RiverMaster Administrator’s Guide
Office
Table of Contents
Configuring an ANG-3000/7000
Setting Up Aurorean Services
Managing Users & Groups
Adding POPs for Corporate ISPs 114
Generating Reports
Index
Contents of the Guide
About This Guide
About This Guide
Conventions Used in this Guide
Related Documents
Xii
System Requirements
Hardware Requirements
Installing the Application
Installation Steps
Software Requirements
Upgrading a Previous Release
When the Welcome window appears, click Next to continue
Installing the Application
Starting the Application for the First Time
First-Time Setup Information
To start RiverMaster, perform the following steps
Do one of the following
Select APS Window
RiverMaster Login Window
RiverMaster Main Interface
Removing RiverMaster Files
Removing RiverMaster Files
Delete the RiverMaster folder Restart your computer
Default location for this folder is C\Program Files\
Locate the RiverMaster program folder
Getting Started with RiverMaster
RiverMaster Overview
Curre
Logging into RiverMaster
Logging into RiverMaster
Logging into RiverMaster
Checking Server Status
Problem Summary & Users Logged
Checking Server Status
Aurorean Network Gateway Statistics
Aurorean Network Gateway Status Information
Aurorean Policy Server Statistics
Aurorean Network Gateway Statistics
Aurorean Policy Server Services
Service Function If Stopped
FTP
Aurorean Policy Server Services
Setting Up a Aurorean Virtual Network the First Time
Setting Up a Aurorean Virtual Network the First Time
Add user accounts to each group as described in Chapter
Setting Up a Aurorean Virtual Network the First Time
Page
Configuring an ANG-3000/7000
Before You Begin
Configuration Pullout
Before You Begin
Allocating IP/IPX Addresses to Remote Clients
Before You Begin
Remote Client Virtual Subnet Usage
Configuring an ANG-3000/7000
Virtual Subnets for Site-to-Site and Remote Access Tunnels
Intelligent Client Routing
Intelligent Client Routing Disabled
Intelligent Client Routing Enabled
NAT Server
Aurorean
Network
Gateway
Site-to-Site Configuration
Site-to-Site Tunnels
AutoLink Recovery
Primary Aurorean System
General Aurorean Network Gateway Settings
General Aurorean Network Gateway Settings
General Aurorean Network Gateway Settings
Click the DNS tab
DNS server addresses tab page appears as shown in Figure
Click the Wins tab
Wins Server Addresses
Click the NAT tab
NAT Server Address
Viewing Aurorean Alternate Address Information
Click Apply to save your changes
Aurorean Alternate Address Info window appears as shown
Primary addresses cannot be modified in this window
Tunnel Protocols
Tunnel Protocols
Tunnel Protocol General Settings
Tunnel Protocols window appears as shown in Figure
Click the Authentication tab
Tunnel Protocol Authentication Settings
Click the Encryption tab Do one of the following
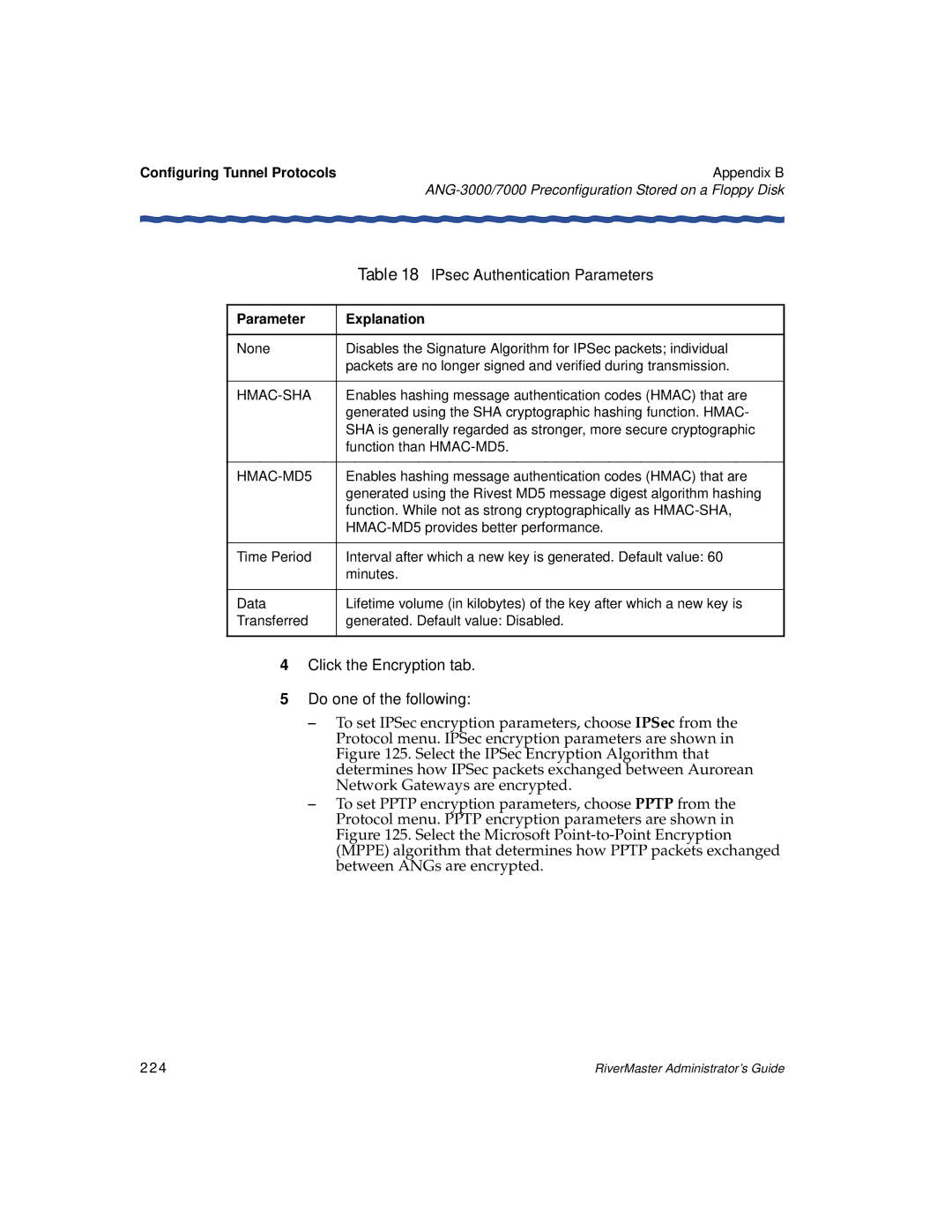
Parameter Explanation
Tunnel Protocol Encryption Settings
Click the Compression tab
Tunnel Parameter Explanation Protocol
Enable or disable Mppc as required
Tunnel Protocol Compression Settings
Virtual Subnetting
IP Subnetting
Sample IP subnet window is shown in Figure
Virtual Subnetting
Add An IP Virtual Subnet window appears as seen in Figure
Click Remove to delete any configured virtual subnets
Click Add
IPX Virtual Networks
Sample IPX virtual networks window is shown in Figure
IPX Subnet Configuration for Remote Clients
Routing
Routing
Setting Routing Protocol Parameters
RIP Configuration window should appear as shown in Figure
RIP Routing Protocol Configuration
Repeat and for each gateway required Do one of the following
Parameter Meaning Fixed Value
Ospf Configuration window appears as shown in Figure
Ospf Routing Protocol Configuration
Routing Interfaces
Adding or Removing a Routing Protocol for an Interface
Adding a Routing Protocol
RIP Interface Configuration window appears as shown
Choose the version of RIP to use on this interface
Do one of the following
To enable Ospf on an interface, perform the following steps
Ospf Interface Configuration window appears as shown
Do one of the following
Static parameter tab page is displayed as shown in Figure
Routing
Click Add
Adding a Remote Server
Remote Server Display
Click Add Remote Server
Add Remote Server window appears as shown in Figure
Adding a Remote Server
Choose the tunneling protocol IPSec or Pptp Click Add
Add Remote Tunnel window appears as shown in Figure
Select Enabled or Disabled in the Enabled State field
Changing Server and Tunnel Properties
Remote Tunnel Properties window appears as shown in Figure
Adding a Remote Server
Page
Setting Up Aurorean Services
Authorization Plug-in Options
Radius Authentication Servers
Plug-in Planning
Private/Public Keys for IPSec Authentication
Problem Notification
Trace Levels
Adding an Authorization Plug-In
Trace Messages Display
Enterasys Authentication
Shows the Configuration pullout
Click here to update the plug-in
Radius Authorization
Optionally, specify a value in the Num Threads field
Adding an Authorization Plug-In Chapter
Optionally, specify a value in the Num Threads field
Server Type Recommended Value
SecurID Authorization
Create New Plug-in window will appear as shown in Figure
Adding an Authorization Plug-In Chapter
Specify SecurID Configuration File Window
Click Create
Chapter
Generating Private/Public Keys
Chapter
Using the Notification Service to Send E-Mail
Creating a Mailing List
Chapter
Adding an Address to a Mailing List
Using the Notification Service to Send E-Mail Chapter
Setting Trace Levels
ANG Tunnel Management Service Window
Click Set to enable the Trace Level
Backing Up the Database
Click on Indus River Access
Starting a Database Backup Click Start on Backup Database
100
Window similar to will appear
Backing Up the Database
Controlling Remote User Dialing & Access
101
TollSaver Database
102
Corporate Dial-Up Access
103
Corporate
104
Creating POP Packages
105
Creating POP Packages
106
Build Completed Window
107
Adding Corporate ISPs
108
109
110
Click the ISP Properties tab
ISP Properties display will appear as show in Figure
111
Select the Access Method as follows
Script files are not uploaded without the .SCP extension
Adding Corporate ISPs
112
113
114
Adding POPs for Corporate ISPs
Adding POPs for Corporate ISPs
Pull-down options appear as shown in below
115
This field is currently not implemented
116
Script window appears as shown in Figure
117
Page
Managing Users & Groups
119
Manage Users & Groups Pullout
120
Group Policies
121
Aurorean Client Installation Kits
122
Contents of a Aurorean Client Installation Kit
123
Client Synchronization
124
125
126
Creating a New Group
Group Notices
Open the Manage Users and Groups pullout
Creating a New Group
Manage Users and Groups Pullout Group View
128
129
Policy Explanation
130
Password Policies
131
Credit Card Policies
132
Tunnel Policies
133
134
Adding Users to a Group
Sample User view is shown in Figure
Corporate User Name field, type a name for the user
135
136
Password field, type a unique password
Department field automatically defaults to the group name
Modifying User & Group Information
137
Removing Users & Groups
138
Creating an Aurorean Client Installation Kit
Creating an Aurorean Client Installation Kit
Sample Group view is shown in Figure
139
Build Client Install Kit Window
140
141
Default Aurorean installation kit file name is
Set the Install Kit Options as follows
Advanced Kit Options Window
142
143
Kit Complete Message
144
145
Controlling Client Synchronization
Controlling Client Synchronization
Viewing Group Policies
146
147
Open the Configuration pullout Click the Update tab
Building Core Data Files
Build Core Data Files Display
148
Uploading Software Synchronization Files
149
Upload Software Synchronization Files Display
150
Click Upload to copy the file you chose onto the APS
151
Setting Up Group Notices
Setting Up Group Notices
Group Notice display appears as shown in Figure
152
Chapter Managing Users & Groups
153
154
Click the arrow in the Group field and select a group
Group pull-down screen appears as shown in Figure
155
Write your notice in the text box
Message you write is limited to 256 characters. See Figure
Page
157
Monitoring System Activity
Current Message Activity
To view message activity, perform the following steps
Open the View System Activity pullout
Sample message activity view is shown in Figure
Monitoring System Activity
System Activity Display
159
160
Message ID Message Type Detailed Description
161
Text
162
Tunnelid
163
Advanced Message Viewer
164
Advanced Message View Setup Example
165
Message Type Explanation
166
167
Advanced Message Viewer Results Example
168
Printing Messages
169
170
RiverMaster Options
RiverMaster Options window displays as shown in Figure
RiverMaster Options Window
171
172
Viewing Tunnel Activity
Tunnel Statistics window appears similar to Figure
Viewing Tunnel Activity
173
174
Describes the types of statistics you can choose
Value Meaning Trends to Look For
175
Using Snmp to Gather Statistics
176
Report Contents
Generating Reports
178
Report Contents
Heading Explanation
Network Gateway Report
179
Network Gateway Report Values
180
Max Tunnels GRE/IPSEC Display
Network Gateway Report
Client Anomaly Report
182
Client Report
183
Client Session Report Values
184
Conn Speed
185
Displays a typical Client Session Summary Report
Client Session Summary Report
Accounting Report
187
Displays a typical Accounting Summary Report
188
Accounting Summary Report
Drill-down Accounting Detail Report
Downloading, Viewing and Exporting Reports
Choose from daily, weekly, monthly or custom options
Downloading, Viewing and Exporting Reports
190
191
Report Viewing Window
192
Printing Reports
193
Exporting Reports
Export window appears as shown in Figure
Select Disk file in the Destination field
194
If you want this export format Go to
195
Choose Export File Window
196
Exporting Records Window
197
Export To Directory window appears as shown in Figure
198
Number and Date Format Dialog box appears as shown
199
Enter Odbc Table Name dialog box appears as shown
200
Select Workbook Window
201
Lines Per Page Dialog Box
Format Options Dialog Box
Exporting Reports to a Microsoft Exchange Folder
203
Select Exchange Folder in the Destination field and click OK
Choose Profile Window
Select a folder window appears as shown in Figure
205
Click on a folder to store the report and click OK
206
Exporting Reports Using Mapi
207
208
Send Mail window appears as shown in Figure
Export is now complete
Glossary
209
AutoLink Recovery
210
Generic Routing Encapsulation GRE
211
Network Administrator
212
Point-to-Point Tunneling Protocol Pptp
213
Remote Client/User
214
TollSaver Database
215
Page
ANG-3000/7000 Preconfiguration Stored on a Floppy Disk
217
Adding Remote Gateways
Add Remote ANG window appears as shown in Figure
Adding Remote Gateways
218
Add Remote ANG Window
219
Configuring ANG IP Addresses
Under Remote Gateways, click Configure Remote Gateway
Remote ANG Configuration screen appears as shown in Figure
220
Configuring Tunnel Protocols
Enter values in the open fields as follows
Click Next
221
Configuring Tunnel Protocols
222
Click on the Authentication tab
223
Click the Encryption tab Do one of the following
224
225
226
Click the Compression tab
Compression properties screen appears as shown in Figure
Enable or disable Mppc as required
227
Configuring Virtual Subnets
228
229
230
Configuring Routing Protocols
Configuring Routing Protocols
231
Ospf Properties
232
233
234
Configuring Routing Interfaces
Configuring Routing Interfaces
235
Configuring RIP for the Interface
236
237
238
Configuring Ospf on an Interface
Set the RIP Route Importing/Exporting options as follows
Creating Static Routes
239
Appendix B
240
241
242
Creating Remote Connections
Creating Remote Connections
Remote Connection Configuration Window
243
Tunnel Values section, enter a User Name
244
245
246
247
Loading the Floppy Disk
Loading the Floppy Disk
Remove the floppy disk
248
249
Enterasys Networks License Agreement
License Grant
250
Warranty
AppendixC
Infringement Indemnification
Limitation of Liability
Appendix C
251
Termination
International Provisions
Applicable Law
252
Government Commercial Computer Software
253
Technical Support
Support from Authorized Resellers
Support from Enterasys Networks
254
255
Symbols
Numerics
Index
256
257
190-208
New
109
111
110
113
48, 224
259
Radius
260
203-206
261
UDP
262
263