Firewall > Access Rules
5If you want to define the source IP addresses that are affected by the rule, such as restricting certain users from accessing the Internet, enter the starting IP addresses of the address range in the Address Range Begin field and the ending IP address in the Address Range End field. To include all IP addresses, enter * in the Address Range Begin field.
6Select the destination of the traffic affected by the rule, LAN, WAN, or *, from the Destination menu.
7If you want to define the destination IP addresses that are affected by the rule, for example, to allow inbound Web access to several Web servers on your LAN, enter the starting IP addresses of the address range in the Address Range Begin field and the ending IP address in the Address Range End field. To include all IP addresses, enter * in the Address Range Begin field.
8Enter any comments to help identify the rule in the Comments field.
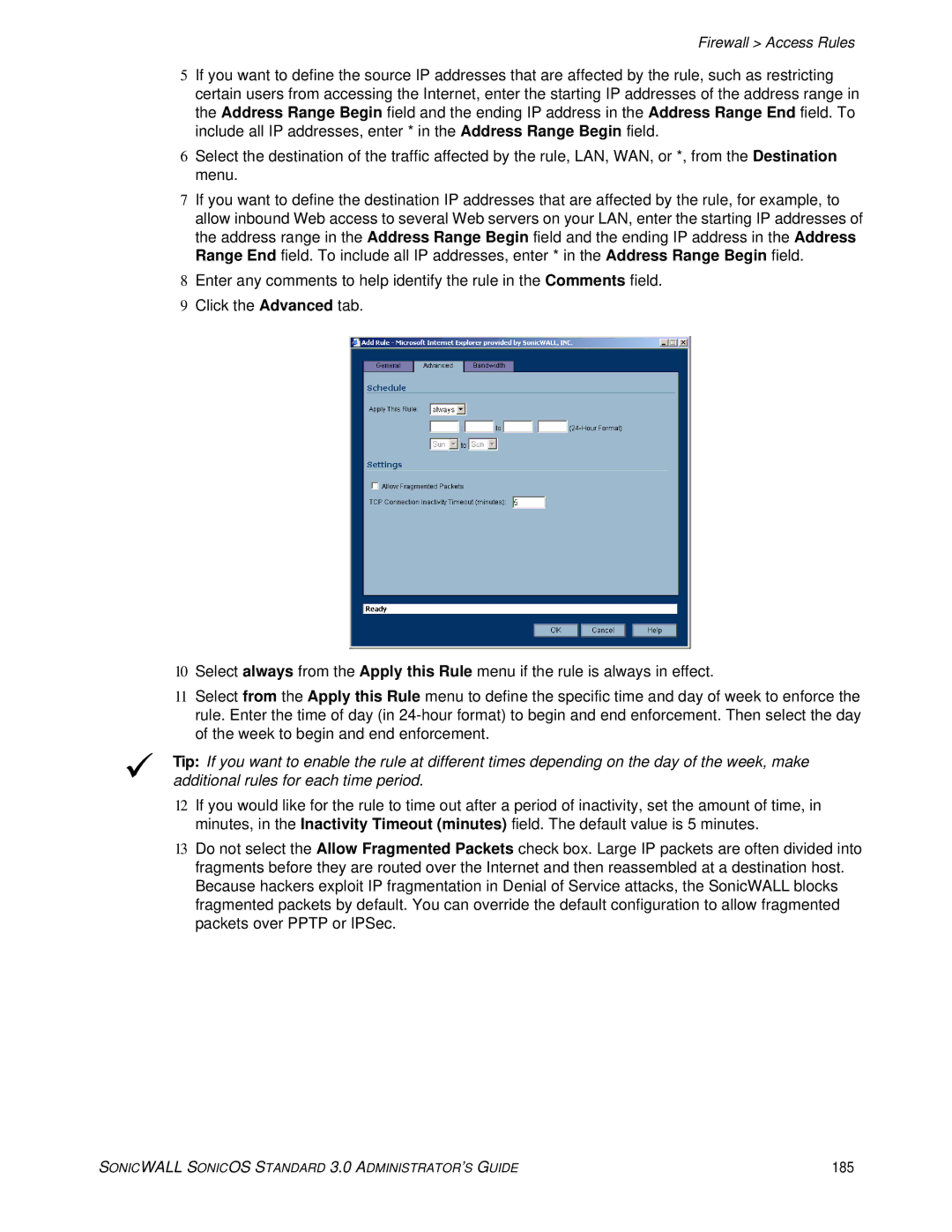
9Click the Advanced tab.
10Select always from the Apply this Rule menu if the rule is always in effect.
11Select from the Apply this Rule menu to define the specific time and day of week to enforce the rule. Enter the time of day (in
9Tip: If you want to enable the rule at different times depending on the day of the week, make additional rules for each time period.
12If you would like for the rule to time out after a period of inactivity, set the amount of time, in minutes, in the Inactivity Timeout (minutes) field. The default value is 5 minutes.
13Do not select the Allow Fragmented Packets check box. Large IP packets are often divided into fragments before they are routed over the Internet and then reassembled at a destination host. Because hackers exploit IP fragmentation in Denial of Service attacks, the SonicWALL blocks fragmented packets by default. You can override the default configuration to allow fragmented packets over PPTP or IPSec.
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE | 185 |