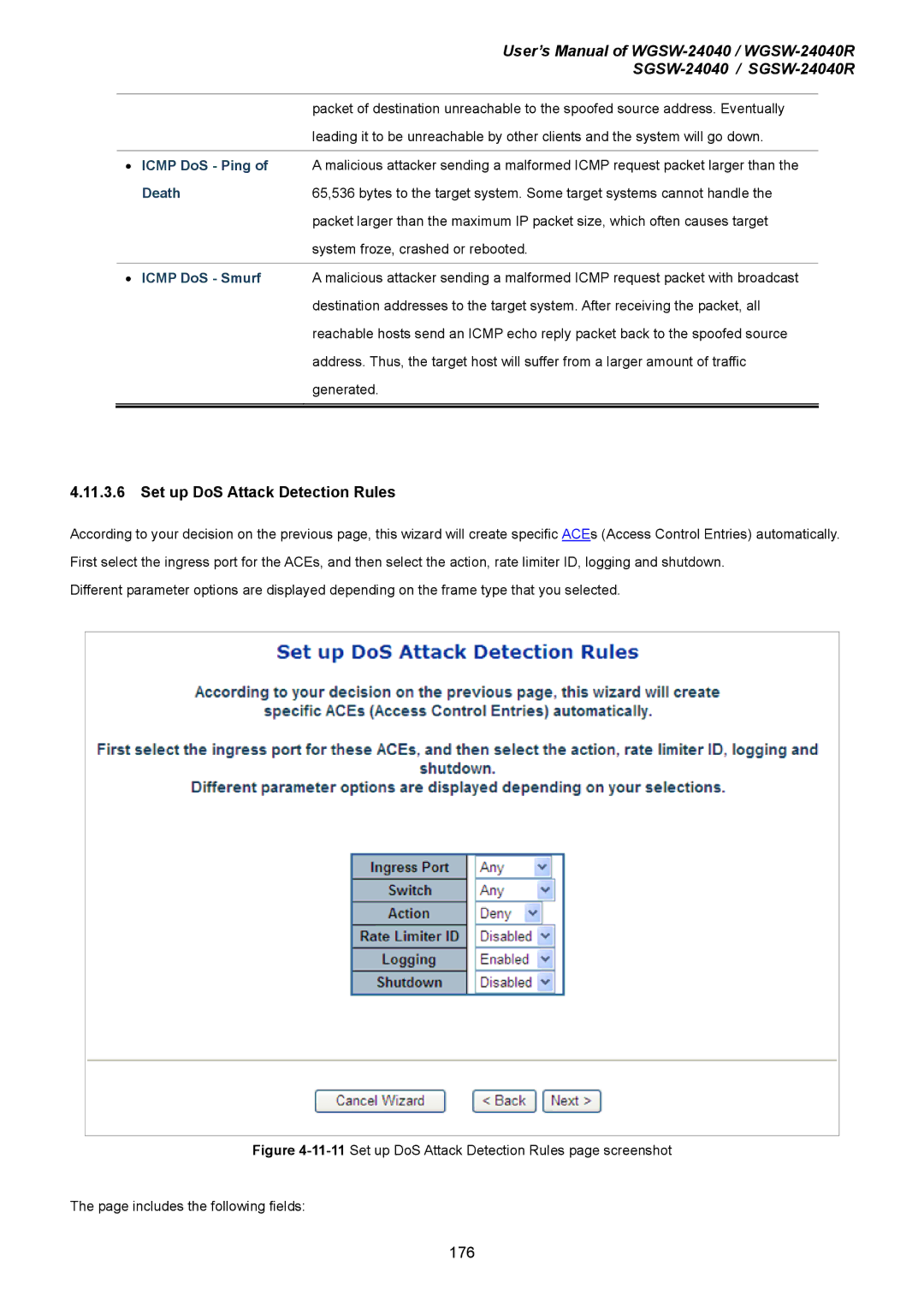
4.11.3.6 Set up DoS Attack Detection Rules
According to your decision on the previous page, this wizard will create specific ACEs (Access Control Entries) automatically. First select the ingress port for the ACEs, and then select the action, rate limiter ID, logging and shutdown.
Different parameter options are displayed depending on the frame type that you selected.
Figure 4-11-11 Set up DoS Attack Detection Rules page screenshot
The page includes the following fields:
176