Text Part Number OL-9775-02
Americas Headquarters
Page
Iii
N T E N T S
Assigning the Switch IP Address and Default Gateway
Understanding Cisco Configuration Engine Software
Clustering Switches
Vii
Catalyst 1900 and Catalyst 2820 CLI Considerations
Viii
Creating a Banner
Changing the Default Privilege Level for Lines
Device Roles
Bypass
Xii
Routed Ports
Xiii
Monitoring and Maintaining the Interfaces
Xiv
Encapsulation Types
Domain Names
Xvi
Private-VLAN Configuration Guidelines
Xvii
Disabled State
Xviii
Boundary Ports
19-25
Xix
Dhcp Server
Xxi
Configuring Dynamic ARP Inspection
Xxii
Configuring MVR
Xxiii
Understanding Storm Control
Xxiv
Understanding Udld Modes of Operation
Xxv
Creating an Rspan Source Session
Xxvi
Snmp Agent Functions
Xxvii
Creating a Numbered Extended ACL
Xxviii
Interaction with Other Features and Switches
Xxix
Xxx
Port-Channel Interfaces
Xxxi
Configuring IP Addressing
Xxxii
Nonstop Forwarding Awareness
Xxxiii
IPv6 Addresses
Xxxiv
Configuring Hsrp Priority
Xxxv
Configuring IP Multicast Routing
Xxxvi
Configuring Basic Dvmrp Interoperability Features
Xxxvii
Using a Filter
45-14
Xxxviii
Xxxix
Configuring Online Diagnostics
Unsupported Route-Map Configuration Commands C-1
Xli
Hsrp
Xlii
VTP
Audience
Preface
Purpose
Conventions
Xliv
Related Publications
Xlv
Xlvi
Overview
Features
Availability and Redundancy Features, Vlan Features,
Deployment Features
Overview Features
Performance Features
Management Options
Manageability Features
Availability and Redundancy Features
Security Features
Vlan Features
Overview Features
QoS and CoS Features
Layer 3 Features
Power over Ethernet Features
Monitoring Features
Default Settings After Initial Switch Configuration
Vlan
Overview Default Settings After Initial Switch Configuration
Overview Default Settings After Initial Switch Configuration
Design Concepts for Using the Switch
Network Configuration Examples
Network Demands Suggested Design Methods
Cost-Effective Wiring Closet
High-Performance Wiring Closet
High-Performance Workgroup Gigabit-to-the-Desktop
Redundant Gigabit Backbone
Server Aggregation
Linux Server Cluster
Cisco SoftPhone Software Gigabit servers
Internet Cisco 2600 or 3700 routers Catalyst 3560-E switches
Large Network Using Catalyst 3750-E and 3560-E Switches
Cisco 7x00 routers Catalyst
Catalyst 3560-E
Multidwelling Network Using Catalyst 3750-E Switches
11 Catalyst 3750-E Switches in a MAN Configuration
Long-Distance, High-Bandwidth Transport Configuration
Access layer Aggregation layer
Where to Go Next
OL-9775-02
Understanding Command Modes
Using the Command-Line Interface
Configure
Mode Access Method Prompt Exit Method About This Mode
Quit
Ctrl-Z
Command Purpose
Console command
Understanding the Help System
Line vty or line
Understanding no and default Forms of Commands
Understanding Abbreviated Commands
Command ?
Command keyword ?
Using Configuration Logging
Understanding CLI Error Messages
Error Message Meaning How to Get Help
Changing the Command History Buffer Size
Using Command History
Recalling Commands
Action1 Result
Disabling the Command History Feature
Using Editing Features
Enabling and Disabling Editing Features
Switch# terminal editing
Capability Keystroke1 Purpose
Editing Commands through Keystrokes
Return and Space bar
Editing Command Lines that Wrap
Press Ctrl-L or Ctrl-R
Command begin include exclude regular-expression
Accessing the CLI
Switch# show interfaces include protocol
Using the Command-Line Interface Accessing the CLI
OL-9775-02
Understanding the Boot Process
Assigning the Switch IP Address and Default Gateway
Assigning Switch Information
Understanding DHCP-Based Autoconfiguration
Default Switch Information
Feature Default Setting
Dhcp Client and Server Message Exchange
Dhcp Client Request Process
Dhcp Server Configuration Guidelines
Configuring DHCP-Based Autoconfiguration
Configuring the DNS
Configuring the Tftp Server
Obtaining Configuration Files
Configuring the Relay Device
Routerconfig-if#ip helper-address
Tftpserver
Example Configuration
DNS Server Configuration
Switch a Switch B Switch C Switch D
Tftp Server Configuration on Unix
Dhcp Client Configuration
Manually Assigning IP Information
Switch# show running-config
Checking and Saving the Running Configuration
Switch# copy running-config startup-config
Default Boot Configuration
Modifying the Startup Configuration
Automatically Downloading a Configuration File
Boot config-file flash/ file-url
Booting Manually
Show boot
Configure terminal Enter global configuration mode
Boot system filesystem /file-url
Booting a Specific Software Image
Controlling Environment Variables
Boot system switch number all
Set Switchnumber
Set Manualboot yes Boot manual
Switch current-stack-member-number renumber
Set Switchpriority
Scheduling a Reload of the Software Image
Configuring a Scheduled Reload
Variable Description
Reload in hhmm text
Switch# reload at 0200 jun
Switch# reload at
Displaying Scheduled Reload Information
Understanding Cisco Configuration Engine Software
Configuring Cisco IOS CNS Agents
Configuration Engine Architectural Overview
Configuration Service
ConfigID
Event Service
What You Should Know About the CNS IDs and Device Hostnames
NameSpace Mapper
DeviceID
Using Hostname, DeviceID, and ConfigID
Hostname and DeviceID
Understanding Cisco IOS Agents
Initial Configuration
Incremental Partial Configuration
Configuring Cisco IOS Agents
Synchronized Configuration
Enabling Automated CNS Configuration
Device Required Configuration
Show running-config
Backup init-retry retry-count keepalive seconds
Enabling the CNS Event Agent
Show cns event connections
Enabling the Cisco IOS CNS Agent
Enabling an Initial Configuration
Cns id interface num dns-reverse ipaddress
Cns config initial ip-address hostname
Mac-address event
Cns id hardware-serial hostname string string
Show running-config Verify your entries
Enabling a Partial Configuration
Cns config partial ip-address hostname
Show cns config stats
Show cns config connections
Displaying CNS Configuration
Show cns event stats
Show cns event subject
Understanding Switch Stacks
Managing Switch Stacks
Managing Switch Stacks Understanding Switch Stacks
Switch Stack Membership
Creating a Switch Stack from Two Standalone Switches
Stack Master Election and Re-Election
Adding a Standalone Switch to a Switch Stack
Stack Member Numbers
Switch Stack Bridge ID and Router MAC Address
Stack Member Priority Values
Effects of Adding a Provisioned Switch to a Switch Stack
Switch Stack Offline Configuration
Scenario Result
Scenario Result
Effects of Replacing a Provisioned Switch in a Switch Stack
Switch Stack Software Compatibility Recommendations
Minor Version Number Incompatibility Among Switches
Major Version Number Incompatibility Among Switches
Stack Protocol Version Compatibility
Understanding Auto-Upgrade and Auto-Advise
Switch
Auto-Upgrade and Auto-Advise Example Messages
Directory
Mar 1 000422.537%IMAGEMGR-6-AUTOADVISESW
Switch Stack Configuration Files
Incompatible Software and Stack Member Image Upgrades
Switch Stack Management Connectivity
Connectivity to the Switch Stack Through an SSH Session
Connectivity to the Switch Stack Through an IP Address
Connectivity to Specific Stack Members
Use the switch stack-member-number
Switch Stack Configuration Scenarios
Priority new-priority-number global
Current-stack-member-number Renumber new-stack-member-number
Default Switch Stack Configuration
Configuring the Switch Stack
Enabling Persistent MAC Address
Show switch
Stack-mac persistent timer
Switchconfig# stack-mac persistent timer
Time-value
Assigning Stack Member Information
Setting the Stack Member Priority Value
Assigning a Stack Member Number
Provisioning a New Member for a Switch Stack
Displaying Switch Stack Information
Accessing the CLI of a Specific Stack Member
Command Description
Show switch stack-member-number
Show switch stack-ring activity
Show switch stack-ports
Detail
OL-9775-02
Understanding Switch Clusters
Clustering Switches
Switch Cisco IOS Release Cluster Capability
Standby Cluster Command Switch Characteristics
Cluster Command Switch Characteristics
Candidate Switch and Cluster Member Switch Characteristics
Planning a Switch Cluster
Discovery Through CDP Hops
Automatic Discovery of Cluster Candidates and Members
Discovery Through CDP Hops
Discovery Through Different VLANs
Discovery Through Different VLANs
Discovery Through Different Management VLANs
Discovery Through Routed Ports
New out-of-box
Discovery of Newly Installed Switches
Hsrp and Standby Cluster Command Switches
Other Considerations for Cluster Standby Groups
Virtual IP Addresses
Automatic Recovery of Cluster Configuration
Hostnames
IP Addresses
Snmp Community Strings
Passwords
Switch Stack Switch Cluster
Switch Clusters and Switch Stacks
Members Other cluster member switches
LRE Profiles
TACACS+ and Radius
Switch# rcommand
Using the CLI to Manage Switch Clusters
Catalyst 1900 and Catalyst 2820 CLI Considerations
Snmp Management for a Cluster
Using Snmp to Manage Switch Clusters
OL-9775-02
Managing the System Time and Date
Administering the Switch
Understanding the System Clock
NTP
Understanding Network Time Protocol
Typical NTP Network Configuration
Configuring NTP
Configuring NTP Authentication
Default NTP Configuration
Ntp authenticate
Configuring NTP Associations
Switchconfig# ntp server 172.16.22.44 version
Configuring NTP Broadcast Service
Ntp peer ip-address version number
Key keyid source interface prefer
Ntp broadcast version number key keyid
Interface interface-id
Destination-address
Ntp broadcast client
Ntp broadcastdelay microseconds
Configuring NTP Access Restrictions
Ntp access-group query-only
Serve-onl y serve peer
Command Purpose
Interface interface-id
Configuring the Source IP Address for NTP Packets
Displaying the NTP Configuration
Configuring Time and Date Manually
Setting the System Clock
Fundamentals Command Reference, Release
Configuring the Time Zone
Displaying the Time and Date Configuration
Clock timezone zone hours-offset
Minutes-offset
Clock summer-time zone recurring
Configuring Summer Time Daylight Saving Time
Week day month hh mm week day month
Hh mm offset
Clock summer-time zone date month
Configuring a System Name and Prompt
Clock summer-time zone date date
Configuring a System Name
Default System Name and Prompt Configuration
Copy running-config startup-confi g
Understanding DNS
Setting Up DNS
Default DNS Configuration
Ip domain-name name
Ip name-server server-address1
Displaying the DNS Configuration
Default Banner Configuration
Creating a Banner
Banner motd c message c
Configuring a Message-of-the-Day Login Banner
Unix telnet
Banner login c message c
Configuring a Login Banner
Managing the MAC Address Table
MAC Addresses and VLANs
Building the Address Table
Default MAC Address Table Configuration
MAC Addresses and Switch Stacks
Changing the Address Aging Time
Removing Dynamic Address Entries
Configuring MAC Address Notification Traps
Mac address-table aging-time
Show mac address-table aging-time
Snmp-server enable traps mac-notification
String by using the snmp-server community
Snmp-server host host-addr traps informs version
Mac address-table notification
Adding and Removing Static Address Entries
Mac address-table static mac-addr
Configuring Unicast MAC Address Filtering
Vlan vlan-id interface interface-id
Show mac address-table static
Vlan vlan-id drop
Displaying Address Table Entries
Managing the ARP Table
OL-9775-02
Understanding the SDM Templates
Configuring SDM Templates
Dual IPv4 and IPv6 SDM Templates
Resource Access Default Routing
IPv4-and-IPv6 Resource Default Routing
SDM Templates and Switch Stacks
Default SDM Template
Configuring the Switch SDM Template
SDM Template Configuration Guidelines
Sdm prefer access default
Setting the SDM Template
Dual-ipv4-and-ipv6 default routing
Vlan routing vlan
Switchconfig# sdm prefer dual-ipv4-and-ipv6 default
Switchconfig# sdm prefer routing
Displaying the SDM Templates
Policy based routing aces 25K
OL-9775-02
Preventing Unauthorized Access to Your Switch
Configuring Switch-Based Authentication
Default Password and Privilege Level Configuration
Protecting Access to Privileged Exec Commands
Enable password password
Setting or Changing a Static Enable Password
Switchconfig# enable password l1u2c3k4y5
Encryption-type encrypted-password
Enable password level level password
Enable secret level level password
Service password-encryption
No service password-recovery
Disabling Password Recovery
Show version
Configuring Username and Password Pairs
Setting a Telnet Password for a Terminal Line
Password password
Switchconfig-line#password let45me67in89
Username command
Configuring Multiple Privilege Levels
Login local
Username name privilege level
Privilege mode level level command
Setting the Privilege Level for a Command
Show privilege
Command
Changing the Default Privilege Level for Lines
Logging into and Exiting a Privilege Level
Understanding TACACS+
Controlling Switch Access with TACACS+
Typical TACACS+ Network Configuration
TACACS+ Operation
Configuring TACACS+
Tacacs-server host hostname port
Default TACACS+ Configuration
Aaa new-model
Aaa group server tacacs+ group-name
Aaa new-model Enable AAA
Configuring TACACS+ Login Authentication
Show tacacs Verify your entries
Login authentication default
Aaa authentication login default
Authentication login command
Line console tty vty line-number
Show running-config Verify your entries
Displaying the TACACS+ Configuration
Controlling Switch Access with Radius
Starting TACACS+ Accounting
Understanding Radius
Radius Operation
Transitioning from Radius to TACACS+ Services
Default Radius Configuration
Configuring Radius
Identifying the Radius Server Host
Page
Radius-server host hostname
Acct-port port-number timeout
Ip-address auth-port port-number
Seconds retransmit retries key
Switchconfig# radius-server host host1
Configuring Radius Login Authentication
Server Host section on
Defining AAA Server Groups
Aaa group server radius group-name
Radius
Aaa authorization network radius
Starting Radius Accounting
Radius-server timeout seconds
Configuring Settings for All Radius Servers
Radius-server key string
Radius-server retransmit retries
Radius-server vsa send accounting
Authentication
Cisco-avpair=shellpriv-lvl=15
Cisco-avpair=ipoutacl#2=deny ip 10.10.10.10 0.0.255.255 any
Displaying the Radius Configuration
Controlling Switch Access with Kerberos
Radius-server host hostname ip-address non-standard
Understanding Kerberos
KDC
Term Definition
Kerberos Operation
Authenticating to a Boundary Switch
Keytab
Srvtab
Authenticating to Network Services
Configuring Kerberos
Obtaining a TGT from a KDC
Aaa authorization exec local
Aaa authentication login default local
Aaa authorization network local
Username command
Configuring the Switch for Secure Shell
Username name privilege level
SSH Servers, Integrated Clients, and Supported Versions
Understanding SSH
Configuration Guidelines
Configuring SSH
Limitations
Setting Up the Switch to Run SSH
Configuring the SSH Server
Displaying the SSH Configuration and Status
Ip ssh timeout seconds
Authentication-retries number
Understanding Secure Http Servers and Clients
Configuring the Switch for Secure Socket Layer Http
Certificate Authority Trustpoints
Rsakeypair TP-self-signed-3080755072
Default SSL Configuration
Configuring Secure Http Servers and Clients
CipherSuites
Configuring a CA Trustpoint
SSL Configuration Guidelines
Configuring the Secure Http Server
Ip http timeout-policy idle seconds life
Configuring the Secure Http Client
Show ip http server secure status
Ip http client secure-trustpoint name
Displaying Secure Http Server and Client Status
Configuring the Switch for Secure Copy Protocol
Ip http client secure-ciphersuite
Show ip http client secure status
Html
Information About Secure Copy
OL-9775-02
Understanding Ieee 802.1x Port-Based Authentication
Configuring Ieee 802.1x Port-Based Authentication
10-1
10-2
Device Roles
10-3
Authentication Process
10-4
Authentication Flowchart
10-5
Authentication Initiation and Message Exchange
EAPOL-Start
10-6
Ports in Authorized and Unauthorized States
Ieee 802.1x Authentication and Switch Stacks
10-7
10-8
Ieee 802.1x Host Mode
Ieee 802.1x Accounting Attribute-Value Pairs
Ieee 802.1x Accounting
Attribute Number AV Pair Name
10-9
10-10
Using Ieee 802.1x Authentication with Vlan Assignment
10-11
Using Ieee 802.1x Authentication with Per-User ACLs
10-12
Using Ieee 802.1x Authentication with Guest Vlan
10-13
Using Ieee 802.1x Authentication with Restricted Vlan
10-14
10-15
Using Ieee 802.1x Authentication with Voice Vlan Ports
10-16
Using Ieee 802.1x Authentication with Port Security
10-17
Using Ieee 802.1x Authentication with Wake-on-LAN
10-18
Network Admission Control Layer 2 Ieee 802.1x Validation
Using Multidomain Authentication
10-19
For example
Using Web Authentication
10-20
10-21
Configuring Ieee 802.1x Authentication
AAA
Default Ieee 802.1x Authentication Configuration
10-22
Ieee 802.1x Authentication
Ieee 802.1x Authentication Configuration Guidelines
10-23
10-24
MAC Authentication Bypass
Configuring Ieee 802.1x Authentication
10-25
10-26
Configuring the Switch-to-RADIUS-Server Communication
10-27
Ip-address auth-port port-number key
Dot1x host-mode multi-host
Configuring the Host Mode
Multi-domain
Show dot1x interface interface-id
Manually Re-Authenticating a Client Connected to a Port
Configuring Periodic Re-Authentication
10-29
Dot1x timeout tx-period seconds
Changing the Switch-to-Client Retransmission Time
Changing the Quiet Period
Show dot1x interface interface-id Verify your entries
Switchconfig-if#dot1x timeout tx-period
Setting the Switch-to-Client Frame-Retransmission Number
Show dot1xinterface interface-id Verify your entries
Dot1x max-reauth-req count
Configuring Ieee 802.1x Accounting
Setting the Re-Authentication Number
Switchconfig-if#dot1x max-reauth-req
10-32
10-33
Configuring a Guest Vlan
Switchport mode private-vlan host
Configuring a Restricted Vlan
Switchconfig# interface gigabitethernet2/0/2
Dot1x guest-vlan vlan-id
Dot1x auth-fail max-attempts max
Dot1x auth-fail vlan vlan-id
Attempts
10-35
Switchconfig-if#dot1x auth-fail max-attempts
Configuring the Inaccessible Authentication Bypass Feature
Radius-server dead-criteria time time
Tries tries
10-37
Dot1x critical recovery action
Configuring Ieee 802.1x Authentication with WoL
Reinitialize vlan vlan-id
Show dot1x interface interface-id
Switchconfig-if#dot1x control-direction both
Configuring MAC Authentication Bypass
Switchconfig-if#dot1x mac-auth-bypass
Dot1x control-direction both
10-40
Configuring NAC Layer 2 Ieee 802.1x Validation
10-41
Configuring Web Authentication
10-42
No dot1x pae Disable Ieee 802.1x authentication on the port
Disabling Ieee 802.1x Authentication on the Port
Dot1x fallback fallback-profile
10-43
10-44
Displaying Ieee 802.1x Statistics and Status
Understanding Interface Types
Configuring Interface Characteristics
11-1
Port-Based VLANs
Switch Ports
11-2
Trunk Ports
Access Ports
11-3
Tunnel Ports
Routed Ports
11-4
EtherChannel Port Groups
Switch Virtual Interfaces
11-5
Gigabit Ethernet Interfaces
Power over Ethernet Ports
Supported Protocols and Standards
11-6
Class
Powered-Device Detection and Initial Power Allocation
11-7
11-8
Power Management Modes
11-9
Power Monitoring and Power Policing
11-10
Maximum Power Allocation Cutoff Power on a PoE Port
11-11
Connecting Interfaces
11-12
Ethernet Management Port
11-13
Connecting a Switch Stack to a PC
11-14
Tftp
Mgmtinit
Using Interface Configuration Mode
Mgmtshow
Mgmtclr
11-16
Procedures for Configuring Interfaces
Interface range port-range macro
Configuring a Range of Interfaces
Macroname
Show interfaces interface-id
11-18
Show running-config include define
Configuring and Using Interface Range Macros
Define interface-range macroname
Interface range macro macroname
Switch# show running-config include define
Configuring Ethernet Interfaces
Switch# show run include define
11-20
11-21
Default Ethernet Interface Configuration
Speed and Duplex Configuration Guidelines
Configuring Interface Speed and Duplex Mode
11-22
Speed 10 100 1000 auto 10
Setting the Interface Speed and Duplex Parameters
Nonegotiate
Duplex auto full half
Flowcontrol receive on off desired
Configuring Ieee 802.3x Flow Control
11-24
Local Side Auto-MDIX
Configuring Auto-MDIX on an Interface
With Correct Cabling
11-25
Interface-id phy
Configuring a Power Management Mode on a PoE Port
11-26
Power inline auto max max-wattage
Budgeting Power for Devices Connected to a PoE Port
Show power inline i nterface-id
Neve r static max max-wattage
11-28
Wattage
11-29
Configuring Power Policing
11-30
Adding a Description for an Interface
Configuring Ethernet Management Ports
Configuring Layer 3 Interfaces
Switch# show interfaces gigabitethernet1/0/2 description
11-31
Interface gigabitethernet interface-id vlan vlan-id
No switchport
No shutdown
11-32
11-33
Configuring the System MTU
System mtu jumbo bytes
Use the system mtu jumbo Use the system mtu routing
System mtu routing bytes
11-34
System mtu bytes
Configuring the Cisco Redundant Power System
Reload
Show system mtu
Power rps switch-number port rps-port-id mode active
Power rps switch-number name string serialnumber
Standby
11-36
Power supply switch-numberoff on
Configuring the Power Supplies
Show env power
Show env rps
Monitoring Interface Status
Monitoring and Maintaining the Interfaces
11-38
11-39
Clearing and Resetting Interfaces and Counters
Interface vlan vlan-id gigabitethernet interface-id
Shutting Down and Restarting the Interface
Shutdown
11-40
Understanding Smartports Macros
Configuring Smartports Macros
12-1
Default Smartports Macro Configuration
Configuring Smartports Macros
Macro Name Description
12-2
12-3
Smartports Macro Configuration Guidelines
Macro name macro-name
Creating Smartports Macros
Name Sample-Macro and macro name sample-macro will result
Show parser macro name macro-name
12-5
Applying Smartports Macros
Show parser macro
Applying Cisco-Default Smartports Macros
Show parser macro macro-name
12-6
Switchconfig-if#macro apply cisco-desktop $AVID
Switch# show parser macro cisco-desktop
12-7
Show parser macro brief
Displaying Smartports Macros
Show parser macro description interface
12-8
Understanding VLANs
Configuring VLANs
13-1
13-2
Vlan Port Membership Modes
Supported VLANs
13-3
13-4
Configuring Normal-Range VLANs
13-5
Vlan ID
Token Ring VLANs
Normal-Range Vlan Configuration Guidelines
13-6
Saving Vlan Configuration
Vlan Configuration Mode Options
Vlan Configuration in config-vlan Mode
Vlan Configuration in Vlan Database Configuration Mode
Parameter Default Range
Default Ethernet Vlan Configuration
VLANxxxx, where
13-8
Creating or Modifying an Ethernet Vlan
Copy running-config startup config
Remote-span
13-9
Vlan database
Deleting a Vlan
13-10
Switchport access vlan vlan-id
Assigning Static-Access Ports to a Vlan
No vlan vlan-id
Show vlan brief
Default Vlan Configuration
Configuring Extended-Range VLANs
Show interfaces interface-id switchport
Vlan fields of the display
13-13
Extended-Range Vlan Configuration Guidelines
Creating an Extended-Range Vlan
Vtp mode transparent
Show vlan id vlan-id
13-14
Switch# copy running-config startup config
Switchconfig# vtp mode transparent
Creating an Extended-Range Vlan with an Internal Vlan ID
Show vlan internal usage
Command Command Mode Purpose
Configuring Vlan Trunks
Displaying VLANs
Trunking Overview
13-17
Switches in an ISL Trunking Environment
Encapsulation Types
Mode Function
Encapsulation Function
13-18
Configuring an Ethernet Interface as a Trunk Port
Default Layer 2 Ethernet Interface Vlan Configuration
Ieee 802.1Q Configuration Considerations
13-19
Configuring a Trunk Port
Interaction with Other Features
Dot1q negotiate
13-20
13-21
Defining the Allowed VLANs on a Trunk
Changing the Pruning-Eligible List
Switchport trunk allowed vlan add
All except remove vlan-list
13-22
Switchport trunk pruning vlan add
Configuring the Native Vlan for Untagged Traffic
Except none remove vlan-list
Vlan ,vlan
Load Sharing Using STP Port Priorities
Configuring Trunk Ports for Load Sharing
Switchport trunk native vlan vlan-id
13-24
13-25
Or switch stack
Load Sharing Using STP Path Cost
Connect to the trunk ports configured on Switch a
Exit Return to global configuration mode
Interface gigabitethernet1/0/1
Switchport trunk encapsulation
Isl dot1q negotiate
Spanning-tree vlan 2-4 cost
Understanding Vmps
Configuring Vmps
13-28
Vmps Configuration Guidelines
Default Vmps Client Configuration
Dynamic-Access Port Vlan Membership
13-29
Entering the IP Address of the Vmps
Configuring the Vmps Client
13-30
Switchport access vlan dynamic
Configuring Dynamic-Access Ports on Vmps Clients
Reconfirming Vlan Memberships
Vmps reconfirm
Changing the Retry Count
Changing the Reconfirmation Interval
Vmps reconfirm minutes
13-32
Vmps Configuration Example
Troubleshooting Dynamic-Access Port Vlan Membership
Switch# show vmps
Monitoring the Vmps
13-34
Dynamic Port Vlan Membership Configuration
Understanding VTP
Configuring VTP
14-1
14-2
VTP Domain
VTP Modes
VTP Mode Description
VTP Advertisements
14-3
VTP Pruning
VTP Version
14-4
Vlan
14-5
VTP and Switch Stacks
Configuring VTP
14-6
VTP Configuration Options
Default VTP Configuration
VTP Configuration in Global Configuration Mode
14-7
VTP Configuration in Vlan Database Configuration Mode
VTP Configuration Guidelines
Passwords
Domain Names
Configuration Requirements
Configuring a VTP Server
VTP Version
14-9
Vtp password password
Vtp password password
Show vtp status
Vtp server
Vtp mode client
Configuring a VTP Client
Switch# vlan database
14-11
14-12
Disabling VTP VTP Transparent Mode
Vtp version
Enabling VTP Version
14-13
Enabling VTP Pruning
Adding a VTP Client Switch to a VTP Domain
Vtp pruning
14-14
14-15
14-16
Monitoring VTP
Understanding Voice Vlan
Configuring Voice Vlan
15-1
Cisco IP Phone Data Traffic
Cisco IP Phone Voice Traffic
15-2
Default Voice Vlan Configuration
Configuring Voice Vlan
Voice Vlan Configuration Guidelines
15-3
15-4
Configuring a Port Connected to a Cisco 7960 IP Phone
15-5
Configuring Cisco IP Phone Voice Traffic
15-6
Configuring the Priority of Incoming Data Frames
15-7
Displaying Voice Vlan
15-8
Understanding Private VLANs
Configuring Private VLANs
16-1
Private-VLAN Domain
16-2
16-3
IP Addressing Scheme with Private VLANs
Private-VLAN Interaction with Other Features
Private VLANs across Multiple Switches
16-4
Private VLANs and SVIs
Private VLANs and Unicast, Broadcast, and Multicast Traffic
16-5
Tasks for Configuring Private VLANs
Configuring Private VLANs
Private VLANs and Switch Stacks
16-6
Private-VLAN Configuration Guidelines
Default Private-VLAN Configuration
Secondary and Primary Vlan Configuration
16-7
16-8
Private-VLAN Port Configuration
16-9
Limitations with Other Features
16-10
Configuring and Associating VLANs in a Private Vlan
Show interfaces status
Show vlan private-vlan type
16-11
Switchport private-vlan host-association
Configuring a Layer 2 Interface as a Private-VLAN Host Port
Switch# show interfaces gigabitethernet1/0/22 switchport
Primaryvlanid secondaryvlanid
Switchport private-vlan mapping primaryvlanid
Switchport mode private-vlan promiscuous
Add remove secondaryvlanlist
16-13
Interface vlan primaryvlanid
Switch# show interfaces private-vlan mapping
Private-vlan mapping add remove
Show interface private-vlan mapping
16-15
Monitoring Private VLANs
16-16
Understanding Ieee 802.1Q Tunneling
Configuring Ieee 802.1Q and Layer 2 Protocol Tunneling
17-1
17-2
Ieee 802.1Q Tunnel Ports in a Service-Provider Network
17-3
Default Ieee 802.1Q Tunneling Configuration
Configuring Ieee 802.1Q Tunneling
Ieee 802.1Q Tunneling Configuration Guidelines
Native VLANs
17-5
System MTU
17-6
Ieee 802.1Q Tunneling and Other Features
Vlan dot1q tag native
Configuring an Ieee 802.1Q Tunneling Port
Show dot1q-tunnel
Show vlan dot1q tag native
17-8
Understanding Layer 2 Protocol Tunneling
Layer 2 Protocol Tunneling
17-9
17-10
Configuring Layer 2 Protocol Tunneling
17-11
Default Layer 2 Protocol Tunneling Configuration
17-12
Layer 2 Protocol Tunneling Configuration Guidelines
17-13
Configuring Layer 2 Protocol Tunneling
Configuring the SP Edge Switch
Configuring Layer 2 Tunneling for EtherChannels
L2protocol-tunnel point-to-point
Pagp lacp udld
17-15
17-16
Configuring the Customer Switch
Switchconfig# interface port-channel
Switchconfig-if#channel-group 1 mode desirable
17-17
17-18
Monitoring and Maintaining Tunneling Status
Understanding Spanning-Tree Features
Configuring STP
18-1
18-2
STP Overview
18-3
Spanning-Tree Topology and BPDUs
18-4
Bridge ID, Switch Priority, and Extended System ID
Spanning-Tree Interface States
Switch Priority Value
Bit
32768 16384 8192 4096 2048 1024 512 256 128
18-6
2illustrates how an interface moves through the states
Listening State
Blocking State
Learning State
Forwarding State
Disabled State
How a Switch or Port Becomes the Root Switch or Root Port
18-8
Spanning-Tree Address Management
Spanning Tree and Redundant Connectivity
Accelerated Aging to Retain Connectivity
18-9
Supported Spanning-Tree Instances
Spanning-Tree Modes and Protocols
18-10
STP and Ieee 802.1Q Trunks
Spanning-Tree Interoperability and Backward Compatibility
VLAN-Bridge Spanning Tree
Rapid PVST+
Spanning Tree and Switch Stacks
Configuring Spanning-Tree Features
18-12
Spanning-Tree Configuration Guidelines
Default Spanning-Tree Configuration
18-13
18-14
18-15
Changing the Spanning-Tree Mode
Disabling Spanning Tree
Configuring the Root Switch
Show spanning-tree vlan vlan-id Verify your entries
18-16
Diameter net-diameter hello-time seconds
Spanning-tree vlan vlan-id root primary
Show spanning-tree detail
18-17
Configuring Port Priority
Configuring a Secondary Root Switch
Spanning-tree vlan vlan-id root secondary
Diameter net-diameter hello-time
Spanning-tree vlan vlan-id port-priority priority
Spanning-tree port-priority priority
Show spanning-tree interface interface-id
Show spanning-tree vlan vlan-id
Port-channel-number
Configuring Path Cost
Spanning-tree cost cost
Spanning-tree vlan vlan-id cost cost
Spanning-tree vlan vlan-id priority priority
Configuring the Switch Priority of a Vlan
18-21
Configuring the Hello Time
Configuring Spanning-Tree Timers
Spanning-tree vlan vlan-id hello-time seconds
18-22
Configuring the Maximum-Aging Time for a Vlan
Configuring the Forwarding-Delay Time for a Vlan
Spanning-tree vlan vlan-id forward-time
Spanning-tree vlan vlan-idmax-age seconds
Displaying the Spanning-Tree Status
Configuring the Transmit Hold-Count
Show spanning-tree detail Verify your entries
18-24
19-1
Configuring Mstp
Multiple Spanning-Tree Regions
Understanding Mstp
19-2
Operations Within an MST Region
IST, CIST, and CST
19-3
19-4
Operations Between MST Regions
Ieee 802.1s Terminology
Hop Count
Cisco Prestandard Cisco Standard
19-5
Ieee 802.1s Implementation
Boundary Ports
19-6
Port Role Naming Change
Interoperation Between Legacy and Standard Switches
19-7
Detecting Unidirectional Link Failure
Mstp and Switch Stacks
19-8
Interoperability with Ieee 802.1D STP
Understanding Rstp
Port Roles and the Active Topology
19-9
19-10
Rapid Convergence
19-11
Synchronization of Port Roles
Bit Function
Bridge Protocol Data Unit Format and Processing
19-12
Processing Superior Bpdu Information
Topology Changes
Processing Inferior Bpdu Information
19-13
19-14
Configuring Mstp Features
Mstp Configuration Guidelines
Default Mstp Configuration
19-15
Spanning-tree mst configuration
Specifying the MST Region Configuration and Enabling Mstp
Instance instance-id vlan vlan-range
Name name
Revision version
Spanning-tree mode mst
Show pending
Exit
19-18
Spanning-tree mst instance-id root primary
19-19
Show spanning-tree mst interface interface-id
Spanning-tree mst instance-id port-priority priority
19-20
19-21
Spanning-tree mst instance-id cost cost
Configuring the Hello Time
Configuring the Switch Priority
Spanning-tree mst instance-id priority priority
19-22
Show spanning-tree mst Verify your entries
Configuring the Forwarding-Delay Time
Spanning-tree mst forward-time seconds
Show spanning-tree mst
Configuring the Maximum-Hop Count
Configuring the Maximum-Aging Time
Specifying the Link Type to Ensure Rapid Transitions
Spanning-tree mst max-age seconds
19-25
Designating the Neighbor Type
Restarting the Protocol Migration Process
Displaying the MST Configuration and Status
19-26
Understanding Optional Spanning-Tree Features
Configuring Optional Spanning-Tree Features
20-1
Understanding Bpdu Guard
Understanding Port Fast
20-2
Understanding UplinkFast
Understanding Bpdu Filtering
20-3
20-4
Switches in a Hierarchical Network
20-5
Understanding Cross-Stack UplinkFast
20-6
How Csuf Works
Events that Cause Fast Convergence
Understanding BackboneFast
20-7
BackboneFast Example Before Indirect Link Failure
20-8
20-9
Adding a Switch in a Shared-Medium Topology
Understanding Root Guard
Understanding EtherChannel Guard
20-10
20-11
Understanding Loop Guard
Optional Spanning-Tree Configuration Guidelines
Default Optional Spanning-Tree Configuration
Enabling Port Fast
20-12
Enabling Bpdu Guard
Spanning-tree portfast trunk interface configuration
Spanning-tree portfast trunk
Portfast
Enabling Bpdu Filtering
Spanning-tree portfast Enable the Port Fast feature
20-14
20-15
Enabling UplinkFast for Use with Redundant Links
Uplinkfast command
Spanning-tree uplinkfast max-update-rate
Enabling Cross-Stack UplinkFast
Enabling BackboneFast
Enabling EtherChannel Guard
Spanning-tree backbonefast Enable BackboneFast
Show spanning-tree summary Verify your entries
20-17
Enabling Loop Guard
Enabling Root Guard
20-18
20-19
20-20
21-1
Flex Links
Vlan Flex Link Load Balancing and Support
Switchport backup interface preemption delay commands
21-2
21-3
MAC Address-Table Move Update
21-4
MAC Address-Table Move Update Example
Default Configuration
Configuration Guidelines
21-5
Switchport backup interface interface-id
Configuring Flex Links
Show interface interface-id switchport backup
Switch# show interface switchport backup
Mode forced bandwidth off
Switchport backup interface interface-id preemption
Delay delay-time
21-7
Switchport backup interface interface-id prefer vlan
Configuring Vlan Load Balancing on Flex Links
Show interfaces interface-id switchport backup
Switch#show interfaces switchport backup
Switchport backup interface interface-idmmu
Configuring the MAC Address-Table Move Update Feature
Primary vlan vlan-id
21-9
Switchconf# mac address-table move update transmit
End Return to global configuration mode
Switch# show mac-address-table move update
21-10
21-11
Monitoring Flex Links and the MAC Address-Table Move Update
21-12
Understanding Dhcp Features
Configuring Dhcp Features and IP Source Guard
22-1
Dhcp Relay Agent
Dhcp Server
Dhcp Snooping
22-2
22-3
Option-82 Data Insertion
Dhcp Relay Agent in a Metropolitan Ethernet Network
22-4
22-5
Remote ID Suboption Frame Format
Dhcp Snooping Binding Database
Cisco IOS Dhcp Server Database
Release
22-6
22-7
Dhcp Snooping and Switch Stacks
Configuring Dhcp Features
Default Dhcp Configuration
22-8
22-9
Dhcp Snooping Configuration Guidelines
Dhcp Server and Switch Stacks
Configuring the Dhcp Server
22-10
Specifying the Packet Forwarding Address
Configuring the Dhcp Relay Agent
Ip helper-address address
22-11
Switchport access vlan vlan-id
Switchport mode access
Enabling Dhcp Snooping and Option
Interface range port-range
22-13
Enabling the Cisco IOS Dhcp Server Database
Enabling Dhcp Snooping on Private VLANs
Enabling the Dhcp Snooping Binding Database Agent
Ip dhcp snooping database
22-15
Displaying Dhcp Snooping Information
Source IP Address Filtering
Understanding IP Source Guard
22-16
Default IP Source Guard Configuration
Configuring IP Source Guard
IP Source Guard Configuration Guidelines
Source IP and MAC Address Filtering
22-18
Enabling IP Source Guard
22-19
Displaying IP Source Guard Information
22-20
Understanding Dynamic ARP Inspection
Configuring Dynamic ARP Inspection
23-1
ARP Cache Poisoning
23-2
23-3
Interface Trust States and Network Security
Relative Priority of ARP ACLs and Dhcp Snooping Entries
Rate Limiting of ARP Packets
23-4
Default Dynamic ARP Inspection Configuration
Configuring Dynamic ARP Inspection
Logging of Dropped Packets
23-5
23-6
Dynamic ARP Inspection Configuration Guidelines
Show cdp neighbors
Configuring Dynamic ARP Inspection in Dhcp Environments
Ip arp inspection vlan vlan-range
23-7
23-8
Configuring ARP ACLs for Non-DHCP Environments
23-9
Limiting the Rate of Incoming ARP Packets
Show arp access-list acl-name
No ip arp inspection trust
Specified with the ip arp inspection vlan logging
23-11
Performing Validation Checks
Ip arp inspection validate
Configuring the Log Buffer
Src-mac dst-mac ip
Show ip arp inspection vlan
Number logs number interval
Ip arp inspection log-buffer entries
23-13
23-14
Displaying Dynamic ARP Inspection Information
Show ip arp inspection statistics vlan
Clear ip arp inspection statistics
Clear ip arp inspection log
Show ip arp inspection log
23-16
24-1
Configuring Igmp Snooping and MVR
24-2
Understanding Igmp Snooping
Joining a Multicast Group
Igmp Versions
24-3
24-4
224.1.2.3
24-5
Leaving a Multicast Group
Immediate Leave
Igmp Configurable-Leave Timer
Igmp Report Suppression
24-6
Igmp Snooping and Switch Stacks
Configuring Igmp Snooping
Default Igmp Snooping Configuration
PIM-DVMRP
Ip igmp snooping vlan vlan-id
Enabling or Disabling Igmp Snooping
24-8
Ip igmp snooping vlan vlan-id mrouter
Setting the Snooping Method
Learn cgmp pim-dvmrp
Show ip igmp snooping
Show ip igmp snooping mrouter vlan vlan-id
Configuring a Multicast Router Port
24-10
Enabling Igmp Immediate Leave
Configuring a Host Statically to Join a Group
Ip igmp snooping vlan vlan-id static ipaddress
Show ip igmp snooping groups
24-12
Configuring the Igmp Leave Timer
Recovering from Flood Mode
Configuring TCN-Related Commands
Controlling the Multicast Flooding Time After a TCN Event
Count
No ip igmp snooping tcn flood
Disabling Multicast Flooding During a TCN Event
24-14
24-15
Configuring the Igmp Snooping Querier
No ip igmp snooping report-suppression
Disabling Igmp Report Suppression
24-16
24-17
Displaying Igmp Snooping Information
24-18
Understanding Multicast Vlan Registration
24-19
Using MVR in a Multicast Television Application
Default MVR Configuration
Configuring MVR
MVR
24-20
Configuring MVR Global Parameters
MVR Configuration Guidelines and Limitations
Mvr Enable MVR on the switch
24-21
24-22
Configuring MVR Interfaces
Mvr immediate
Mvr type source receiver
Show mvr
Show mvr interface Show mvr members
Displaying MVR Information
Configuring Igmp Filtering and Throttling
24-24
Configuring Igmp Profiles
Default Igmp Filtering and Throttling Configuration
24-25
Permit deny
Ip igmp profile profile number
Range ip multicast address
Show ip igmp profile profile number
Switch# show ip igmp profile
Setting the Maximum Number of Igmp Groups
Applying Igmp Profiles
Ip igmp filter profile number
Show running-config interface Verify the configuration
Configuring the Igmp Throttling Action
EtherChannel group or a EtherChannel interface
Interface-id
Ip igmp max-groups action deny
Displaying Igmp Filtering and Throttling Configuration
Replace
Show ip igmp profile profile
24-30
Understanding MLD Snooping
Configuring IPv6 MLD Snooping
25-1
25-2
MLD Queries
MLD Messages
Multicast Client Aging Robustness
25-3
MLD Reports
Multicast Router Discovery
MLD Done Messages and Immediate-Leave
25-4
MLD Snooping in Switch Stacks
Configuring IPv6 MLD Snooping
Topology Change Notification Processing
25-5
MLD Snooping Configuration Guidelines
Default MLD Snooping Configuration
25-6
Ipv6 mld snooping
Enabling or Disabling MLD Snooping
Ipv6 mld snooping vlan vlan-id
25-7
Ipv6 mld snooping vlan vlan-id static
Configuring a Static Multicast Group
Show ipv6 mld snooping multicast-address user
Show ipv6 mld snooping multicast-address vlan
Ipv6 mld snooping vlan vlan-id mrouter
Enabling MLD Immediate Leave
Show ipv6 mld snooping mrouter vlan vlan-id
25-9
25-10
Configuring MLD Snooping Queries
Disabling MLD Listener Message Suppression
Displaying MLD Snooping Information
25-11
Vlan-id count dynamic user
Show ipv6 mld snooping querier vlan vlan-id
Vlan-id ipv6-multicast-address
25-12
Configuring Storm Control
Configuring Port-Based Traffic Control
Understanding Storm Control
26-1
Broadcast Storm Control Example
26-2
Configuring Storm Control and Threshold Levels
Default Storm Control Configuration
26-3
Unicast level level level-low bps bps
Storm-control broadcast multicast
Bps-low pps pps pps-low
Storm-control action shutdown trap
Default Protected Port Configuration
Configuring Protected Ports
Show storm-control interface-id broadcast
Multicast unicast
Protected Port Configuration Guidelines
Configuring Port Blocking
Configuring a Protected Port
26-6
Default Port Blocking Configuration
Configuring Port Security
Blocking Flooded Traffic on an Interface
26-7
Secure MAC Addresses
Understanding Port Security
26-8
26-9
Security Violations
Port Security Configuration Guidelines
Default Port Security Configuration
Forwarded1 Trap Message Message2 Increments
26-10
26-11
26-12
Enabling and Configuring Port Security
Protect restrict shutdown
Switchport port-security violation
Shutdown vlan
26-13
26-14
Switchconfig-if#switchport port-security maximum
Switchconfig-if#switchport port-security
Switchconfig-if#switchport port-security mac-address sticky
Switchconfig-if#switchport port-security violation restrict
26-16
Enabling and Configuring Port Security Aging
Switchconfig# interface GigabitEthernet 1/0/8
Port Security and Switch Stacks
Port Security and Private VLANs
26-17
Show port-security interface interface-idaddress
Displaying Port-Based Traffic Control Settings
Show port-security interface interface-idvlan
26-18
Understanding CDP
Configuring CDP
27-1
CDP and Switch Stacks
Configuring CDP
Default CDP Configuration
Configuring the CDP Characteristics
Cdp holdtime seconds
Disabling and Enabling CDP
Cdp advertise-v2
Show cdp
Cdp enable Enable CDP on the interface after disabling it
No cdp enable Disable CDP on the interface
Disabling and Enabling CDP on an Interface
27-4
27-5
Monitoring and Maintaining CDP
27-6
Understanding Lldp and LLDP-MED
Configuring Lldp and LLDP-MED
Understanding Lldp
28-1
28-2
Understanding LLDP-MED
Default Lldp Configuration
Configuring Lldp and LLDP-MED
Configuring Lldp Characteristics
28-3
28-4
Disabling and Enabling Lldp Globally
28-5
Disabling and Enabling Lldp on an Interface
TLV, and enter interface configuration mode
Configuring LLDP-MED TLVs
No lldp med-tlv-select tlv Specify the TLV to disable
Lldp med-tlv-select tlv Specify the TLV to enable
28-7
Monitoring and Maintaining Lldp and LLDP-MED
28-8
Understanding Udld
Configuring Udld
Modes of Operation
29-1
29-2
Methods to Detect Unidirectional Links
29-3
Configuring Udld
29-4
Default Udld Configuration
Message-timer-interval
Udld aggressive enable message time
Enabling Udld Globally
Show udld
Udld reset Show udld
Resetting an Interface Disabled by Udld
Enabling Udld on an Interface
Udld port aggressive
29-7
Displaying Udld Status
29-8
Understanding Span and Rspan
Configuring Span and Rspan
30-1
30-2
Local Span
30-3
Remote Span
Span Sessions
Span and Rspan Concepts and Terminology
30-4
30-5
Monitored Traffic
30-6
Source Ports
Vlan Filtering
Source VLANs
30-7
30-8
Destination Port
Rspan Vlan
Span and Rspan Interaction with Other Features
30-9
Span and Rspan and Switch Stacks
Configuring Span and Rspan
30-10
Configuring Local Span
Default Span and Rspan Configuration
Span Configuration Guidelines
30-11
30-12
Creating a Local Span Session
Destination interface interface-id
Monitor session sessionnumber
Encapsulation replicate
Show monitor session sessionnumber
30-14
Monitor session sessionnumber filter vlan
Specifying VLANs to Filter
30-15
Rspan Configuration Guidelines
Configuring Rspan
Be a Vlan
30-16
30-17
Configuring a Vlan as an Rspan Vlan
Interfaces port-channelport-channel-number. Valid
Creating an Rspan Source Session
Destination remote vlan vlan-id
30-18
Remote vlan vlan-id
Creating an Rspan Destination Session
30-19
30-20
Untagged vlan vlan-id or vlan vlan-id- Forward incoming
Ingress dot1q vlan vlan-id isl untagged
30-21
30-22
Show monitor session sessionnumber
30-23
Displaying Span and Rspan Status
30-24
Understanding Rmon
Configuring Rmon
31-1
31-2
Configuring Rmon
Configuring Rmon Alarms and Events
Default Rmon Configuration
31-3
Add an event in the Rmon event table that is
Rmon event number description string log owner string
31-4
Collecting Group Ethernet Statistics on an Interface
Collecting Group History Statistics on an Interface
Rmon collection history index
Show rmon history
Rmon collection stats index owner ownername
Displaying Rmon Status
Show rmon statistics
31-6
Understanding System Message Logging
Configuring System Message Logging
32-1
System Log Message Format
Configuring System Message Logging
32-2
Text string that uniquely describes the message
Hhmmss short uptime
32-3
No logging console Disable message logging
Default System Message Logging Configuration
Show running-config Verify your entries Show logging
Disabling Message Logging
Logging buffered size
Setting the Message Display Destination Device
Logging host
32-5
Logging file flash filename
Synchronizing Log Messages
Terminal monitor
Session to see the debugging messages
Line vty
Line console vty line-number
Logging synchronous level severity-level
All limit number-of-buffers
Enabling and Disabling Sequence Numbers in Log Messages
Enabling and Disabling Time Stamps on Log Messages
32-8
Logging console level
Defining the Message Severity Level
Logging monitor level
Logging trap level
32-10
Level Description Syslog Definition
Logging history level
Enabling the Configuration-Change Logger
Logging history size number
32-11
Logging Messages to a Unix Syslog Daemon
Configuring Unix Syslog Servers
32-12
Logging facility facility-type
Configuring the Unix System Logging Facility
Facility-type keywords
32-13
Facility Type Keyword Description
Displaying the Logging Configuration
32-14
Understanding Snmp
Configuring Snmp
33-1
33-2
Snmp Versions
Snmp Manager Functions
Model Level Authentication Encryption Result
DES
Operation Description
Snmp Agent Functions
Using Snmp to Access MIB Variables
33-4
33-5
Snmp Notifications
Snmp ifIndex MIB Object Values
Configuring Snmp
IfIndex Range
SVI
Snmp Configuration Guidelines
Default Snmp Configuration
33-7
No snmp-server Disable the Snmp agent operation
Configuring Community Strings
Disabling the Snmp Agent
33-8
Access-list access-list-number deny
View-name ro rw access-list-number
Snmp-server community string view
Permit source source-wildcard
Snmp-server engineID local engineid-string
Configuring Snmp Groups and Users
Snmp-server engineID local
33-10
Snmp-server group groupname v1 v2c
Write writeview notify notifyview access
Auth noauth priv read readview
33-11
Remote host udp-port port v1 access
Configuring Snmp Notifications
Encrypted access access-list auth md5
Notification Type Keyword Description
33-13
33-14
33-12 , or enter snmp-server enable traps ?
Setting the Agent Contact and Location Information
Enable traps command for each trap type
Notification-types
Limiting Tftp Servers Used Through Snmp
Switchconfig# snmp-server community public
Snmp Examples
Snmp-server tftp-server-list
33-17
Displaying Snmp Status
33-18
Understanding ACLs
Configuring Network Security with ACLs
34-1
34-2
Supported ACLs
34-3
Port ACLs
34-4
Router ACLs
Vlan Maps
Handling Fragmented and Unfragmented Traffic
34-5
34-6
ACLs and Switch Stacks
34-7
Configuring IPv4 ACLs
Access List Number Type Supported
Access List Numbers
Creating Standard and Extended IPv4 ACLs
34-8
34-9
ACL Logging
Show access-lists number name
Access-list access-list-number deny permit
Creating a Numbered Standard ACL
Source source-wildcard log
34-11
Creating a Numbered Extended ACL
34-12
34-13
34-14
Creating Named Standard and Extended ACLs
Resequencing ACEs in an ACL
34-15
Ip access-list extended name
Ip access-list standard name
Any log
Tos tos established log time-range
34-17
Using Time Ranges with ACLs
Periodic weekdays weekend daily
Absolute start time date
Show time-range
34-18
Applying an IPv4 ACL to a Terminal Line
Switch# show ip access-lists
Including Comments in ACLs
34-19
Applying an IPv4 ACL to an Interface
Access-class access-list-number
Out
34-20
34-21
Ip access-group access-list-number
Hardware and Software Treatment of IP ACLs
IPv4 ACL Configuration Examples
34-22
Switchconfig# access-list 106 permit ip any 172.20.128.64
Switchconfig# access-list 6 permit 172.20.128.64
34-23
Extended ACLs
Numbered ACLs
34-24
Time Range Applied to an IP ACL
Named ACLs
Commented IP ACL Entries
34-25
Switchconfig-if#ip access-group ext1
Switch# show logging
34-26
34-27
Creating Named MAC Extended ACLs
34-28
Applying a MAC ACL to a Layer 2 Interface
Mac access-group name
Configuring Vlan Maps
Show mac access-group interface interface-id
ACL
34-30
Vlan Map Configuration Guidelines
Creating a Vlan Map
Vlan access-map name number
Action drop forward
Match ip mac address name
34-32
Examples of ACLs and Vlan Maps
34-33
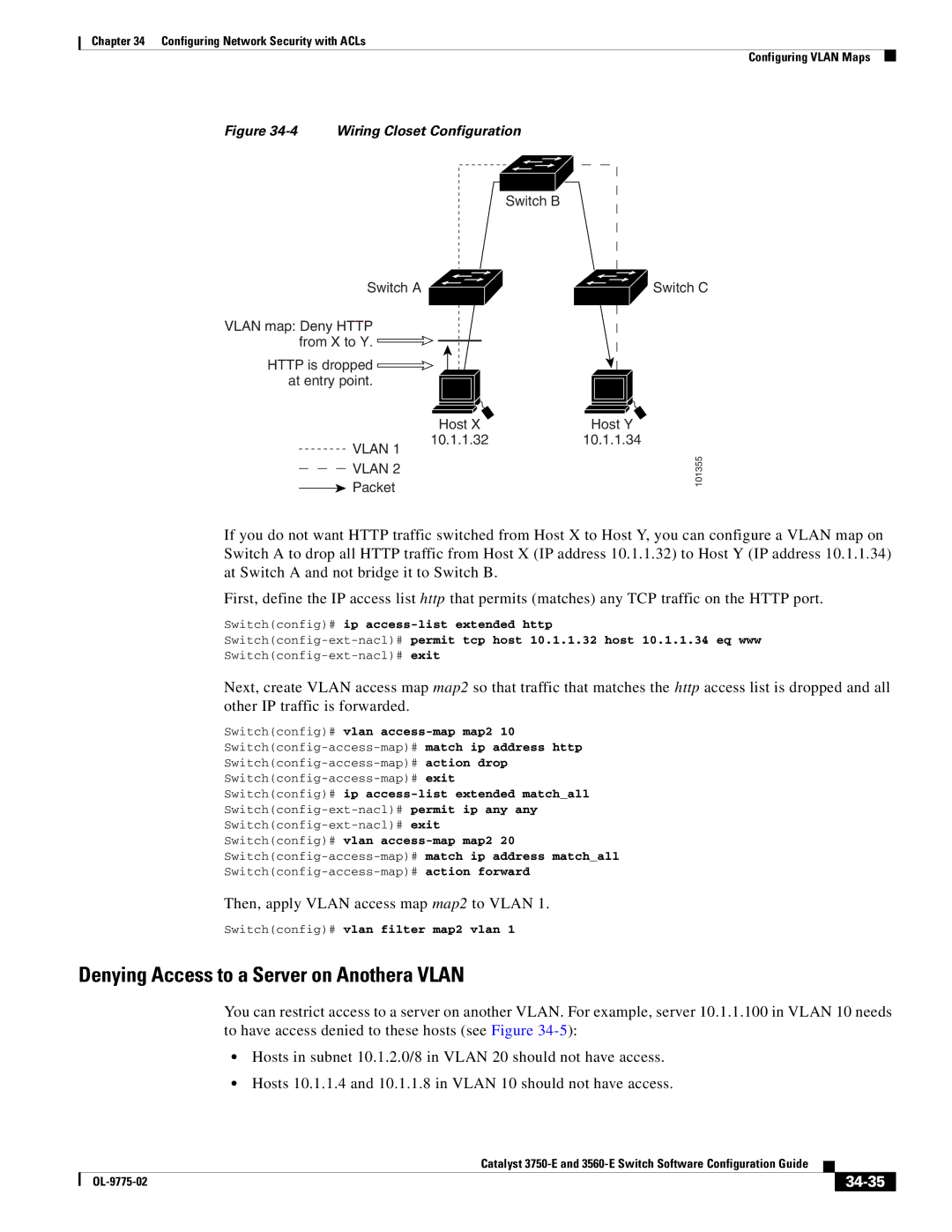
Wiring Closet Configuration
Using Vlan Maps in Your Network
Applying a Vlan Map to a Vlan
Vlan filter mapname vlan-list list
Switchconfig# vlan access-map map2
Denying Access to a Server on Anothera Vlan
Switchconfig# ip access-list extended matchall
Switchconfig# vlan filter map2 vlan
34-36
Using Vlan Maps with Router ACLs
34-37
Vlan Maps and Router ACL Configuration Guidelines
Examples of Router ACLs and Vlan Maps Applied to VLANs
ACLs and Switched Packets
ACLs and Bridged Packets
34-38
34-39
ACLs and Routed Packets
Show ip access-lists number name
Displaying IPv4 ACL Configuration
ACLs and Multicast Packets
34-40
Show mac access-group interface interface-id
Show running-config interface interface-id
Show ip interface interface-id
34-41
34-42
35-1
Configuring IPv6 ACLs
35-2
Understanding IPv6 ACLs
IPv6 ACLs and Switch Stacks
Supported ACL Features
IPv6 ACL Limitations
35-3
Default IPv6 ACL Configuration
Configuring IPv6 ACLs
Interaction with Other Features and Switches
35-4
Creating IPv6 ACLs
Ipv6 access-list access-list-name
35-5
Log-input routing sequence
Dscp value fragments log
Value time-range name
35-6
35-7
Applying an IPv6 ACL to an Interface
Ipv6 traffic-filter access-list-name
Ipv6 address ipv6-address
35-8
Show ipv6 access-list access-list-name
Show access-lists
Displaying IPv6 ACLs
35-9
35-10
36-1
Configuring QoS
36-2
Understanding QoS
36-3
Basic QoS Model
Basic QoS Model
36-4
36-5
Classification
Check if packet came with CoS label tag Yes
36-6
Classification Based on Class Maps and Policy Maps
Classification Based on QoS ACLs
36-7
36-8
Policing and Marking
36-9
Policing on Physical Ports
36-10
Policing on SVIs
36-11
Policing and Marking Flowchart on SVIs
36-12
Mapping Tables
36-13
Queueing and Scheduling Overview
SRR Shaping and Sharing
Weighted Tail Drop
36-14
36-15
Queueing and Scheduling on Ingress Queues
36-16
Queue Type Function
36-17
WTD Thresholds
36-18
Queueing and Scheduling on Egress Queues
36-19
36-20
Buffer and Memory Allocation
36-21
Packet Modification
36-22
Configuring Auto-QoS
36-23
Generated Auto-QoS Configuration
36-24
Description Automatically Generated Command
36-25
Sizes. It configures the bandwidth and the SRR mode shaped
Switch automatically configures the egress queue buffer
If you entered the auto qos voip trust command, the switch
Or shared on the egress queues mapped to the port
Auto-QoS Configuration Guidelines
Effects of Auto-QoS on the Configuration
36-27
Auto qos voip cisco-phone
Enabling Auto-QoS for VoIP
Cisco-softphone trust
Show auto qos interface interface-id
36-29
36-30
Auto-QoS Configuration Example
Debug auto qos
Cdp enable
Auto qos voip trust
Show auto qos
Displaying Auto-QoS Information
Configuring Standard QoS
36-32
Default Ingress Queue Configuration
Default Standard QoS Configuration
36-33
Dscp Value Queue ID -Threshold ID
Default Egress Queue Configuration
36-34
Default Mapping Table Configuration
Standard QoS Configuration Guidelines
QoS ACL Guidelines
Applying QoS on Interfaces
General QoS Guidelines
Policing Guidelines
36-36
Enabling VLAN-Based QoS on Physical Ports
Enabling QoS Globally
36-37
Configuring the Trust State on Ports within the QoS Domain
Configuring Classification Using Port Trust States
36-38
15 Port Trusted States within the QoS Domain
36-39
Mls qos trust cos dscp ip-precedence
Configuring the CoS Value for an Interface
Show mls qos interface
36-40
Mls qos cos default-cos override
Configuring a Trusted Boundary to Ensure Port Security
36-41
Mls qos trust dscp
Enabling Dscp Transparency Mode
Mls qos trust device cisco-phone
36-42
36-43
No mls qos rewrite ip dscp
Mls qos dscp-mutation
Mls qos map dscp-mutation
Show mls qos maps dscp-mutation
36-44
Switchconfig-if#mls qos dscp-mutation gi1/0/2-mutation
Configuring a QoS Policy
36-45
36-46
Classifying Traffic by Using ACLs
Switchconfig# access-list 102 permit pim any 224.0.0.2 dscp
Switchconfig# access-list 100 permit ip any any dscp
Permit protocol source source-wildcard
Source-wildcard
36-48
Mac access-list extended name
Class-map match-all match-any
Classifying Traffic by Using Class Maps
Is match-all
Match-any keywords
Ip dscp dscp-list ip precedence
Match access-group acl-index-or-name
Ip-precedence-list
Show class-map
36-51
Class class-map-name
Policy-map policy-map-name
36-52
36-53
Show policy-map policy-map-nameclass
Service-policy input policy-map-name
36-54
Switchconfig-pmap#class macclass2 maclist2
Switchconfig# policy-map macpolicy1
Switchconfig-if#service-policy input macpolicy1
36-55
36-56
Traffic by Using Class Maps section on
36-57
Drop policed-dscp-transmit
Police rate-bps burst-byte exceed-action
Exceed-action policed-dscp-transmit keywords to mark down
36-58
36-59
Service-policy policy-map-name
Show policy-map policy-map-nameclass
Service-policy input policy-map-name
Show mls qos vlan-based
Aggregate-policer-name rate-bps burst-byte
Mls qos aggregate-policer
Exceed-action drop
Policed-dscp-transmit
Show mls qos aggregate-policer
Only one policy map per ingress port is supported
Aggregate-policer-name
Configuring the CoS-to-DSCP Map
Configuring Dscp Maps
Switchconfig-pmap-c#police aggregate transmit1
CoS Value Dscp Value
Mls qos map cos-dscp dscp1...dscp8
Configuring the IP-Precedence-to-DSCP Map
IP Precedence Value Dscp Value
36-64
36-65
Configuring the Policed-DSCP Map
Dscp Value CoS Value
Configuring the DSCP-to-CoS Map
36-66
Show
Mls qos map dscp-cos dscp-list to cos
Configuring the DSCP-to-DSCP-Mutation Map
Show mls qos maps dscp-to-cos
36-67
Switch# show mls qos maps dscp-mutation mutation1
Switchconfig-if#mls qos dscp-mutation mutation1
36-68
36-69
Configuring Ingress Queue Characteristics
Mls qos srr-queue input cos-map
Mls qos srr-queue input dscp-map
Mls qos srr-queue input threshold
Show mls qos maps
Allocating Bandwidth Between the Ingress Queues
Allocating Buffer Space Between the Ingress Queues
Mls qos srr-queue input buffers
Show mls qos interface buffer
Weight1 weight2
Configuring the Ingress Priority Queue
Mls qos srr-queue input bandwidth
Show mls qos interface queueing
Weight
Configuring Egress Queue Characteristics
Mls qos srr-queue input
Priority-queue queue-id bandwidth
36-74
Queue-set qset-id
Mls qos queue-set output qset-id
36-75
36-76
Mls qos srr-queue output cos-map
Mls qos srr-queue output dscp-map
36-77
Srr-queue bandwidth shape weight1
Configuring SRR Shaped Weights on Egress Queues
Weight2 weight3 weight4
Queueing
Configuring the Egress Expedite Queue
Configuring SRR Shared Weights on Egress Queues
Srr-queue bandwidth share weight1
36-79
Srr-queue bandwidth limit weight1
Mls qos Enable QoS on a switch
Limiting the Bandwidth on an Egress Interface
36-80
36-81
Displaying Standard QoS Information
36-82
Show running-config include rewrite
Understanding EtherChannels
Configuring EtherChannels and Link-State Tracking
37-1
37-2
EtherChannel Overview
37-3
Single-Switch EtherChannel
37-4
Port-Channel Interfaces
37-5
Port Aggregation Protocol
Mode Description
PAgP Interaction with Other Features
PAgP Modes
Auto
Link Aggregation Control Protocol
Lacp Interaction with Other Features
Lacp Modes
37-7
Load-Balancing and Forwarding Methods
EtherChannel On Mode
37-8
37-9
37-10
EtherChannel and Switch Stacks
Default EtherChannel Configuration
Configuring EtherChannels
37-11
37-12
EtherChannel Configuration Guidelines
37-13
Configuring Layer 2 EtherChannels
Active passive
Auto non-silent desirable non-silent on
37-14
Switchconfig-if-range#channel-group 5 mode active
Configuring Layer 3 EtherChannels
Creating Port-Channel Logical Interfaces
37-15
Interface port-channel port-channel-number
Configuring the Physical Interfaces
Show etherchannel channel-group-number detail
No ip address
For channel-group-number, the range is 1 to 48. This number
Partner that is PAgP capable, configure the switch port for
Must be the same as the port-channel-number logical port
37-17
Port-channel load-balance dst-ip dst-mac
Configuring EtherChannel Load-Balancing
Src-dst-ip src-dst-mac src-ip src-mac
37-18
Show etherchannel load-balance Verify your entries
Configuring the PAgP Learn Method and Priority
37-19
Pagp learn-method physical-port
Configuring Lacp Hot-Standby Ports
Pagp port-priority priority
Show pagp channel-group-number internal
Show running-config Verify your entries Show lacp sys-id
Configuring the Lacp System Priority
37-21
Lacp port-priority priority
Configuring the Lacp Port Priority
Show lacp channel-group-number
Internal
Understanding Link-State Tracking
Displaying EtherChannel, PAgP, and Lacp Status
37-23
37-24
37-25
Configuring Link-State Tracking
Link-State Tracking Configuration Guidelines
Default Link-State Tracking Configuration
Configuring Link-State Tracking
37-26
Switch show link state group detail
Switch show link state group
Displaying Link-State Tracking Status
37-27
37-28
38-1
Configuring IP Unicast Routing
Types of Routing
Understanding IP Routing
38-2
38-3
IP Routing and Switch Stacks
38-4
Configuring IP Addressing
Steps for Configuring Routing
38-5
ARP
Default Addressing Configuration
Irdp
38-6
Assigning IP Addresses to Network Interfaces
Show running-config Verify your entry
Use of Subnet Zero
38-7
38-8
Classless Routing
No ip classless Disable classless routing behavior
Configuring Address Resolution Methods
38-9
Arp ip-address hardware-address type
Define a Static ARP Cache
38-10
38-11
Set ARP Encapsulation
Enable Proxy ARP
Routing Assistance When IP Routing is Disabled
Default Gateway
Proxy ARP
38-13
Icmp Router Discovery Protocol Irdp
38-14
Configuring Broadcast Packet Handling
Ip forward-protocol udp port nd sdns
Ip directed-broadcast access-list-number
38-15
38-16
Forwarding UDP Broadcast Packets and Protocols
Flooding IP Broadcasts
Establishing an IP Broadcast Address
Ip broadcast-address ip-address
38-17
Clear arp-cache
Monitoring and Maintaining IP Addressing
Clear host name
Clear ip route network mask
38-19
Enabling IP Unicast Routing
38-20
Configuring RIP
Configuring Basic RIP Parameters
Default RIP Configuration
Router rip
Network network number
38-22
Configuring Summary Addresses and Split Horizon
Configuring RIP Authentication
Ip rip authentication key-chain name-of-chain
Ip rip authentication mode text md5
Switchconfig-router#neighbor 2.2.2.2 peer-group mygroup
Configuring Split Horizon
Ip summary-address rip ip address ip-network mask
No ip split horizon
No ip split-horizon
Configuring Ospf
38-25
38-26
Default Ospf Configuration
38-27
Ospf Nonstop Forwarding
38-28
Ospf NSF Awareness
Configuring Ospf Interfaces
Configuring Basic Ospf Parameters
38-29
38-30
38-31
Configuring Ospf Area Parameters
38-32
Configuring Other Ospf Parameters
38-33
Changing LSA Group Pacing
Configuring a Loopback Interface
Ip address address mask
38-34
Monitoring Ospf
Configuring Eigrp
38-35
38-36
38-37
Default Eigrp Configuration
38-38
Eigrp Nonstop Forwarding
Router eigrp autonomous-system
Configuring Basic Eigrp Parameters
Network network-number
Eigrp log-neighbor-changes
No auto-summary
Configuring Eigrp Interfaces
Ip summary-address eigrp
38-40
Ip hello-interval eigrp autonomous-system-number
Configuring Eigrp Route Authentication
No ip split-horizon eigrp autonomous-system-number
Show ip eigrp interface
38-42
Eigrp Stub Routing
Monitoring and Maintaining Eigrp
Configuring BGP
38-43
EBGP, IBGP, and Multiple Autonomous Systems
38-44
38-45
Default BGP Configuration
38-46
38-47
Nonstop Forwarding Awareness
Router bgp autonomous-system
Enabling BGP Routing
Network network-number mask network-mask
Route-map route-map-name
38-49
Switch# show ip bgp neighbors
Switchconfig-router#neighbor 192.208.10.2 remote-as
Managing Routing Policy Changes
38-50
Show ip bgp neighbors
Type of Reset Advantages Disadvantages
Clear ip bgp * address
Show ip bgp
38-52
Configuring BGP Decision Attributes
38-53
Configuring BGP Filtering by Neighbor
Configuring BGP Filtering with Route Maps
38-54
Out weight weight
Ip as-path access-list access-list-number
Route-map map-tag in out
Show ip bgp neighbors paths
38-56
Configuring Prefix Lists for BGP Filtering
Ip community-listcommunity-list-number
Configuring BGP Community Filtering
Permit deny community-number
Send-community
Set comm-list list-num delete
Configuring BGP Neighbors and Peer Groups
Ip bgp-community new-format
Show ip bgp community
38-59
38-60
Configuring Aggregate Addresses
Configuring BGP Route Reflectors
Configuring Routing Domain Confederations
38-61
Route-reflector-client
Configuring Route Dampening
Bgp cluster-id cluster-id
No bgp client-to-client reflection
38-63
Monitoring and Maintaining BGP
38-64
Configuring Multi-VRF CE
38-65
Understanding Multi-VRF CE
38-66
Multi-VRF CE Configuration Guidelines
Default Multi-VRF CE Configuration
VRF
38-67
Route-target export import both
Configuring VRFs
Import map route-map
Ip vrf forwarding vrf-name
Show ip vrf brief detail interfaces
Configuring a VPN Routing Session
Log-adjacency-changes
Redistribute bgp
Multi-VRF CE Configuration Example
Configuring BGP PE to CE Routing Sessions
38-70
VPN2 CE1
38-71
38-72
Configuring Switch a
Switchconfig-router-af#network 8.8.1.0 mask
Switchconfig-router-af#network 8.8.2.0 mask
Switchconfig-if#ip address 208.0.0.20
38-73
38-74
Router# configure terminal
Displaying Multi-VRF CE Status
Configuring Unicast Reverse Path Forwarding
38-75
Configuring Distributed Cisco Express Forwarding
Configuring Protocol-Independent Features
38-76
38-77
Configuring the Number of Equal-Cost Routing Paths
Router bgp rip ospf eigrp
Configuring Static Unicast Routes
Maximum-paths maximum
Show ip route
Route Source Default Distance
Specifying Default Routes and Networks
Ip default-network network number Specify a default network
38-79
38-80
Using Route Maps to Redistribute Routing Information
38-81
38-82
38-83
Configuring Policy-Based Routing
38-84
PBR Configuration Guidelines
38-85
Enabling PBR
Ip route-cache policy
Ip policy route-map map-tag
Ip local policy route-map map-tag
38-86
Filtering Routing Information
Setting Passive Interfaces
38-87
Filtering Sources of Routing Information
Controlling Advertising and Processing in Routing Updates
Router bgp rip eigrp
38-88
Distance weight ip-address ip-address mask
Managing Authentication Keys
Ip access list
38-89
38-90
Monitoring and Maintaining the IP Network
38-91
38-92
Understanding IPv6
Configuring IPv6 Unicast Routing
39-1
39-2
IPv6 Addresses
Bit Wide Unicast Addresses
Supported IPv6 Unicast Routing Features
39-3
Path MTU Discovery for IPv6 Unicast
DNS for IPv6
ICMPv6
Neighbor Discovery
39-5
IPv6 Applications
Dual IPv4 and IPv6 Protocol Stacks
Unsupported IPv6 Unicast Routing Features
39-6
Limitations
IPv6 and Switch Stacks
39-7
39-8
Dual IPv4-and IPv6 SDM Templates
SDM Templates
39-9
39-10
Configuring IPv6
Configuring IPv6 Addressing and Enabling IPv6 Routing
Default IPv6 Configuration
39-11
39-12
Ip routing Enable routing on the switch
Configuring IPv4 and IPv6 Protocol Stacks
Switchconfig-if#ipv6 address 20010DB8c181/64 eui
39-13
39-14
Configuring CEF and dCEF for IPv6
Configuring IPv6 Icmp Rate Limiting
Ipv6 icmp error-interval interval bucketsize
Show ipv6 interface interface-id
39-16
Configuring Static Routing for IPv6
Ipv6 route ipv6-prefix/prefix length
Administrative distance
Ipv6-address interface-id ipv6-address
39-17
Show ipv6 route static updated
Configuring RIP for IPv6
Show ipv6 static ipv6-address
Interface-id recursive detail
39-19
39-20
Configuring Ospf for IPv6
39-21
Displaying IPv6
Switch# show ipv6 interface
39-22
Switch# show ipv6 protocols
Switch# show ipv6 cef /0
Switch# show ipv6 rip
39-23
Switch# show ipv6 static
Switch# show ipv6 neighbors
Switch# show ipv6 route
Switch# show ipv6 traffic
39-25
39-26
Understanding Hsrp
Configuring Hsrp and Enhanced Object Tracking
40-1
40-2
40-3
Multiple Hsrp
Hsrp and Switch Stacks
Configuring Hsrp
40-4
Hsrp Configuration Guidelines
Default Hsrp Configuration
Enabling Hsrp
40-5
Standby group-number ip ip-address
Switch# show standby
Secondary
Show standby interface-id group
40-7
Configuring Hsrp Priority
Standby group-number priority
Priority preempt delay delay
Standby group-number track
40-8
Configuring Hsrp Authentication and Timers
Configuring Mhsrp
Switchconfig-if#standby 2 ip
40-9
Standby group-number timers hellotime
Standby group-number authentication string
Switchconfig-if#standby 1 authentication word
Holdtime
Configuring Hsrp Groups and Clustering
Displaying Hsrp Configurations
Enabling Hsrp Support for Icmp Redirect Messages
Show standby interface-idgroup brief detail
Understanding Enhanced Object Tracking
Configuring Enhanced Object Tracking
40-12
Tracking Interface Line-Protocol or IP Routing State
Configuring Enhanced Object Tracking Features
Track object-number interface
40-13
Switch# show track 33 Track
Configuring a Tracked List
Track track-numberlist boolean
Object object-number not
Threshold weight up number
Weight
Track track-numberlist threshold
40-15
Percentage
Track track-number list threshold
Object object-number
Threshold percentage up number
40-17
Configuring Hsrp Object Tracking
Show standby
Configuring Other Tracking Characteristics
40-18
Understanding Wccp
Configuring Web Cache Services By Using
41-1
41-2
Wccp Message Exchange
Wccp Negotiation
Packet Redirection and Service Groups
MD5 Security
41-3
41-4
Wccp and Switch Stacks
Unsupported Wccp Features
Configuring Wccp
Default Wccp Configuration
Wccp Configuration Guidelines
41-6
Enabling the Web Cache Service
41-7
41-8
Switchconfig-if-range#switchport access vlan
Switchconfig# interface range gigabitethernet1/0/3
Monitoring and Maintaining Wccp
41-9
41-10
Enabled / disabled
42-1
Configuring IP Multicast Routing
IP Multicast Routing Protocols
42-2
Igmp Version
Understanding Igmp
42-3
PIM Versions
Understanding PIM
PIM Modes
42-4
42-5
PIM Stub Routing
42-6
Auto-RP
Multicast Forwarding and Reverse Path Check
Bootstrap Router
42-7
Network Port
Understanding Dvmrp
42-8
Understanding Cgmp
Multicast Routing and Switch Stacks
42-9
Default Multicast Routing Configuration
Configuring IP Multicast Routing
Multicast Routing Configuration Guidelines
42-10
PIMv1 and PIMv2 Interoperability
Auto-RP and BSR Configuration Guidelines
42-11
Ip multicast-routing distributed
Configuring Basic Multicast Routing
42-12
Ip pim version 1
Configuring PIM Stub Routing
Ip pim dense-mode sparse-mode
Sparse-dense-mode
Manually Assigning an RP to Multicast Groups
Configuring a Rendezvous Point
Ip pim passive
42-14
Ip pim rp-address ip-address
Access-list-number override
42-15
42-16
Configuring Auto-RP
Ip pim send-rp-announce interface-id
Scope ttl group-list access-list-number
Interval seconds
42-17
Show ip pim rp mapping
Ip pim send-rp-discovery scope ttl
Show ip pim rp
42-18
Ip pim rp-announce-filter rp-list
Access-list-number group-list
42-19
Ip pim bsr-border
Configuring PIMv2 BSR
42-20
42-21
Ip multicast boundary
Hash-mask-length priority
Ip pim bsr-candidate interface-id
42-22
Ip pim rp-candidate interface-id
Group-list access-list-number
42-23
Show ip pim rp group-name
Using Auto-RP and a BSR
Group-address mapping
Show ip pim rp-hash group
Troubleshooting PIMv1 and PIMv2 Interoperability Problems
Configuring Advanced PIM Features
Monitoring the RP Mapping Information
Understanding PIM Shared Tree and Source Tree
Shared Tree and Source Tree Shortest-Path Tree
42-26
Ip pim spt-threshold kbps infinity
Delaying the Use of PIM Shortest-Path Tree
42-27
Modifying the PIM Router-Query Message Interval
Configuring Optional Igmp Features
Ip pim query-interval seconds
Show ip igmp interface interface-id
Configuring the Switch as a Member of a Group
Default Igmp Configuration
Ip igmp join-group group-address
42-29
Ip igmp access-group access-list-number
Controlling Access to IP Multicast Groups
Show ip igmp interface interface-id Verify your entries
42-30
Modifying the Igmp Host-Query Message Interval
Changing the Igmp Version
Ip igmp version 1
Query-interval or the ip igmp query-max-response-time
Ip igmp querier-timeout seconds
Changing the Igmp Query Timeout for IGMPv2
Ip igmp query-interval seconds
42-32
Changing the Maximum Query Response Time for IGMPv2
Configuring the Switch as a Statically Connected Member
Ip igmp query-max-response-time
42-33
Enabling Cgmp Server Support
Configuring Optional Multicast Routing Features
Ip igmp static-group group-address
42-34
Ip cgmp proxy
Configuring sdr Listener Support
42-35
Enabling sdr Listener Support
Ip sdr listen Enable sdr listener support
Limiting How Long an sdr Cache Entry Exists
42-36
42-37
Configuring an IP Multicast Boundary
42-38
Configuring Basic Dvmrp Interoperability Features
42-39
Configuring Dvmrp Interoperability
42-40
Ip dvmrp metric metric list
42-41
Configuring a Dvmrp Tunnel
Neighbor-list access-list-number
Access-list-number distance
Advertising Network 0.0.0.0 to Dvmrp Neighbors
Ip dvmrp accept-filter
Ip dvmrp default-information
Configuring Advanced Dvmrp Interoperability Features
Responding to mrinfo Requests
Originate only
42-44
Enabling Dvmrp Unicast Routing
42-45
Rejecting a Dvmrp Nonpruning Neighbor
42-46
Enter interface configuration mode
Controlling Route Exchanges
By default, 7000 routes are advertised. The range is 0 to
Limiting the Number of Dvmrp Routes Advertised
Changing the Dvmrp Route Threshold
Default is 10,000 routes. The range is 1 to
Configuring a Dvmrp Summary Address
Route-count
42-48
42-49
Ip dvmrp summary-address address
Disabling Dvmrp Autosummarization
Mask metric value
No ip dvmrp auto-summary
Ip dvmrp metric-offset in out
Adding a Metric Offset to the Dvmrp Route
Increment
42-51
Clearing Caches, Tables, and Databases
Monitoring and Maintaining IP Multicast Routing
Displaying System and Network Statistics
42-52
42-53
Monitoring IP Multicast Routing
42-54
Understanding Msdp
Configuring Msdp
43-1
43-2
Msdp Operation
43-3
Msdp Benefits
Default Msdp Configuration
Configuring Msdp
Configuring a Default Msdp Peer
43-4
Prefix-list list
Ip msdp default-peer ip-address name
43-5
Ip prefix-list name description string
Caching Source-Active State
Seq number permit deny network
Ip msdp description peer-name
43-7
Ip msdp cache-sa-state list
Requesting Source Information from an Msdp Peer
Switchconfig# ip msdp sa-request
Ip msdp sa-request ip-address name
43-8
Redistributing Sources
Controlling Source Information that Your Switch Originates
Ip msdp redistribute list
43-9
43-10
Filtering Source-Active Request Messages
Name list access-list-number
Ip msdp filter-sa-request ip-address
43-11
Using a Filter
Controlling Source Information that Your Switch Forwards
Ip msdp sa-filter out ip-address name
Route-map map-tag
43-13
Using TTL to Limit the Multicast Data Sent in SA Messages
Controlling Source Information that Your Switch Receives
Ip msdp ttl-threshold ip-address name
Ttl
Ip msdp sa-filter in ip-address name
Switchconfig# ip msdp sa-filter in switch.cisco.com
43-15
Shutting Down an Msdp Peer
Configuring an Msdp Mesh Group
Ip msdp mesh-group name ip-address
43-16
Ip msdp shutdown peer-name peer
Including a Bordering PIM Dense-Mode Region in Msdp
Ip msdp border sa-address interface-id
43-17
43-18
Configuring an Originating Address other than the RP Address
Clear ip msdp peer peer-addressname
Monitoring and Maintaining Msdp
Clear ip msdp statistics peer-addressname
Clear ip msdp sa-cache group-addressname
43-20
Understanding Fallback Bridging
Configuring Fallback Bridging
Fallback Bridging Overview
44-1
44-2
Fallback Bridging and Switch Stacks
Configuring Fallback Bridging
44-3
Fallback Bridging Configuration Guidelines
Default Fallback Bridging Configuration
Creating a Bridge Group
44-4
Vlan-bridge
Bridge bridge-group protocol
Bridge-group bridge-group
44-5
Switchconfig# bridge 10 protocol vlan-bridge
Adjusting Spanning-Tree Parameters
44-6
Changing the Interface Priority
Changing the VLAN-Bridge Spanning-Tree Priority
Bridge bridge-group priority number
Bridge-group bridge-grouppriority
Bridge-group bridge-group path-cost
Assigning a Path Cost
Cost
44-8
Switchconfig# bridge 10 hello-time
Adjusting Bpdu Intervals
Bridge bridge-group hello-time seconds
44-9
Switchconfig# bridge 10 max-age
Switchconfig# bridge 10 forward-time
Bridge bridge-group forward-time
Bridge bridge-group max-age seconds
Disabling the Spanning Tree on an Interface
Monitoring and Maintaining Fallback Bridging
Clear bridge bridge-group
Show bridge bridge-group group
44-12
45-1
Troubleshooting
45-2
Recovering from a Software Failure
Switch flashinit
Recovering from a Lost or Forgotten Password
Switch loadhelper
Switch copy xmodem flashimagefilename.bin
45-4
45-5
Procedure with Password Recovery Enabled
45-6
Copy the configuration file into memory
Switch dir flash
Procedure with Password Recovery Disabled
45-7
45-8
Preventing Switch Stack Problems
45-9
Recovering from a Command Switch Failure
Switchconfig# no cluster commander-address
Replacing a Failed Command Switch with a Cluster Member
45-10
45-11
Replacing a Failed Command Switch with Another Switch
45-12
Troubleshooting Power over Ethernet Switch Ports
Recovering from Lost Cluster Member Connectivity
Preventing Autonegotiation Mismatches
45-13
Disabled Port Caused by False Link Up
Disabled Port Caused by Power Loss
Show controllers power inline privileged Exec command
SFP Module Security and Identification
Using Ping
Monitoring Temperature
Monitoring SFP Module Status
Understanding Ping
Executing Ping
Switch# ping
Character Description
45-16
Understanding Layer 2 Traceroute
Using Layer 2 Traceroute
Usage Guidelines
45-17
Displaying the Physical Path
Using IP Traceroute
Understanding IP Traceroute
45-18
Executing IP Traceroute
Switch# traceroute ip
Traceroute ip host
Trace the path that packets take through the network
Understanding TDR
Using TDR
45-20
Enabling Debugging on a Specific Feature
Using Debug Commands
Running TDR and Displaying the Results
45-21
Redirecting Debug and Error Message Output
Enabling All-System Diagnostics
45-22
45-23
Using the show platform forward Command
Udp 10
45-24
Basic crashinfo Files
Using the crashinfo Files
45-25
Extended crashinfo Files
Using On-Board Failure Logging
Understanding Obfl
45-26
45-27
Configuring Obfl
Show logging onboard module
Displaying Obfl Information
45-28
Understanding Online Diagnostics
Configuring Online Diagnostics
46-1
Scheduling Online Diagnostics
Configuring Online Diagnostics
Diagnostic schedule switch
Non-disruptive daily hhmm
Diagnostic monitor interval switch
Configuring Health-Monitoring Diagnostics
Diagnostic content command output
Diagnostic monitor syslog
Diagnostic monitor switch number test
Diagnostic monitor threshold switch
Show diagnostic content post result
Schedule status switch
Starting Online Diagnostic Tests
Running Online Diagnostic Tests
Diagnostic start switch number
All basic non-disruptive
46-6
Displaying Online Diagnostic Tests and Test Results
MIB List
Supported MIBs
CISCO-FTP-CLIENT-MIB CISCO-HSRP-MIB
CISCO-RTTMON-MIB CISCO-SMI-MIB
CISCO-IGMP-FILTER-MIB
ETHERLIKE-MIB IEEE8021-PAE-MIB IEEE8023-LAG-MIB
IGMP-MIB INET-ADDRESS-MIB IPMROUTE-MIB
TCP-MIB UDP-MIB
Using FTP to Access the MIB Files
Working with the Flash File System
Displaying Available File Systems
Switch# show file systems
Field Value
Setting the Default File System
Displaying Information about Files on a File System
Cd newconfigs
Changing Directories and Displaying the Working Directory
Pwd
Creating and Removing Directories
Mkdir oldconfigs
Copying Files
Deleting Files
Switch# delete myconfig
Creating, Displaying, and Extracting Files
Flash
Archive /create destination-url
Archive /table source-url
Extract a file into a directory on the flash file system
Archive /xtract source-url
Directories are extracted
More /ascii /binary /ebcdic
Working with Configuration Files
Configuration File Types and Location
Guidelines for Creating and Using Configuration Files
Copying Configuration Files By Using Tftp
Creating a Configuration File By Using a Text Editor
Uploading the Configuration File By Using Tftp
Downloading the Configuration File By Using Tftp
Copying Configuration Files By Using FTP
Ip ftp password password
Downloading a Configuration File By Using FTP
Ip ftp username username
Ftp // username password @ location /directory
Uploading a Configuration File By Using FTP
Filename systemrunning-config
Filename nvramstartup-config
Copy systemrunning-config
Copying Configuration Files By Using RCP
Copy nvramstartup-config
Ftp // username password @ location /directory Filename
Hostname Switch1 Ip rcmd remote-username User0
Systemrunning-config
Downloading a Configuration File By Using RCP
Nvramstartup-config
Ip rcmd remote-username username
Uploading a Configuration File By Using RCP
Clearing Configuration Information
Switch# copy nvramstartup-config rcp
Deleting a Stored Configuration File
Clearing the Startup Configuration File
Working with Software Images
File Format of Images on a Server or Cisco.com
Image Location on the Switch
Field Description
Copying Image Files By Using Tftp
Downloading an Image File By Using Tftp
Preparing to Download or Upload an Image File By Using Tftp
Archive download-sw
Allow-feature-upgrade /directory
Overwrite /reload
Archive download-sw /directory
Archive upload-sw
Uploading an Image File By Using Tftp
Tftp //location /directory /image-name .tar
Preparing to Download or Upload an Image File By Using FTP
Copying Image Files By Using FTP
Downloading an Image File By Using FTP
Directory /overwrite /reload
Archive download-sw /allow-feature-upgrade
For /directory /image-name1 .tar
Directory /image-name2 .tar image-name3 .tar
Uploading an Image File By Using FTP
Copying Image Files By Using RCP
Preparing to Download or Upload an Image File By Using RCP
File By Using RCP section on page B-31
Downloading an Image File By Using RCP
Or Upload an Image File By Using RCP section on
Uploading an Image File By Using RCP
Rcp // username @ location /directory /image-na
Copying an Image File from One Stack Member to Another
Me.tar
Destination-stack-member-number /force-reload
Archive copy-sw /destination-system
Source-stack-member-number
For /destination-system destination-stack-member-number
Access Control Lists
Unsupported Commands Cisco IOS Release 12.237SE
Unsupported Privileged Exec Commands
Unsupported Global Configuration Commands
ARP Commands
Archive Commands
Boot Loader Commands
Debug Commands
Bridge bridge-groupacquire
Fallback Bridging
Bridge crb
Bridge bridge-group domain domain-name bridge irb
X25 map bridge x.121-address broadcast options-keywords
Hsrp
Interface Commands
Igmp Snooping Commands
IP Multicast Routing
Show ip pim vc group-address name type number
Ip pim accept-rpaddress auto-rpgroup-access-list-number
Show ip rtp header-compression type number detail
Ip multicast-routing vrf vrf-name
IP Unicast Routing
Unsupported Privileged Exec or User Exec Commands
Unsupported VPN Configuration Commands
Unsupported BGP Router Configuration Commands
Unsupported Route Map Commands
Show cable-diagnostics prbs Test cable-diagnostics prbs
MAC Address Commands
Miscellaneous
Set tag tag-value
Msdp
NetFlow Commands
Unsupported Global Configuration Command
Network Address Translation NAT Commands
Unsupported Policy-Map Configuration Command
QoS
Unsupported User Exec Commands
Unsupported Interface Configuration Command
Unsupported Privileged Exec Command
Spanning Tree
IN-1
Numerics
IN-2
ACLs
Eigrp
CDP Lldp RIP
Hsrp
TACACS+
Cidr
BGP
IN-4
IN-5
Bpdu
CEF
CDP
Cgmp
CLI
IN-7
CNS
IN-8
DNS
Dhcp
IN-9
TACACS+ Udld
Snmp
Vmps
Wccp
IN-11
Dhcp option
IN-12
DTP
IN-13
Dvmrp
IN-14
Dynamic ARP inspection
IN-15
Lacp
FIB
STP
IN-16
FTP
Mstp STP
IN-17
Icmp
Https
IN-18
IN-19
Igmp
IN-20
IN-21
IP addresses
IN-22
Mbone
IN-23
IGP
IN-24
IP unicast routing
IN-25
ISL
IN-26
LLDP-MED
IN-27
Mhsrp
MDA
IN-28
IN-29
Msdp
IST
CST
MTU
IN-30
IN-31
NAC
IN-32
NSSA, Ospf
PBR
Obfl
IN-33
IN-34
PIM
IN-35
Port-based authentication
Vvid
Pvid
IN-36
IN-37
Private VLANs
IN-38
QoS
IN-39
IN-40
RCP
RFC
Radius TACACS+
Rmon
IN-41
Rspan
RPS
Rstp
IN-42
IN-43
SDM
IN-44
Snmp
SRR
Span
IN-45
VTP
SSL
IN-46
IN-47
Stacks, switch
IN-48
LLDP-MED Ospf
IN-49
STP
IN-50
IN-51
System message logging
IN-52
IN-53
IN-54
IN-55
VLANs
VQP
VPN
IN-56
IN-57
WTD
IN-58