Chapter 10: 802.1x
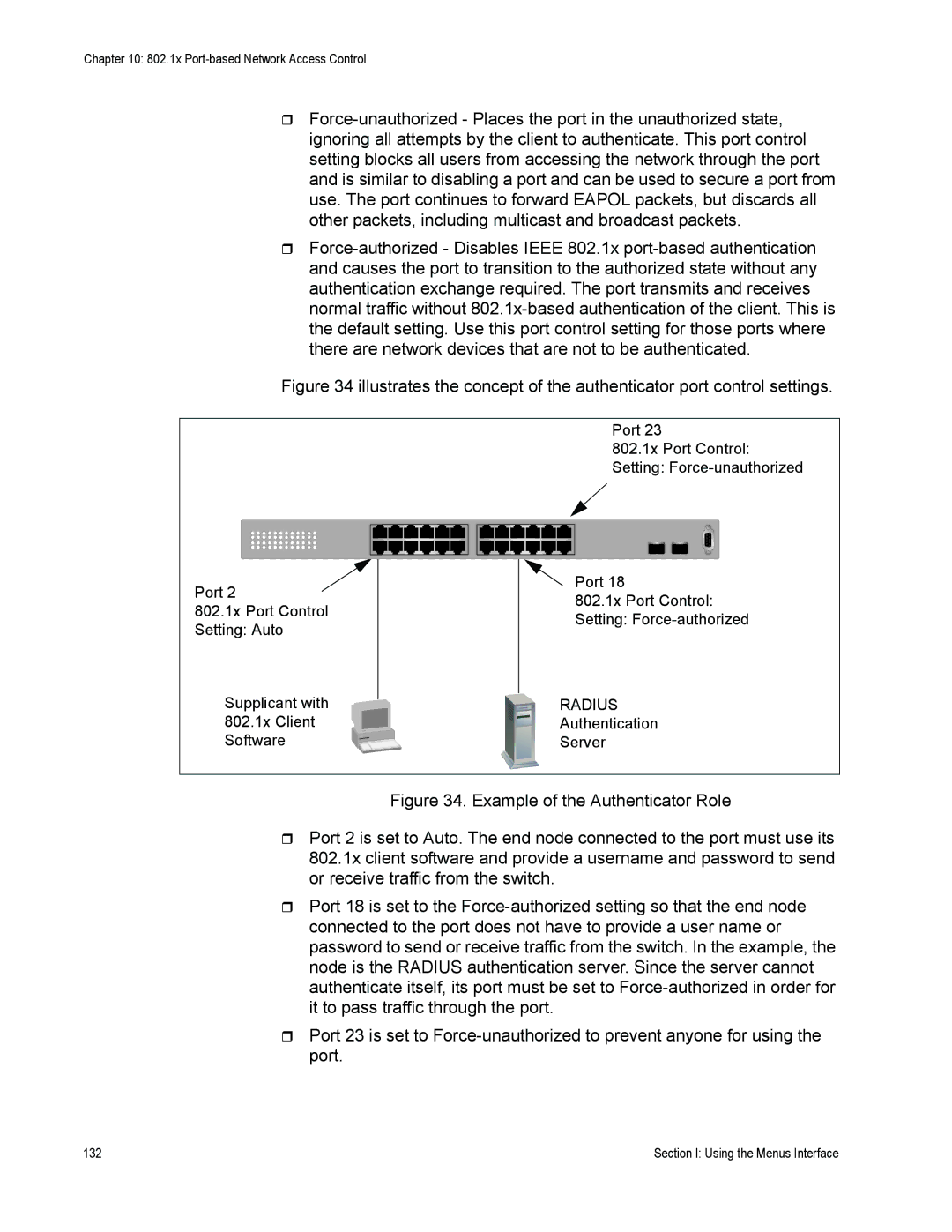
Figure 34 illustrates the concept of the authenticator port control settings.
Port 23
802.1x Port Control:
Setting:
Port 2
802.1x Port Control
Setting: Auto
Supplicant with 802.1x Client Software
Port 18
802.1x Port Control:
Setting:
RADIUS
Authentication
Server
Figure 34. Example of the Authenticator Role
Port 2 is set to Auto. The end node connected to the port must use its 802.1x client software and provide a username and password to send or receive traffic from the switch.
Port 18 is set to the Force-authorized setting so that the end node connected to the port does not have to provide a user name or password to send or receive traffic from the switch. In the example, the node is the RADIUS authentication server. Since the server cannot authenticate itself, its port must be set to Force-authorized in order for it to pass traffic through the port.
Port 23 is set to Force-unauthorized to prevent anyone for using the port.
132 | Section I: Using the Menus Interface |