CHAPTER 36: Configuring VPN Settings
Configuring GroupVPN with IKE 3rd Party Certificates
To configure your GroupVPN policy with IKE 3rd Party Certificates, follow these steps:
SAlert: Before configuring GroupVPN with IKE using 3rd Party Certificates, your certificates must be installed on the SonicWALL.
1In the VPN > Settings page click the edit The VPN Policy window is displayed.
icon under Configure for the GroupVPN entry.
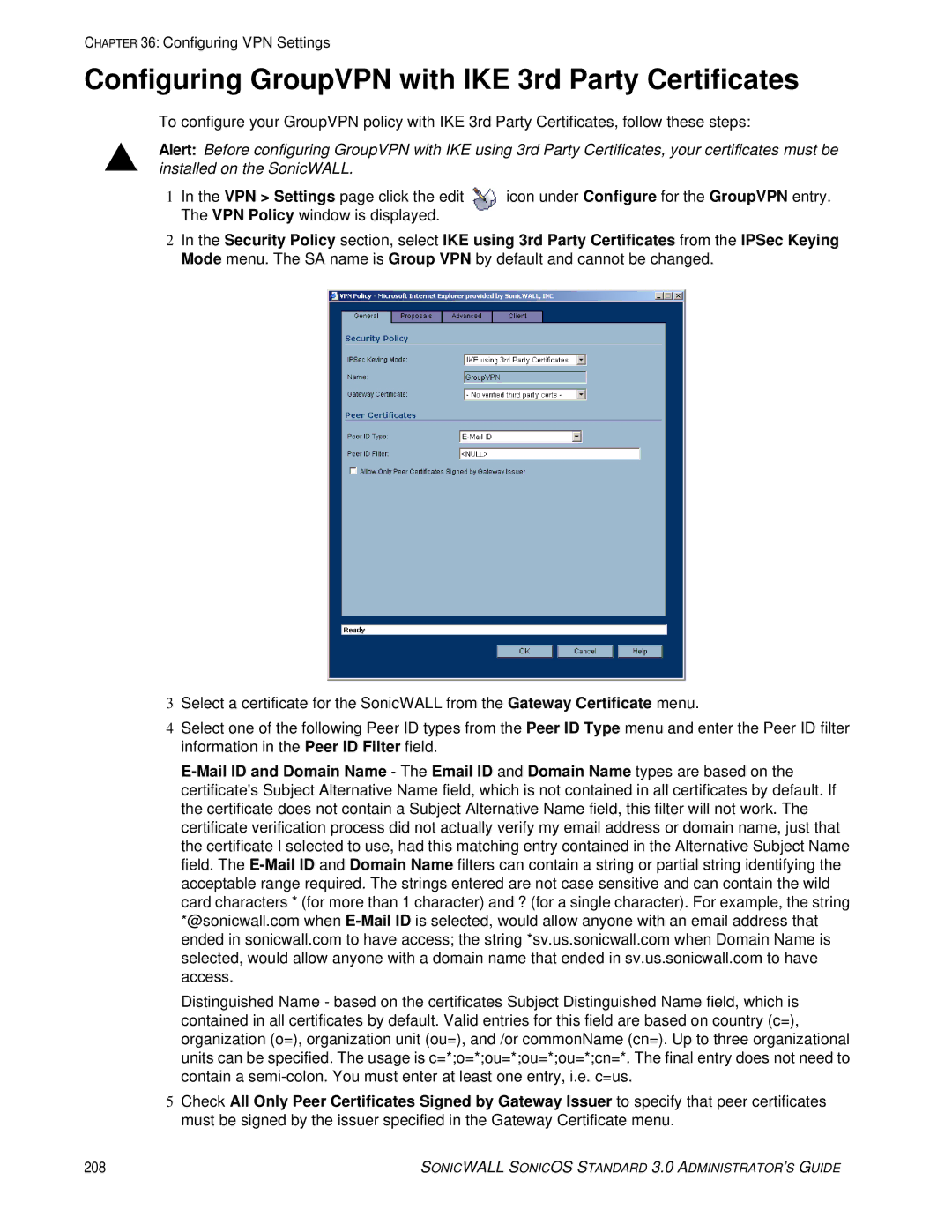
2In the Security Policy section, select IKE using 3rd Party Certificates from the IPSec Keying Mode menu. The SA name is Group VPN by default and cannot be changed.
3Select a certificate for the SonicWALL from the Gateway Certificate menu.
4Select one of the following Peer ID types from the Peer ID Type menu and enter the Peer ID filter information in the Peer ID Filter field.
Distinguished Name - based on the certificates Subject Distinguished Name field, which is contained in all certificates by default. Valid entries for this field are based on country (c=), organization (o=), organization unit (ou=), and /or commonName (cn=). Up to three organizational units can be specified. The usage is c=*;o=*;ou=*;ou=*;ou=*;cn=*. The final entry does not need to contain a
5Check All Only Peer Certificates Signed by Gateway Issuer to specify that peer certificates must be signed by the issuer specified in the Gateway Certificate menu.
208 | SONICWALL SONICOS STANDARD 3.0 ADMINISTRATOR’S GUIDE |