Configuring GroupVPN Policy on the SonicWALL
In the IKE (Phase 1) Proposal section, select the following settings:
Group 2 from the DH Group menu. 3DES from the Encryption menu SHA1 from the Authentication menu
Leave the default setting, 28800, in the Life Time (secs) field. This setting forces the tunnel to renegotiate and exchange keys every 8 hours.
In the IPSec (Phase 2) Proposal section, select the following settings:
ESP from the Protocol menu 3DES from the Encryption menu MD5 from the Authentication menu
Select Enable Perfect Forward Secrecy if you want an additional
Leave the default setting, 28800, in the Life Time (secs) field. This setting forces the tunnel to renegotiate and exchange keys every 8 hours.
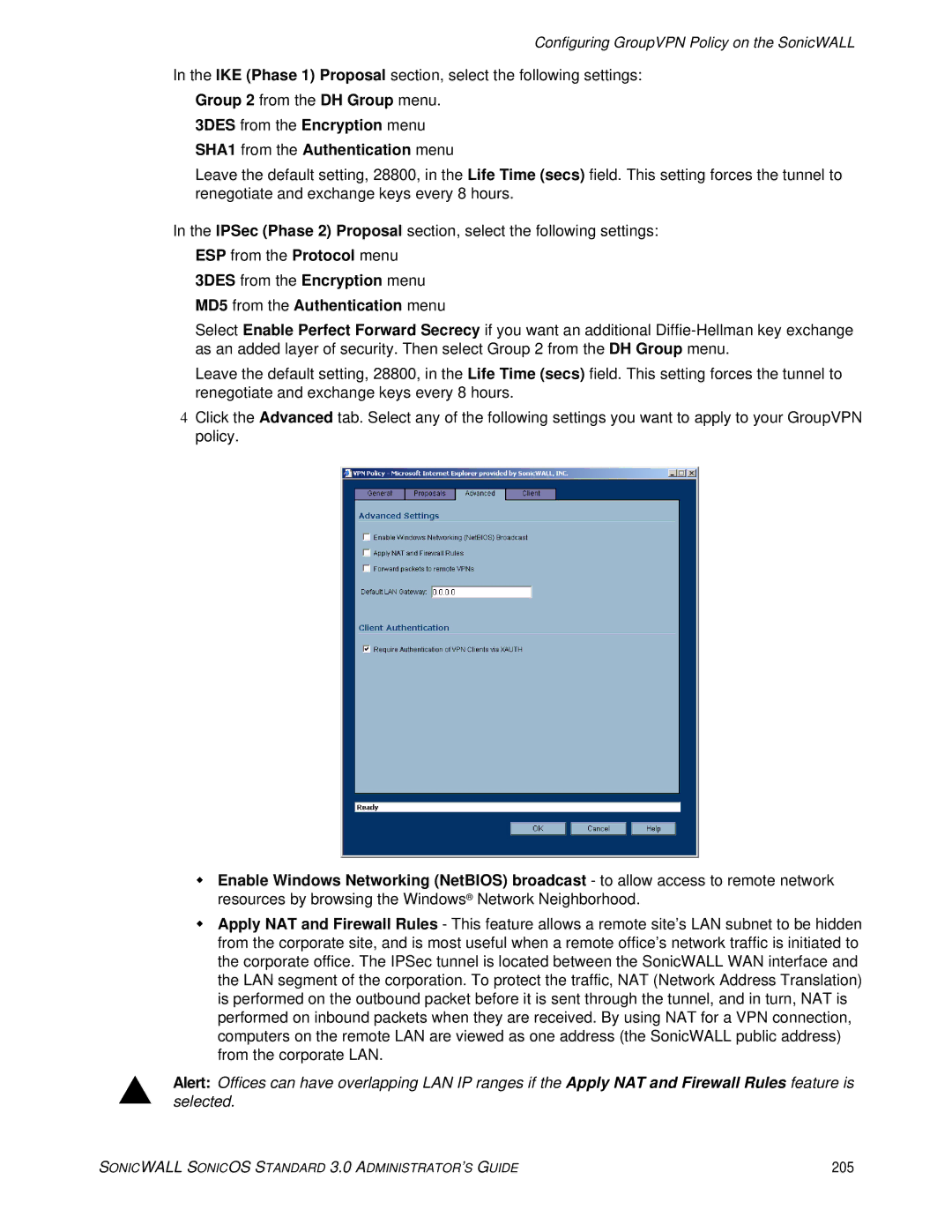
4Click the Advanced tab. Select any of the following settings you want to apply to your GroupVPN policy.
Enable Windows Networking (NetBIOS) broadcast - to allow access to remote network resources by browsing the Windows® Network Neighborhood.
Apply NAT and Firewall Rules - This feature allows a remote site’s LAN subnet to be hidden from the corporate site, and is most useful when a remote office’s network traffic is initiated to the corporate office. The IPSec tunnel is located between the SonicWALL WAN interface and the LAN segment of the corporation. To protect the traffic, NAT (Network Address Translation) is performed on the outbound packet before it is sent through the tunnel, and in turn, NAT is performed on inbound packets when they are received. By using NAT for a VPN connection, computers on the remote LAN are viewed as one address (the SonicWALL public address) from the corporate LAN.
SAlert:selected.Offices can have overlapping LAN IP ranges if the Apply NAT and Firewall Rules feature is
SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE | 205 |