CHAPTER 36: Configuring VPN Settings
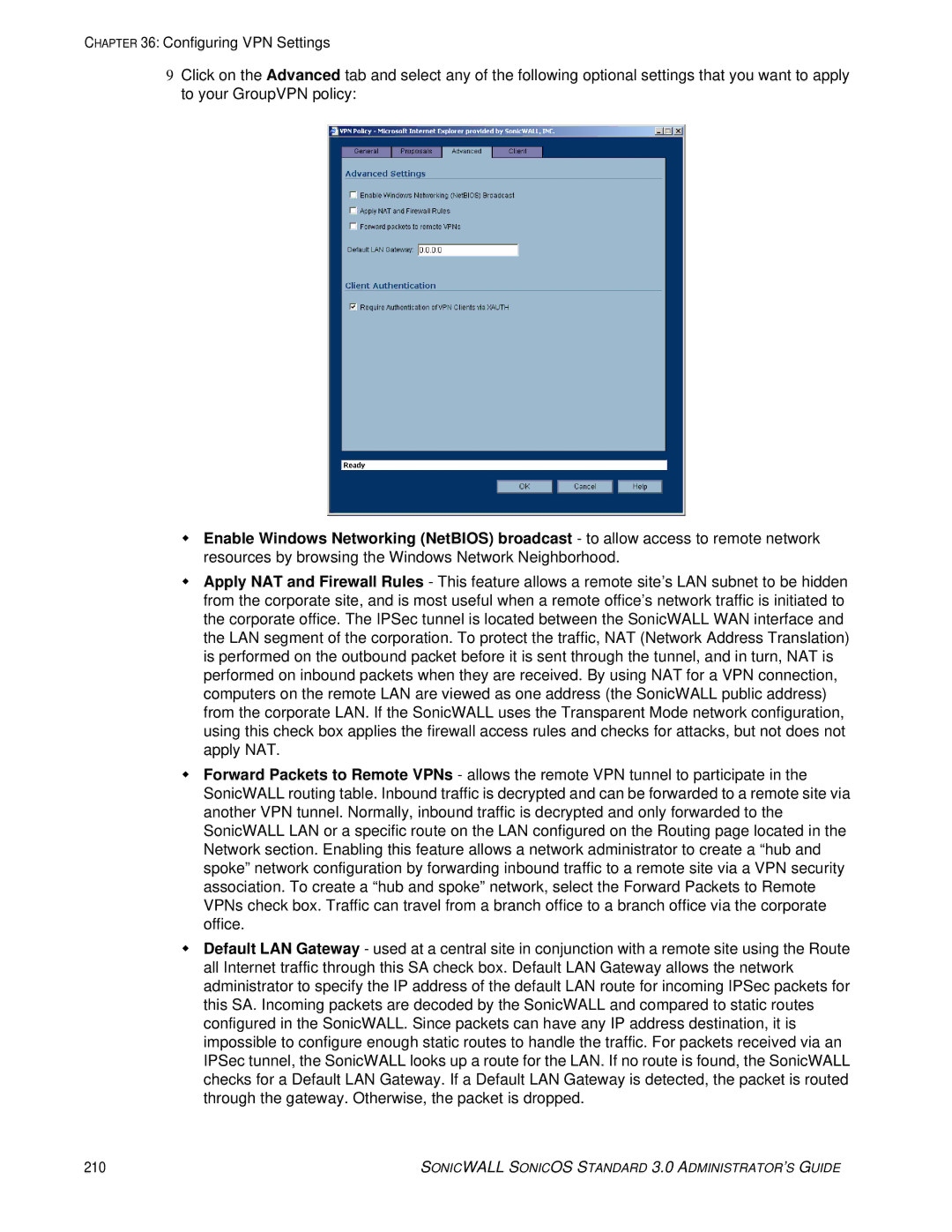
9Click on the Advanced tab and select any of the following optional settings that you want to apply to your GroupVPN policy:
Enable Windows Networking (NetBIOS) broadcast - to allow access to remote network resources by browsing the Windows Network Neighborhood.
Apply NAT and Firewall Rules - This feature allows a remote site’s LAN subnet to be hidden from the corporate site, and is most useful when a remote office’s network traffic is initiated to the corporate office. The IPSec tunnel is located between the SonicWALL WAN interface and the LAN segment of the corporation. To protect the traffic, NAT (Network Address Translation) is performed on the outbound packet before it is sent through the tunnel, and in turn, NAT is performed on inbound packets when they are received. By using NAT for a VPN connection, computers on the remote LAN are viewed as one address (the SonicWALL public address) from the corporate LAN. If the SonicWALL uses the Transparent Mode network configuration, using this check box applies the firewall access rules and checks for attacks, but not does not apply NAT.
Forward Packets to Remote VPNs - allows the remote VPN tunnel to participate in the SonicWALL routing table. Inbound traffic is decrypted and can be forwarded to a remote site via another VPN tunnel. Normally, inbound traffic is decrypted and only forwarded to the SonicWALL LAN or a specific route on the LAN configured on the Routing page located in the Network section. Enabling this feature allows a network administrator to create a “hub and spoke” network configuration by forwarding inbound traffic to a remote site via a VPN security association. To create a “hub and spoke” network, select the Forward Packets to Remote VPNs check box. Traffic can travel from a branch office to a branch office via the corporate office.
Default LAN Gateway - used at a central site in conjunction with a remote site using the Route all Internet traffic through this SA check box. Default LAN Gateway allows the network administrator to specify the IP address of the default LAN route for incoming IPSec packets for this SA. Incoming packets are decoded by the SonicWALL and compared to static routes configured in the SonicWALL. Since packets can have any IP address destination, it is impossible to configure enough static routes to handle the traffic. For packets received via an IPSec tunnel, the SonicWALL looks up a route for the LAN. If no route is found, the SonicWALL checks for a Default LAN Gateway. If a Default LAN Gateway is detected, the packet is routed through the gateway. Otherwise, the packet is dropped.
210 | SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE |