HP 10Gb Ethernet BL-c Switch
Legal notices
Contents
Statistics Menu
100
102
101
103
105
164
163
165
168
Index 224
Connecting to the switch
Introduction
Additional references
Setting an IP address
Establishing a console connection
Parameter Value
Establishing a Telnet connection
Telnet 10GbE switch IP address
Establishing an SSH connection
3DES
Accessing the switch
You will then be prompted to enter your password
# ssh user@10Gb switch IP address
User account Description and tasks performed
Idle timeout
Typographical conventions
Typeface or Meaning Example Symbol
AaBbCc123
Address
Menu summary
Main Menu
Following table describes the global commands
Global commands
Command Action
Or print
Exit or Quit
Traceroute host name IP address max-hops msec delay
Verbose n
Telnet hostname IP address port -m-mgt-d-data
Option Description
Command line history and editing
Command stacking
Command line interface shortcuts
Command abbreviation
Tab completion
Main# /cfg
Configuration Menu is displayed
Configuring Simple Network Management Protocol support
Setting passwords
Changing the default administrator password
Use the following command to enable Snmp
Enter the new administrator password at the prompt
Enter the current administrator password at the prompt
Enter the new administrator password, again, at the prompt
System Menu is displayed
Changing the default operator password
Changing the default user password
Enter the new operator password, again, at the prompt
Enter the new operator password at the prompt
Enter new operator password
Re-enter new operator password
Command Usage
Command /info
Menu overview
Following table describes the Information Menu options
System Information Menu
Command /info/sys
SNMPv3 Information Menu
Command /info/sys/snmpv3
Command /info/sys/snmpv3/view
Command /info/sys/snmpv3/usm
SNMPv3 USM User Table information
SNMPv3 View Table information
SNMPv3 Access Table information
Command /info/sys/snmpv3/access
Following table describes the SNMPv3 View Table information
Command /info/sys/snmpv3/comm
Command /info/sys/snmpv3/group
SNMPv3 Group Table information
SNMPv3 Community Table information
Command /info/sys/snmpv3/tparam
Command /info/sys/snmpv3/taddr
SNMPv3 Target Address Table information
SNMPv3 Target Parameters Table information
Command /info/sys/snmpv3/notify
SNMPv3 Notify Table information
NameTag V1v2trapv1v2trap
SNMPv3 dump
Command /info/sys/snmpv3/dump
System information
Command /info/sys/gen
Show last 100 syslog messages
Command /info/sys/log
Cfg/sys/access/user/uid command
Command /info/sys/user
System user information
Following table describes the User Name information
Layer 2 information
Command /info/l2
FDB information menu
Command /info/l2/fdb
Find MAC address Vlan
Port port number
Command /info/l2/lacp
Command /info/l2/fdb/dump
Link Aggregation Control Protocol information
Show all FDB information
Command /info/l2/hotlink/trigger
Command /info/l2/lacp/dump
Hot Links Trigger information
Lacp dump
Command /info/l2/8021x
802.1X information
Following table describes the Ieee 802.1X parameters
Backend Auth State
Authenticator PAE State
Spanning Tree information
Command /info/l2/stp
Parameters Description
Rapid Spanning Tree / Multiple Spanning Tree information
Desg 8017 P2P2,Edge
Desg 8018
Parameter Description
Common Internal Spanning Tree information
Command /info/l2/cist
Cist Root
Following table describes the Cist parameters
Command /info/l2/vlan
Command /info/l2/trunk
Trunk group 1, Enabled port state STG 1 forwarding
Trunk group information
STP uplink fast mode disabled
Command /info/l2/uplink
STP uplink fast mode
Fast Uplink Convergence status
Layer 3 information
Command /info/l3
Command /info/l3/route/dump
Command /info/l3/route
Route information
Show all IP Route information
Following table describes the Tag parameter
Following table describes the Type parameter
Command /info/arp/dump
Command /info/arp
ARP information
Show all ARP entry information
Command /info/l3/ospf
Command /info/arp/addr
Ospf information
ARP address list information
Command /info/l3/ospf/if
Command /info/l3/ospf/general
Ospf general information
Ospf interface information
Ospf Database information menu
Command /info/l3/ospf/dbase
Ospf route codes information
Command /info/l3/ospf/routes
Rtr adv-rtr A.B.C.D
Linkstateid A.B.C.Dself
RIP user configuration
Routing Information Protocol information
RIP Routes information
IP information
Command /info/l3/ip
Timer information
Command /info/l3/igmp
Command /info/l3/igmp/dump
Igmp multicast group information
4094
Igmp multicast router information
Vrrp information
Command /info/l3/vrrp
Server Mobility Port information
Command /info/l3/sm/port
Command /info/qos/8021p
Command /info/qos
QoS information
802.1p information
ACL information
Command /info/acl
Command /info/rmon/hist
Command /info/rmon
Rmon Information Menu
Rmon history information
Command /info/rmon/alarm
Rmon alarm information
Trap, both
Command /info/rmon/event
Link status information
Command /info/link
Command /info/transcvr
Command /info/port
Port information
Transceiver status
Command /info/dump
Command /info/ufd
Uplink Failure Detection information
Information dump
Menu information
Command /stats
Following table describes the Statistics Menu options
Ntp clear
Command /stats/port port number
Port Statistics Menu
Sfd clear
Command /stats/port port number/8021x
802.1X statistics
Statistics Port
BackendNonNakResponsesFromSupplic ant
Command /stats/port port number/brg
Bridging statistics
Statistics Description
Ethernet statistics
Command /stats/port port number/ether
Dot3StatsCarrierSenseErrors object
Dot3StatsInternalMacTransmitErrors
Dot3StatsMultipleCollisionFrames
Dot3StatsSingleCollisionFrames object
Interface statistics
Command /stats/port port number/if
Errors-IfHCOut
Errors-IfHCIn
Octets-IfHCOut
UcastPkts-IfHCOut
Command /stats/port port number/link
Command /stats/port port number/ip
Internet Protocol IP statistics
Link statistics
Port Rmon statistics
Command /stats/port port number/rmon
EtherStatsJabbers
EtherStatsFragments
EtherStatsCollisions
EtherStatsPkts64Octets
Command /stats/l2/lacp port number
Command /stats/l2/fdb
Layer 2 statistics
FDB statistics
Hot Links statistics
Command /stats/l2/hotlink
Following table describes the Hot Links statistics
Statistic Description
Layer 3 statistics
Command /stats/l3
Arp clear
Igmpgrps
Command /stats/l3/geal3/dump
Command /stats/l3/geal3
GEA Layer 3 statistics menu
GEA statistics
Command /stats/l3/ip
IP statistics
Following table describes the IP statistics
ARP statistics
DNS statistics
Route statistics
Icmp statistics
Command /stats/l3/icmp
TCP statistics
Command /stats/l3/tcp
Semantics of the Ubound quantity described in RFC
Command /stats/l3/igmp Vlan number
Command /stats/l3/udp
UDP statistics
Igmp Multicast Group statistics
Command /stats/l3/ospf
Ospf statistics menu
Following table describes the Ospf statistics menu options
Command /stats/l3/ospf/general
Ospf global statistics
Following table describes the Ospf global statistics
Tx ls Updates
Rx ls Updates
Rx ls Acks
Tx ls Acks
Nbr change
Timers Kickoff Hello
Command /stats/l3/vrrp
Vrrp statistics
Following table describes the Vrrp statistics
RIP statistics
Command /stats/l3/rip
Command /stats/mp/pkt
Management Processor statistics
Packet statistics
Command /stats/mp/ucb
Command /stats/mp/tcb
Access Control List ACL statistics menu
CPU statistics
ACL statistics
Snmp statistics
Command /stats/snmp
NoSuchName
NTP statistics
Command /stats/ntp
Uplink Failure Detection statistics
Command /stats/ufd
Following table describes the NTP statistics
Primary Server
Statistics dump
Command /stats/dump
Following table describes the Configuration Menu options
Command /cfg
Viewing pending changes
Viewing, applying, reverting, and saving changes
Applying pending changes
Reverting changes
Reminders
Saving the configuration
Cfg/sys/reminders dis
# save
Command /cfg/sys
System configuration
Address. The default value is enabled
System host log configuration
Command /cfg/sys/syslog
Multi-line to end
Console disableenable
Command Description
Log featureall enabledisable
Host IP address
Command /cfg/sys/sshd
Secure Shell Server configuration
Intrval
Sshport TCP port number
Command /cfg/sys/radius
Radius server configuration
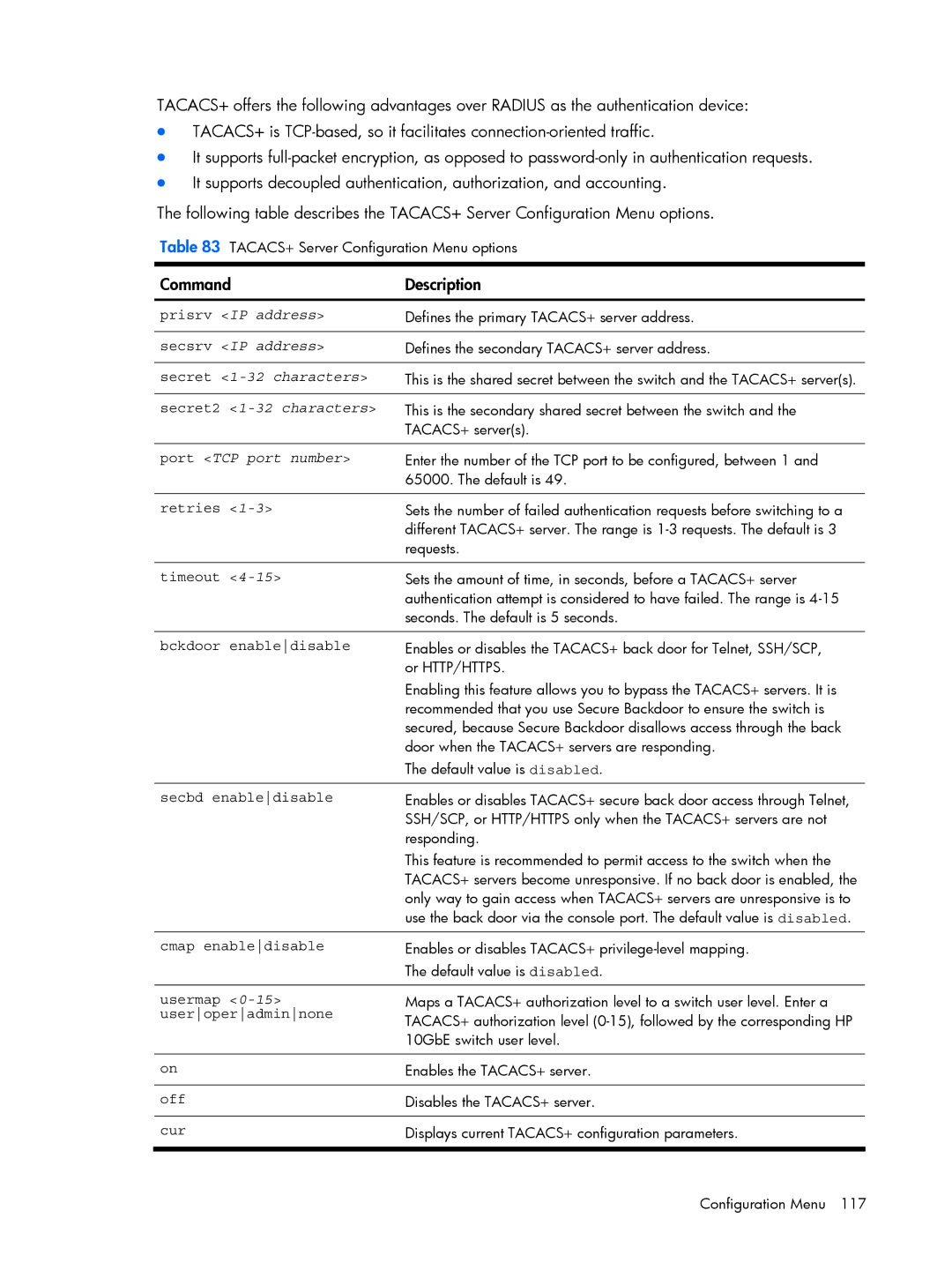
Command /cfg/sys/tacacs+
TACACS+ server configuration
Cmap enabledisable
Useroperadminnone
Port TCP port number
NTP server configuration
Command /cfg/sys/ntp
Mgtdata
Command /cfg/sys/ssnmp
System Snmp configuration
SNMPv3 configuration
Command /cfg/sys/ssnmp/snmpv3
Wcomm 1-32 characters
User Security Model configuration
Command /cfg/sys/ssnmp/snmpv3/usm
V1v2 disableenable
Command /cfg/sys/ssnmp/snmpv3/view
SNMPv3 View configuration
Name 1-32 characters
Characters
Command /cfg/sys/ssnmp/snmpv3/access
View-based Access Control Model configuration
Rview 1-32 characters
Wview 1-32 characters
SNMPv3 Community Table configuration
SNMPv3 Group configuration
Command /cfg/sys/ssnmp/snmpv3/group
Command /cfg/sys/ssnmp/snmpv3/comm
Command /cfg/sys/ssnmp/snmpv3/taddr
SNMPv3 Target Address Table configuration
Command /cfg/sys/ssnmp/snmpv3/tparam
SNMPv3 Target Parameters Table configuration
AuthPriv
Snmpv1snmpv2csnmpv3
SNMPv3 Notify Table configuration
System Access configuration
Command /cfg/sys/ssnmp/snmpv3/notify
Command /cfg/sys/access
Command /cfg/sys/access/mgmt
Management Networks configuration
User ID configuration
User Access Control configuration
Command /cfg/sys/access/user
Command /cfg/sys/access/user/uid
Https Access configuration
Command /cfg/sys/access/https
Access enabledisable
Command /cfg/port port number
Port configuration
Port link configuration
Command /cfg/port port number/gig
Temporarily disabling a port
Command /cfg/port port number/aclqos
Port ACL/QoS configuration
Command /cfg/port port number/stp
Port Pvrst configuration
Edge enabledisable
Link autop2pshared
Command /cfg/l2
Layer 2 configuration
Enabledisable
Bpdugrd enabledisable
Command /cfg/l2/8021x
802.1X configuration
802.1X Global configuration
Command /cfg/l2/8021x/global
CommandDescription
802.1X Port configuration
Command /cfg/l2/8021x/port port number
802.1X Port Configuration Menu
Applies the global 802.1X parameters to the port
Command /cfg/l2/mrst
Rev
Rstpmstppvrst
Following configurations are unsupported
Common Internal Spanning Tree configuration
Following configurations are supported
Command /cfg/l2/mrst/cist
Command /cfg/l2/mrst/cist/brg
Cist bridge configuration
Cist port configuration
Command /cfg/l2/mrst/cist/port port number
Cost
Spanning Tree configuration
Command /cfg/l2/stp
Edge disableenable
Command /cfg/l2/stp/brg
Bridge Spanning Tree configuration
Command /cfg/l2/stp 1-128/port port number
Spanning Tree port configuration
Fastfwd disableenable
Static FDB configuration
Forwarding Database configuration
Command /cfg/l2/fdb
Command /cfg/l2/fdb/static
Command /cfg/l2/trunk
Trunk configuration
Add port number
Rem port number
Layer 2 IP Trunk Hash configuration
IP Trunk Hash configuration
Command /cfg/l2/thash
Command /cfg/l2/thash/set
Lacp Port configuration
Link Aggregation Control Protocol configuration
Command /cfg/l2/lacp
Command /cfg/l2/lacp/port port number
Vlan configuration
Command /cfg/l2/vlan
Def list of port numbers
Command /cfg/l2/vlan x/pvlan
Protocol Vlan configuration
Pty Ether2SNAPLLC
Ethernet type
Command /cfg/l2/vlan x/privlan
Private Vlan configuration
Tagpvl enabledisable
Type primaryisolatedcommunity
Command /cfg/l2/hotlink
Hot Links configuration
Bpdu enabledisable
Sndfdb enabledisable
Hot Links Master configuration
Hot Links Trigger configuration
Command /cfg/l2/hotlink/trigger
Command /cfg/l2/hotlink/trigger 1-4/master
Hot Links Backup configuration
Command /cfg/l2/hotlink/trigger 1-4/backup
Following table describes the Hot Links Backup Menu options
Layer 3 configuration
Command /cfg/l3
Gw 1-4
Command /cfg/l3/if
IP interface configuration
Relay disableenable
Addr IP address
Default Gateway configuration
Command /cfg/l3/gw 1-4
Arp disableenable
Address Resolution Protocol configuration
IP Static Route configuration
Command /cfg/l3/route
Command /cfg/l3/arp
IP Forwarding configuration
Static ARP configuration
Command /cfg/l3/arp/static
Command /cfg/l3/frwd
Route Map configuration
Network Filter configuration
Command /cfg/l3/nwf
Command /cfg/l3/rmap
Command /cfg/l3/rmap 1-32/alist
IP Access List configuration
Type 12none
Metric 1-16777214none
Command /cfg/l3/rip
Routing Information Protocol configuration
Current Display current RIP configuration
Off Globally turn
Command /cfg/l3/rip/if
RIP Interface configuration
Command /cfg/l3/rip/redist fixedstaticospfeospf
RIP Route Redistribution configuration
Add 1-32 1-32all
Remove 1-32 1-32all
Open Shortest Path First configuration
Command /cfg/l3/ospf
Md5key 1-255 characters
Command /cfg/l3/ospf/aindex
Osfp Area Index configuration
Auth nonepasswordmd5
Areaid IP address
Ospf Summary Range configuration
Ospf Interface configuration
Command /cfg/l3/ospf/range
Command /cfg/l3/ospf/if
Mdkey 1-255none
Key key stringnone
Command /cfg/l3/ospf/virt
Ospf Virtual Link configuration
Key password
Nbr IP address
Ospf Route Redistribution configuration
Ospf Host Entry configuration
Command /cfg/l3/ospf/host
Command /cfg/l3/ospf/redist fixedstaticrip
Command /cfg/l3/ospf/md5key key ID
Ospf MD5 Key configuration
Export 1-16777215 12none
Key 1-16 characters
Igmp snooping configuration
Igmp configuration
Command /cfg/l3/igmp
Command /cfg/l3/igmp/snoop
Aggr disableenable
Flood disableenable
Ports
Igmpv3
Command /cfg/l3/igmp/snoop/igmpv3
IGMPv3 Snooping configuration
Igmp filtering configuration
Igmp static multicast router configuration
Add port number 1-4094
Remove port number
Command /cfg/l3/igmp/igmpflt/filter
Igmp filtering port configuration
Command /cfg/l3/igmp/igmpflt/port port number
Igmp filter definition
Bootstrap Protocol Relay configuration
Domain Name System configuration
Command /cfg/l3/dns
Command /cfg/l3/bootp
Command /cfg/l3/sm
Server Mobility configuration
Filter enabledisable
Nsmrelay enabledisable
Command /cfg/l3/sm/port port number
Server Mobility port configuration
Addback port number
Remback port number
Virtual Router Redundancy Protocol configuration
Command /cfg/l3/vrrp
Cur Display current Vrrp configuration
Command /cfg/l3/vrrp/vr
Vrrp Virtual Router configuration
Command /cfg/l3/vrrp/vr 1-250/track
Vrrp Virtual Router Priority Tracking configuration
Preem disableenable
Switch ports
Command /cfg/l3/vrrp/group
Vrrp Virtual Router Group configuration
Vrs disableenable
Ifs disableenable
Virtual Router Group Configuration Menu options
Vrrp Interface configuration
Vrrp Virtual Router Group Priority Tracking configuration
Command /cfg/l3/vrrp/group/track
Command /cfg/l3/vrrp/if
Command /cfg/l3/vrrp/track
Vrrp Tracking configuration
QoS 802.1p configuration
Quality of Service configuration
Command /cfg/qos
Command /cfg/qos/8021p
Access Control List configuration
Access Control configuration
Command /cfg/acl
Command /cfg/acl/acl
Command /cfg/acl/acl 1-384/ethernet
ACL Ethernet Filter configuration
Command /cfg/acl/acl 1-384/ipv4
ACL IP Version 4 Filter configuration
Sip IP address IP mask
Dip IP address IP mask
Command /cfg/acl/acl 1-384/tcpudp
ACL TCP/UDP Filter configuration
Filtering TCP/UDP Menu
Sport 1-65535 port mask
ACL Re-mark configuration
ACL Meter configuration
Command /cfg/acl/acl 1-384/meter
Command /cfg/acl/acl 1-384/re-mark
ACL Re-mark In-Profile Update User Priority configuration
ACL Re-mark In-Profile configuration
Command /cfg/acl/acl 1-384/re-mark/inprof
Command /cfg/acl/acl 1-384/re-mark/inprof/up1p
ACL Re-mark Out-of-Profile configuration
ACL Packet Format configuration
Command /cfg/acl/acl 1-384/re-mark/outprof
Command /cfg/acl/acl 1-384/pktfmt
Command /cfg/acl/group
ACL Group configuration
Add acl
Rem acl
Rmon history configuration
Remote Monitoring configuration
Command /cfg/rmon
Command /cfg/rmon/hist
Command /cfg/rmon/event
Rmon event configuration
Following table describes the Rmon Event Menu options
Owner 1-127 characters
Command /cfg/rmon/alarm
Rmon alarm configuration
Oid 1-127 characters
Rlimit -2147483647 to
Mirror disableenable
Command /cfg/pmirr
Port mirroring
Monport port number
Port-based port mirroring
Command /cfg/pmirr/monport port number
Add mirrored port inoutboth
Rem mirrored port
Failure Detection Pair configuration
Uplink Failure Detection configuration
Command /cfg/ufd
Command /cfg/ufd/fdp
Command /cfg/ufd/fdp/ltm
Link to Monitor configuration
Removes a Lacp admin key from the LtM
Addport port number
Addport port number Remport port number
Link to Disable configuration
Addtrunk
Remtrunk Addkey Remkey Cur
Restoring the active switch configuration
Saving the active switch configuration
Command /cfg/ptcfg FTP/TFTP server filename
Command /cfg/gtcfg FTP/TFTP server filename
Command /oper/port port number
Command /oper
Operations-level port options
Following table describes the Operations Menu options
Command /oper/port port number/8021x
Rmon disableenable
Operations-level port 802.1X options
Command /oper/vrrp
Vrrp Operations Menu Back Set virtual router to backup
Operations-level Vrrp options
Updating the switch software image
Downloading new software to the switch
Command /boot
Enter the hostname or IP address of the FTP or Tftp server
Enter the password for the FTP server if prompted
Enter the name of the new software file on the server
Enter the port type to use for the file transfer
Selecting a software image to run
Uploading a software image from the switch
New choice
System prompts you for information. Enter the desired image
Resetting the switch
Selecting a configuration block
Boot Options# conf
Boot Options# reset
Accessing the Iscli
Boot Options# mode iscli
Switch# boot cli-mode aos
Command /maint
Maintenance Menu
Command /maint/sys
System maintenance options
System Maintenance Menu Flags Set Nvram flag word
Flags new Nvram flags word as
Command /maint/debug
Command /maint/fdb
Forwarding Database options
Debugging options
Command /maint/arp
ARP cache options
MP trace buffer at 132815 Fri May 25, 2002 mask 0x2ffdf748
Command /maint/igmp
Command /maint/route
IP Route Manipulation options
Igmp Multicast Group options
Command /maint/igmp/mrouter
Command /maint/igmp/snoop
Igmp Snooping options
Igmp Mrouter options
Uuencode flash dump
FTP/TFTP system dump put
Clearing dump information
Command /maint/panic
Panic command
Enter y to confirm the command
Unscheduled system dumps
Index
Page
Rmon
Snmp
Vrrp