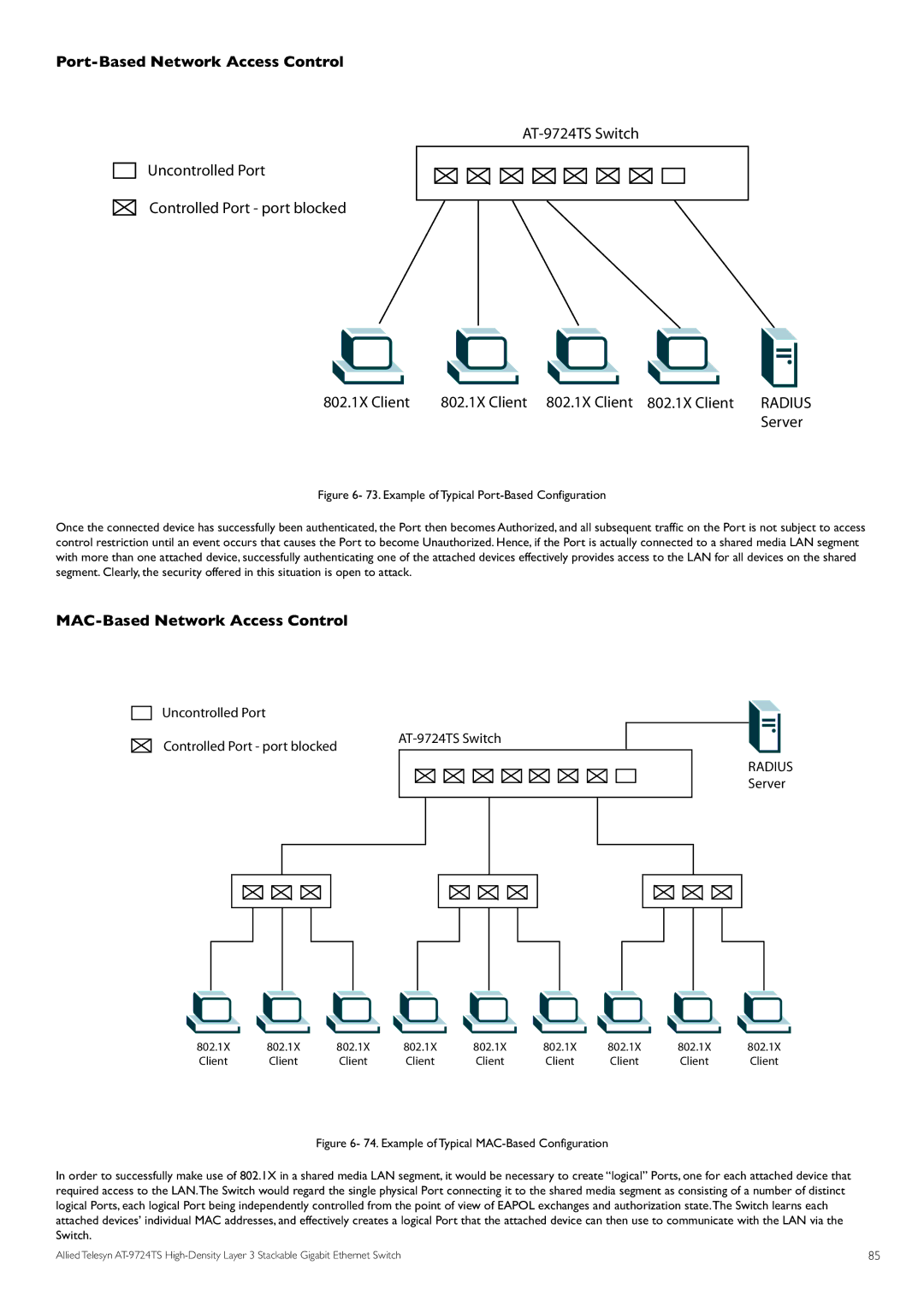
Port-Based Network Access Control
Uncontrolled Port
Controlled Port - port blocked
802.1X Client | 802.1X Client 802.1X Client 802.1X Client | RADIUS |
|
| Server |
Figure 6- 73. Example of Typical Port-Based Configuration
Once the connected device has successfully been authenticated, the Port then becomes Authorized, and all subsequent traffic on the Port is not subject to access control restriction until an event occurs that causes the Port to become Unauthorized. Hence, if the Port is actually connected to a shared media LAN segment with more than one attached device, successfully authenticating one of the attached devices effectively provides access to the LAN for all devices on the shared segment. Clearly, the security offered in this situation is open to attack.
MAC-Based Network Access Control
Uncontrolled Port
Controlled Port - port blocked
RADIUS
Server
802.1X | 802.1X | 802.1X | 802.1X | 802.1X | 802.1X | 802.1X | 802.1X | 802.1X |
Client | Client | Client | Client | Client | Client | Client | Client | Client |
Figure 6- 74. Example of Typical MAC-Based Configuration
In order to successfully make use of 802.1X in a shared media LAN segment, it would be necessary to create “logical” Ports, one for each attached device that |
|
required access to the LAN.The Switch would regard the single physical Port connecting it to the shared media segment as consisting of a number of distinct |
|
logical Ports, each logical Port being independently controlled from the point of view of EAPOL exchanges and authorization state.The Switch learns each |
|
attached devices’ individual MAC addresses, and effectively creates a logical Port that the attached device can then use to communicate with the LAN via the |
|
Switch. | 85 |
Allied Telesyn |