SLC Advanced Console Manager User Guide
Contacts
Warranty
Copyright & Trademark
Open Source Software
Revision History
Disclaimer & Revisions
Table of Contents
Web and Command Line Interfaces
Quick Setup
Basic Parameters
Services
Device Ports 100
Connections 166
USB/SD Card Port 157
Maintenance 227
User Authentication 174
Application Examples 255
Command Reference 260
Appendix a Security Considerations 328
Appendix B Safety Information 329
SLC 8000 Advanced Console Manager User Guide
List of Tables
SLC 8048 Unit Front Side Part Number SLC 804812N-01-S
List of Figures
13 SSL Certificate97
13User Authentication Custom Menus
Purpose and Audience
About this Guide
Summary of Chapters
About this Guide
Additional Documentation
Console Management
Features
Power
Introduction
Models
System Features
Protocols Supported
Access Control
Configuration Options
Hardware Features
Device Port Buffer
Device Ports Back Side
Serial Port Interfaces
Network Connection
Network Connections
Memory Card Port
USB Interface
Internal Modem Location
Internal Modem
Product Information Label
Installation
Power Cords
Whats in the Box
Technical Specifications
To connect to a device port
Physical Installation
Connecting to a Device Port
To install the SLC 8000 advanced console manager in a rack
Console Port and Device Port DTE Reverse Pinout Disabled
Connecting Terminals
Connecting to Network Ports
Modular Expansion for I/O Module
To connect a terminal
AC Input
Modem Servicing Instructions
Modem Installation
Installation
Battery Part Numbers
Battery Replacement
Battery Replacement Instructions
Disposal of Used Batteries from battery data sheet
Short the Battery and Damage the Battery Housing
Installation
Recommendations
Quick Setup
IP Address
Before you begin, ensure that you have
Method #1 Using the Front Panel Display
Front Panel LCD Display and Keypads
Navigating
Up and down arrows
Right arrow
Left arrow
Enter center button
Entering the Settings
To complete the Quick Setup
Method #2 Quick Setup on the Web
Restoring Factory Defaults
To use the LCD display to restore factory default settings
Quick Setup
Date & Time Settings
Network Settings
Administrator Settings
Method #3 Quick Setup on the Command Line Interface
To complete the command line interface Quick Setup script
IP Address if
Config Eth1
Specifying
Password
Sysadmin
Date/Time
Next Step
Web Manager
Web and Command Line Interfaces
Port Number Bar
To log in to the SLC web manager
Logging
Logging Out
Command Line Interface
Web Page Help
To log in any other user
Command Syntax
Command Line Help
Tips
To show current CLI settings
General CLI Commands
To configure the current command line session
To set the number of lines displayed by a command
To clear the command history
To view the last 100 commands entered in the session
To view the rights of the currently logged-in user
Requirements
Basic Parameters
Network Network Settings
To enter settings for one or both network ports
12340BCD1D67000000008375BADD0057 may be shortened to
Ethernet Interfaces Eth1 and Eth2
1234BCD1D678375BADD57
Hostname & Name Servers
Gateway
TCP Keepalive Parameters
Network Commands
DNS Servers
DHCP-Acquired DNS Servers
To view DNS settings
To set the default and alternate network gateways
To view all network settings
To view Ethernet port settings and counters
To view a list of IP filters
IP Filter
Viewing IP Filters
Mapping Rulesets
To delete a mapping
Configuring IP Filters
To enable IP filters
Enabling IP Filters
Protocol
Rule Parameters
Ruleset Name
IP Addresses
Generate rule to
Allow service
Port Range
Action
Updating an IP Filter
IP Filter Commands
Deleting an IP Filter
Replace Rule Number delete Rule Number
To configure routing settings
Routing
Dynamic Routing
Static Routing
Equivalent Routing Commands
To configure static or dynamic routing
Show routing resolveip enabledisable email Email Address
Ethernet Port
Enable VPN Tunnel
To complete the VPN
Name
Remote Hop/Router
Authentication IKE
Authentication ESP
Remote Id
Configuring an IPsec VPN Tunnel through the CLI
Security
To disable Fips
To enable Fips
System Logging and Other Services
Services
System Logging
SSH/Telnet/Logging
Audit Log
Telnet
Web SSH/Web Telnet Settings
Phone Home
Top Level MIB
Enable Agent
Version
Communities
V3 Read-Write User
SNMP, SSH, Telnet, and Logging Commands
Set services one or more services parameters
V3 Read-Only User
To configure NFS and SMB/CIFS
Set services v3passwordv3phrasev3rwpasswordv3rwphrase
To view current services
Show services
Nfsserverhostname or ipaddr/exported/path
SMB/CIFS Share
To unmount a remote NFS share
NFS and SMB/CIFS Commands
To view NFS share settings
To mount a remote NFS share
Secure Lantronix Network
To view SMB/CIFS settings
Show cifs
Services Secure Lantronix Network
IP Address Login
To directly access the CLI interface for a device
SSH or Telnet CLI Session
To directly access a specific port on a particular device
Secure Lantronix
Secure Lantronix Network Commands
Set s one or more parameters
Add IP Address delete IP Address
To set the local date, time, and time zone
Date and Time
Search localsubnetipaddrlistboth
Show slcnetwork ipaddrlist allAddress Mask
Enable NTP
10 Services Date & Time
To view the local date, time, and time zone
Date and Time Commands
Show ntp
To view NTP settings
To configure the Web Server
Web Server
Admin web protocol sslv2nosslv2
Admin Web Commands
To configure the timeout for web sessions
Admin web timeout disable5-120 minutes
Services Web Sessions
To view, reset, import, or change an SSL Certificate
Services SSL Certificate
Import SSL Certificate
Reset to Default
Login
Certificate
IGoogle Gadgets
Web Server Commands
To set up an SLC iGoogle gadget
Password / Retype Password
14 iGoogle Gadget Example
Connection Methods
Device Ports
Permissions
Device Ports
Modules
Devices Device Status
Device Status
Devices Device Ports
Device Ports
Telnet/SSH/TCP in Port Numbers
Global Commands
Sshport TCP Port tcpport TCP Port telnetport TCP Port
Device Ports Settings
To view global settings for device ports
To open the Device Ports Settings
SLC 8000 Advanced Console Manager User Guide 106
IP Settings
Device Port Settings
Data Settings
Modem Settings Device Ports
Hardware Signal Triggers
Modem Settings PPP Mode
Modem Settings Text Mode
AT S7=45 SO=0 L1 V1 X4 &D2 &c1 E1 Q0
Remote/Dial-out Login
Same authentication for
DOD Authentication
Enable NAT
Device Ports SLP / ServerTech CDU Device
Port Status and Counters
To open the Device Ports SLP
Outlets
To enter SLP commands
Number of Outlets
Number of Expansion
Devices Device Ports Sensorsoft
Device Port Sensorsoft Device
Device Port Commands
To view the settings for one or more device ports
To set the dialout password
Show deviceport port Device Port List or Name
To zero the port counters for one or more device ports
Device Commands
To view a list of all device port names
To view the modes and states of one or more device ports
To connect to a device port to monitor it
Interacting with a Device Port
Connect direct endpoint
Device Ports Logging
Local Logging
NFS File Logging
Device Port NumberDevice Port NameFile number.log
USB and SD Card Logging
Email/SNMP Notification
Sylog Logging
Local Logging
Email/Traps
Email/Traps
Byte Threshold
Email Delay
Send
Trigger on
USB / SD Card Logging
Log Viewing Attributes
Syslog Logging
To clear the local log for a device port
Logging Commands
To configure logging settings for one or more device ports
Show locallog Device Port # or Name bytes Bytes To Display
To set console port parameters
Console Port
To view console port settings
Internal Modem Settings
Console Port Commands
To configure console port settings
Setting Up Internal Modem Storage
SLC 8000 Advanced Console Manager User Guide 128
AT S7=45 SO=0 L1 V1 X4 &D2 &c1 E1 Q0
Chap Handshake
Password/ Retype
Host Lists
To add a host list
Host Parameters
To retry connecting to the host list
Escape Sequence
Retry connecting to the host list
To view or update a host list
To delete a host list
Host List Commands
To add a new host entry to a list or edit an existing entry
To add a script
Scripts
To move a host entry to a new position in the host list
To display the members of a host list
SLC 8000 Advanced Console Manager User Guide 136
Script Name
Scripts
Type
Group
To view or update a script
SD Card Right to view and enter settings for SD card
User Rights
To change the permissions for a script
Batch Script Syntax
To rename a script
To delete a script
Interface Script Syntax
Senduser Password
Set myvar expr 1 +
Primary Commands
Secondary Commands
Determine if two strings are equal
String compare str 1 str
Compare two strings
String match str 1 str
19 Control Flow Commands
Control Flow Commands
Interface Script-Monitor Port
Sample Scripts
SLC 8000 Advanced Console Manager User Guide 146
Batch Script-SLC CLI
SLC 8000 Advanced Console Manager User Guide 148
Site Name
Sites
To add a site
Site Id
Chap Secret
Login/CHAP Host
Dial-out Login
Dial-out Password
Set site addedit Site Name parameters
To view or update a site
To delete a site
To create or edit a site
Dial
Modem Dialing States
Set site delete Site Name show site allnamesSite Name
Dial-on-demand
Dial-back
Dial-back & Dial-on-demand
Dial-in & Dial-on-demand
Cbcp Server
SLC 8000 Advanced Console Manager User Guide 156
USB/SD Card Port
Set Up of USB/SD Card Storage
Click Configure
Filesystem Check
Unmount
Format
Filesystem
Devices USB Modem
To configure the USB Modem port, from the USB Ports table
Modem Settings
Text Mode
Remote/Dial-out Pwd
PPP Mode
Manage Files
SD Card Commands
USB Commands
Connections
Typical Setup Scenarios for the SLC Unit
Terminal Server
Reverse Terminal Server
Remote Access Server
Console Server
Multiport Device Server
Connection
Connection Configuration
To create a connection
Outgoing
Trigger
To view, update, or disconnect a current connection
SSH Out
Options
To configure initial timeout for outgoing connections
Connection Commands
To monitor a device port
To view connections and their IDs
To terminate a bidirectional or unidirectional connection
To display details for a single connection
Connect global show
To display global connections
Ldap
User Authentication
Kerberos
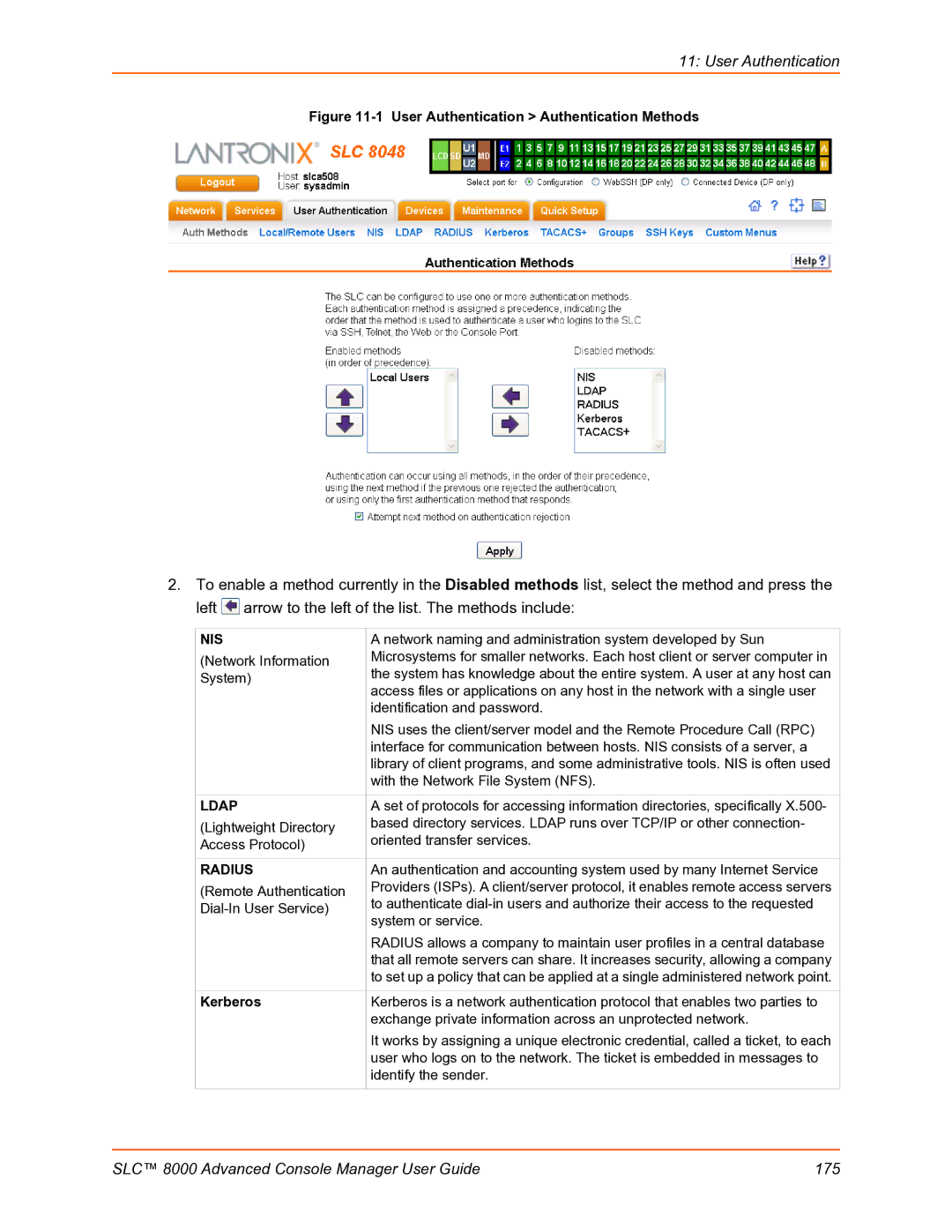
User Authentication Authentication Methods
Show auth
Authentication Commands
To set ordering of authentication methods
Set auth one or more parameters
User Types and Rights
User Rights
To enable local and/or remote users
Local and Remote User Settings
To add a user
Adding, Editing or Deleting a User
Data Ports
Listen Ports
Clear Port Buffers
Allow Password Change
Enable for Dial-back
Display Menu at Login
Password Expires
Select or clear the checkboxes for the following rights
SD Card Right to enter settings for SD card
Shortcut
Local Users Commands
Local User Rights Commands
To view settings for all remote users
Remote User Commands
User Authentication NIS
To configure the SLC unit to use NIS to authenticate users
NIS Master Server
Enable NIS
NIS Domain
Broadcast for NIS
SLC 8000 Advanced Console Manager User Guide 188
To view NIS settings
NIS Commands
To set group and permissions for NIS users
Ldap
To configure the SLC unit to use Ldap to authenticate users
Enable Ldap
User Authentication Ldap
Uid=roberts,ou=People,dc=lantronix,dc=com and the password
Uid=$login,ou=People,dc=lantronix,dc=com, and user roberts
Key File is in PEM format, eg
Certificate in base64 encoding
Private key in base64 encoding
Set ldap one or more parameters
Ldap Commands
Adsupport enabledisable
Right to enter modem settings for USB
To import or delete a certificate
To set the Ldap bind password
To view Ldap settings
To set user group and permissions for Ldap users
Radius
Tcp, or udp
Listen Port
To set user group and permissions for Radius users
Radius Commands
Show radius
To view Radius settings
END-VENDOR Lantronix
Kerberos
Realm
Enable Kerberos
KDC IP Address
KDC Port
Full Administrative
Use Ldap
To set user group and permissions for Kerberos users
Kerberos Commands
Set kerberos group defaultpoweradmin
Set kerberos one or more parameters
Show kerberos
To view Kerberos settings
Set kerberos permissions Permission List
Set kerberos custommenu Menu Name
TACACS+ Servers
Enable TACACS+
Secret
SLC 8000 Advanced Console Manager User Guide 207
To set user group and permissions for TACACS+ users
TACACS+ Commands
Set tacacs+ group defaultpoweradmin
Set tacacs+ one or more parameters
Set tacacs+ custommenu Menu Name
To view TACACS+ settings
To configure Groups in the SLC unit
Groups
Group Name
10 User Authentication Groups
Deviceport, tcp, or udp
Enable for
Dial-back
Imported Keys
SSH Keys
Exported Keys
SLC 8000 Advanced Console Manager User Guide 214
Host & User Associated with Key
Host & Login for Import
Imported Keys SSH
Exported Keys SSH Out
Key Name
Host and Login for Export
To view, reset, or import SSH RSA1, RSA, And DSA host keys
To view or delete a key
Key
Reset to Default Host
Import Host Key
To export a key
SSH Commands
To import an SSH key
Set sshkey import ftpscpcopypaste one or more parameters
To display SSH keys that have been exported
To reset defaults for all or selected host keys
To delete a key
To display SSH keys that have been imported
To add a custom menu
Custom Menus
SLC 8000 Advanced Console Manager User Guide 221
Redisplay Menu
Menu Name
Title
Nicknames
To create a new custom menu from an existing custom menu
Custom User Menu Commands
To view or update a custom menu
To delete a custom menu
To set the optional title for a menu
SLC 8000 Advanced Console Manager User Guide 225
SLC 8000 Advanced Console Manager User Guide 226
Firmware & Configurations
Maintenance
Maintenance Firmware & Configurations
To configure settings
Site Information
Internal Temperature
SLC Firmware
Load Firmware Via Options
Boot Banks
Configuration Management
Manage Files
Administrative Commands
To reboot the SLC 8000 advanced console manager
Admin shutdown
To list current hardware and firmware information
To update SLC firmware to a new revision
To view FTP settings
To restore the SLC unit to factory default settings
Set temperature one or more parameters
To rename a saved configuration
To delete a saved configuration
To list the configurations saved to a location
Starting at
System Logs
To view system logs
Level
To clear system logs
System Log Command
Ending at
To clear one or all of the system logs
Audit Log
SLC 8000 Advanced Console Manager User Guide 238
Email Log
Maintenance Email Log
Host Lookup
Diagnostics
ARP Table
Netstat
Diag arp email Email Address
Diagnostic Commands
To generate and send Ethernet packets
To display a report of network connections
To resolve a host name into an IP address
To verify that the host is up and running
Parameters ethport
Default is
To display all network traffic, applying optional filters
Diag nettrace one or more parameters
Status/Reports
Maintenance Status/Reports
Devices Host Lists
Serial port settings
View Report
All Displays all reports Port Status
To display the overall status of all SLC units
Status Commands
To display a snapshot of configurable parameters
Emailing Logs and Reports
11 Emailed Log or Report
To email a log to an individual
SLC 8000 Advanced Console Manager User Guide 248
Event Trigger
Events
Ethernet
Events Commands
To delete an event
To update event definitions
To configure the LCD and Keypad
LCD/Keypad
To configure the Keypad
To configure the LCD
Keypad Locked
Banners
LCD/Keypad Commands
To configure banner settings
Restore Factory Defaults Password / Retype Password
Logout Banner
Banner Commands
Login Banner
Welcome Banner
Telnet/SSH to a Remote Device
Application Examples
SLC show deviceport port
SLC connect direct deviceport
Reboot Shutdown messages from SUN
Dial-in Text Mode to a Remote Device
Dial-in Text Mode to a Remote Device
Local Serial Connection to Network Device via Telnet
Local Serial Connection to Network Device via Telnet
Trying Connected to Escape character is Sun OS 8.0 login
Introduction to Commands
Command Reference
For general command line Help, type
Admin banner show
Administrative Commands
Admin banner login
Admin banner logout
Admin config factorydefaults
Admin banner ssh
Admin banner welcome
Admin config delete
Admin config save
Admin config restore
Admin firmware update
Admin config show
Admin firmware bootbank
Admin firmware show
Admin keypad
Admin ftp password
Admin ftp server
Admin ftp show
Admin memory swap add Size of Swap in MB usbport U1U1
Admin keypad show
Admin lcd reset
Admin memory show
Admin site
Admin quicksetup
Admin reboot
Admin shutdown
Admin web certificate show
Admin version
Admin web certificate
Admin web certificate reset
Admin web show
Admin web group
Admin web timeout
Admin web terminate
Audit Log Commands
Show user
Authentication Commands
Set auth
Show auth
Show kerberos
Kerberos Commands
Displays Kerberos settings
Set kerberos
Set ldap bindpassword
Ldap Commands
Set ldap
Show ldap
Local Users Commands
Set localusers addedit User Login one or more parameters
Set ldap certificate importdelete
Set localusers delete
Set local users complexpasswords
Set localusers allowreuse
Set localusers state
Set localusers periodwarning
Set localusers maxloginattempts
Set localusers password
Set localusers periodlockout
Show localusers
NIS Commands
Set nis
Set radius
Radius Commands
Displays NIS settings
Show nis
Show radius
TACACS+ Commands
Displays Radius settings
Set radius server
Set localusers lock
User Permissions Commands
Show tacacs+
Set localusers group
Set remoteusers addedit
Set localusers permissions
Set remoteusers listonlyauth
Set nisldapradiuskerberostacacs+ permissions
Set remoteusers delete
Show remoteusers
Set nisldapradiuskerberostacacs+ group
Set cli
CLI Commands
Set cli terminallines
Show history
Connection Commands
Show cli
Set history
Connect direct
Connect global outgoingtimeout
Connect terminate
Connect listen deviceport
Connect unidirection
Show connections connid
Show connections
Set consoleport
Set menu add
Custom User Menu Commands
Show consoleport
Set localusers
Set nisldapradiuskerberostacacs custommenu Menu Name
Set menu delete
Set nisldapradiuskerberostacacs+ custommenu
Show menu
Set ntp
Date and Time Commands
Set datetime
Show datetime
Set command
Device Commands
Show ntp
Set deviceport port
Device Port Commands
SLC 8000 Advanced Console Manager User Guide 294
Sshport TCP Port telnetport TCP Port tcpport TCP Port
Set deviceport global
Show deviceport global
Show deviceport names
Show portstatus
Show deviceport port
Show portcounters
Show portcounters zerocounters
Diag netstat
Diagnostic Commands
Diag arp
Diag internals
Diag pingping6
Diag lookup
Diag loopback
Diag perfstat
Diag traceroute
Count=1, delay = 5 seconds
Diag sendpacket host
Diag top
Slp outletcontrol state
End Device Commands
Slp auth login
Slp envmon
Slp system
Events Commands
Admin events add
Slp restart
Admin events show
Group Commands
Admin events delete
Admin events edit
Set groups rename Group Name newname New Group Name
Host List Commands
Set hostlist addedit Host List Name
Set hostlist addedit Host List Name entry
Set hostlist delete
Set hostlist edit Host List Name move
Show hostlist
Set ipfilter state
Internal Modem Commands
Set ipfilter mapping
Set ip filter rules
Logging Commands
Set locallog clear
Show locallog
Example
Set log modem pppdebug enabledisable
Set log modem ppplog enabledisable
Set log clear modem
Set network dns
Network Commands
Show log local
Set network
Set network port
Configures up to three DNS servers
Set network gateway
Set network host
Show network port
Displays all network settings
Show network gateway
Show network host
Set cifs
NFS and SMB/CIFS Commands
Set nfs mount
Set nfs unmount
Show nfs
Routing Commands
Set cifs password
Show cifs
Show routing
Services Commands
Security Commands
Show services
Show slcnetwork
SLC Network Commands
SSH Key Commands
Set slcnetwork
Set sshkey import
Set sshkey delete
Set sshkey export
Set sshkey import
Show sshkey import
Set sshkey server reset
Set sshkey server import type
Show sshkey export
Show sshkey server
Status Commands
Show syslog
System Log Commands
Show sysconfig
Show sysstatus
Show syslog clear
USB Access Commands
USB Storage Commands
Set usb access
Set usb storage unmount
Set usb storage fsck
Set usb storage format
Set usb storage mount
Show usb storage
USB Modem Commands
Set usb storage copy
Set usb storage delete
Show usb modem
VPN Commands
Set usb modem U1U2 dialoutpassword
Set vpn
Show vpn
Show vpn rsakey
Set temperature
Show temperature
Set temperature
Security Practice
Appendix a Security Considerations
Factors Affecting Security
Safety Precautions
Appendix B Safety Information
Port Connections
Rack
Appendix C Adapters and Pinouts
Appendix C Adapters and Pinouts
SLC 8000 Advanced Console Manager User Guide 333
Appendix D Protocol Glossary
NTP Network Time Protocol
PAP Password Authentication Protocol
Radius Remote Authentication Dial-In User Service
TACACS+ Terminal Access Controller Access Control System
Manufacturer’s Name & Address
Appendix E Compliance Information
RoHS Notice
Appendix E Compliance Information

![]() arrow to the left of the list. The methods include:
arrow to the left of the list. The methods include: